
Updated February 12, 2019
Israeli hackers and activists Noam Rotem and Ran L from Safety Detectives research lab have uncovered a major security breach in temperature control systems manufactured by Resource Data Management, a Scotland-based remote monitoring solutions company.
These control systems are used by hospitals and supermarket chains all over the world, including Marks & Spencer, Ocado, Way-on, and many others.
A basic scan reveals hundreds of installations in the UK, Australia, Israel, Germany, the Netherlands, Malaysia, Iceland, and many other countries around the world. As each installation includes dozens of machines, we’re looking at many thousands of vulnerabilities.
This screenshot from Shodan’s search engine for internet-connected devices shows 7419 installations with vulnerabilities (correction: after further analysis Safety Detective now estimates there are hundreds of locations with thousands of machines affected (we confirmed 10,606 cases). Read full details and comments below.
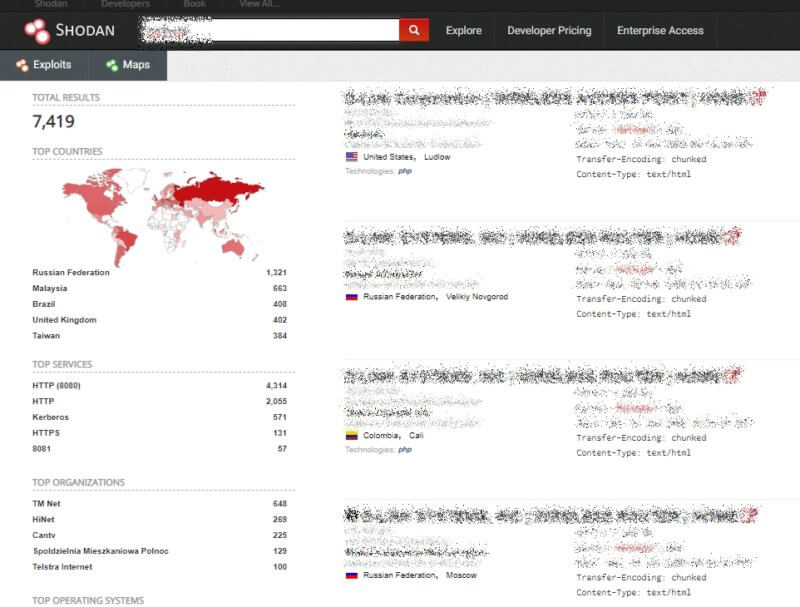
These systems all use the unsecured HTTP protocol and the 9000 port (or sometimes 8080, 8100, or even simply 80). They all come with a default username and “1234” as the default password, which is rarely changed by system administrators. All the screenshots taken in this report did not require entering usernames and passwords, but it came to our attention that almost all devices use the default password.
