
Led by Anurag Sen, the SafetyDetectives cybersecurity team identified a data exposure affecting the US payment software provider Transact Campus.
According to the company’s website, Transact Campus’ technology integrates several payment functions into a single mobile platform to power student purchases at higher education institutions.Transact Campus’ services streamline payment processes for students and institutions alike.
An Elasticsearch server containing data related to Transact Campus was left unsecured, without any password protection, and has therefore exposed over 1 million student records.
Who Is Transact Campus?
Transact Campus sells a campus payments technology to US higher education institutions that integrates mobile payments and user identification (with “Campus ID”) into a single app for students.
Students can make cashless payments on tuition fees and various other on-site privileges with their unique personal account (“Campus ID”), including event tickets and products from concession stands, vending machines, and third-party vendors.
Campus IDs can also be used to authorize student access to various other campus functions, such as printer access, door access, event access, and class attendance monitoring.
Transact Campus is headquartered in Phoenix, Arizona. Since the company was founded in 1984, Transact Campus has served 12 million students at 1,300 client institutions, facilitating $45 billion worth of transactions. Transact Campus currently employs around 400 people and generates an estimated annual revenue of US$100 million.
What was Exposed?
The open Elasticsearch server exposed over 1 million records, totaling more than 5 GB of data. The server was left accessible and its data was unencrypted.
The Elasticsearch’s logs contained data from various colleges that use Transact Campus’ services. This data belongs to students at these exposed institutions.
Several forms of student PII were exposed on the open server, including:
- Full names
- Email addresses
- Phone numbers
- Login credentials in plain text, incl. usernames and passwords
- Transaction details, incl. amount and time of purchase
- Credit card details (incomplete), incl. 6 first digits (BIN*) and last 4 digits of credit card numbers, expiry dates, and bank details
- Purchased meal plans and meal plan balances
*Note: A Bank Identification Number (BIN) is the first six digits of a payment card number. These numbers identify the card issuer.
The