The systems can be accessed through any browser. All you need is the right URL, which as our tests show, isn’t too difficult to find. We won’t go into the specifics here, as it’s not our intention to encourage hacking systems that could literally put lives at risk; but all it takes is a simple Google search.
We instructed our office secretary on how to find other devices online, and she quickly found a cooling factory in Germany and a hospital in the UK, using only Google.
With Shodan, a potential attacker can identify thousands of devices.
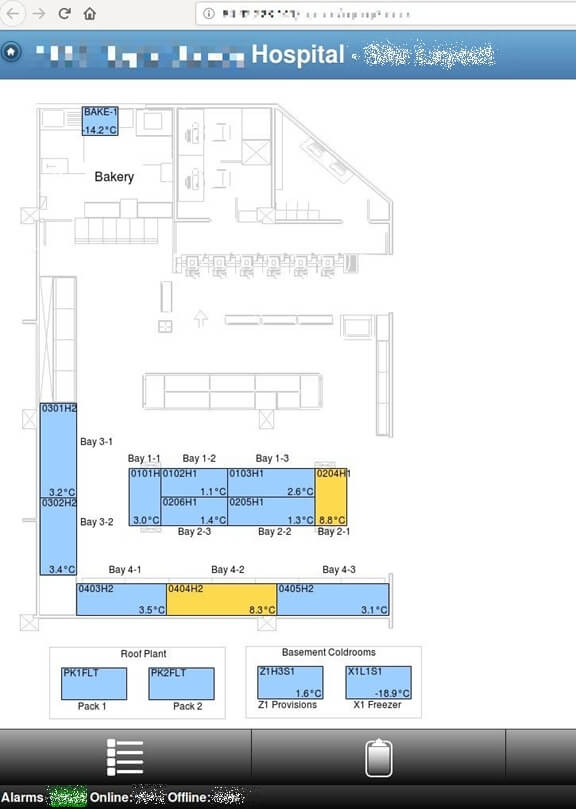
Here’s the site layout from a hospital in the UK:
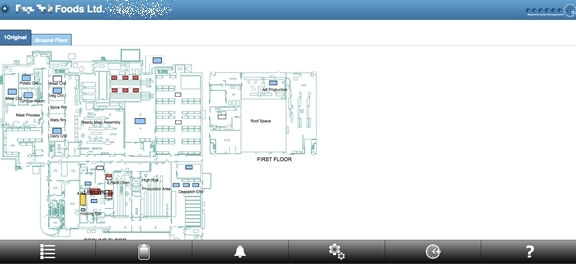
Here’s a similar layout page from a major supermarket:
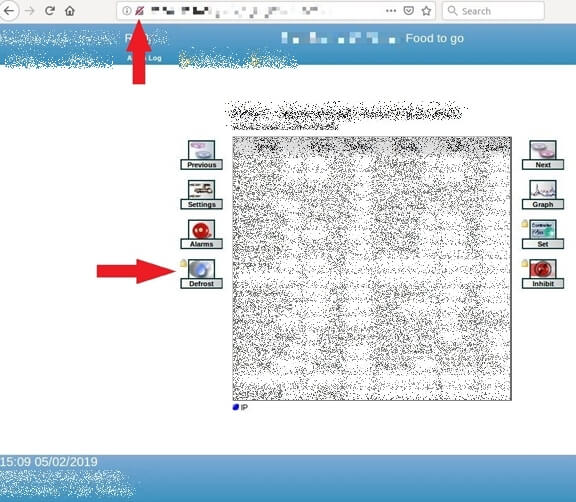
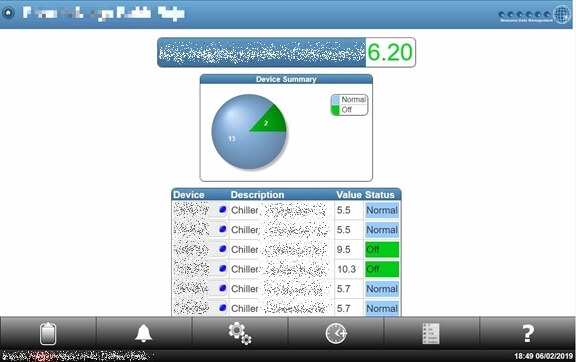
Below is detailed data on one of those machines – namely a display case at a large supermarket. Note how it’s accessible through an unsecured URL. To defrost this machine, all you’d need to do is click a button and enter the default username and password.
Here we were able to easily access the refrigeration system at Marks and Spencer Brooklands:
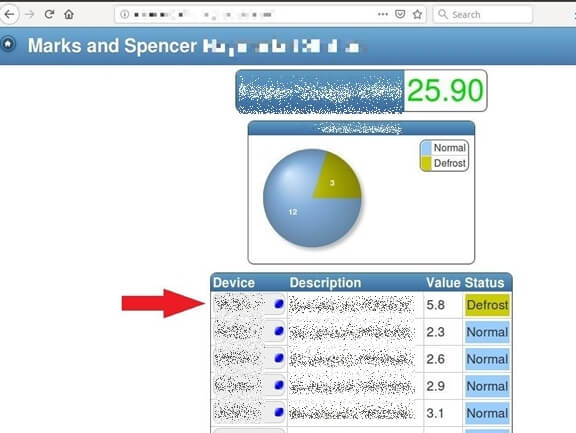
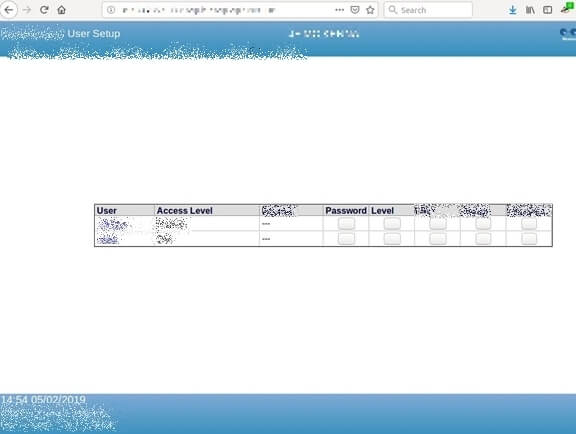
Not only were we able to change refrigerator and freezer settings through this system, we could also modify user settings, alarm settings, and more.
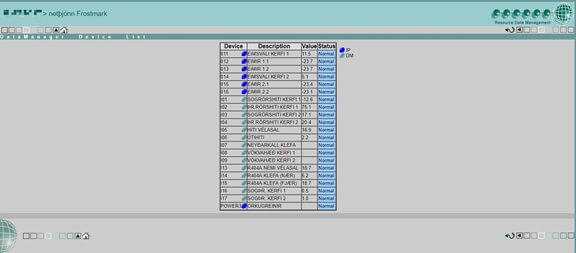
As previously mentioned, these systems are installed by companies in countries all over the world. Here we were able to access the refrigeration system of a food storage facility in Iceland:
Here we were able to access the system of the largest pharmaceutical company in Malaysia.
And the list goes on and on. Other potential victims of the security breach include:
- Menu Italiano, an Italian food manufacturer with locations in Italy, Denmark, Belgium, Sweden, Germany, and China
- Muenstermann Kuelhaus am Grossmarket Dueseldorf, a cooling facility in Germany
- CCM Duopharma Biotech Berhad, a pharmaceutical company from Selangor, Malaysia
In the era of the Internet of Things, system administrators need to take special care to secure their remote systems, and never rely on manufacturers’ default settings. This is particularly crucial when it literally becomes a matter of life and death, as illustrated in the above examples.
Response
We notified Resource Data Management of the severe vulnerability, while urging them to fix it ASAP and provided technical information and screenshot evidence that hackers can obtain their clients’ information. When they didn’t reply, we contacted them via twitter (without disclosing information on the nature of the vulnerability). We were amazed to receive the following official response from Resource Data Management by email:
Good Afternoon,
Thank you for your email and approach. Having looked at your services they are not of interest to our company.
As a senior team member within the company can I please ask you to refrain from contacting us any further, on any of individual or general email accounts. It would also be greatly appreciated if you could refrain from tagging us on posts on social media.
Thank you for your co-operation.
Update: we got another response from RDM
Update: we got a third response from RDM (February 11, 2019)
Updates and corrections to this report (February 11, 2019)
RDM clarified that there couldn’t be as many as 7000 installations, as we initially reported. In addition, several independent researchers reached out to let us know that the number of affected installations and refrigerators is lower than originally reported; claiming there were between 600-700 based on what seemed to be serious investigation.
As is quite common whenever we contact companies to inform them of a security breach, the initial reaction is usually denial, followed by questioning the validity of our research and how we calculated the numbers, thereby downplaying the problem. So when other researchers also pointed out problems with our original numbers, we thought it would be a good idea to go back and double check our preliminary research.
In a private communication with one researcher, we asked if they really expected us to check over 7000 URLs in order to count the number of refrigerators at each location. The researcher suggested that if verifying the validity of the claim was too much work, then maybe we were in the wrong business to begin with. So we decided to listen to our critics and do some rigorous fact checking in order to ensure the integrity of our research, and provide the correct, verified figures for the benefit of the public.
Our methodology
- We downloaded Shodan’s data on 7419 locations and opened a few dozen links. Many URLs are no longer available (hopefully due to an improvement in security by the refrigerator owners).
- We then looked at 2215 URLs that provided status code OK200.
- We found a pattern in the title tag on pages that were real sites, and not routers, and were able to screen 380 results.
- Then we carefully examined all 380 results and discovered that 319 are totally open locations with refrigerators accessible to anyone with a link, including 10 hospitals in the UK.
- We then took the first 24 URLs from the list, which seemed to be distributed randomly and included locations from the US, Malaysia, France, UK, New Zealand, Australia, Canada, Iceland, and Netherlands. We believe they represent a good sample of the 319 locations they came from.
- Lastly, we manually counted the number of refrigerators, cooling rooms, and freezers at each location. Of these 24 locations, there were a total of 798 machines, therefore the average worked out to 33.25 refrigerators per location.
Based on the above analysis, we can confirm that there are 319 locations, with an estimated 10,606 machines that are still accessible online as of this latest update (five days after we did the research and hopefully after many businesses already fixed the issue since February 12).
We want to remind our readers that Shodan doesn’t covert the entire internet. The fact that five days passed, and we were very conservative in our methodology in order to report the smallest possible number of vulnerabilities, means that we are confident the impact of the breach could have been much greater. However, we don’t think the important question is whether there are 7000, 8000, or even the revised estimate of 10,000 refrigerators accessible to hackers; but rather, why so many people thought that connecting the machines to the internet, while remaining accessible to anyone, didn’t raise any red flags.
We want to thank everyone who encouraged us to be more precise with our research, which allowed us to improve the findings of this report.
Past reports
You may also want to read about why we consider Kaspersky a virus, how to hack ethically, and a recently discovered major security breach affecting nearly half of all airlines worldwide.
Published on: Feb 7, 2019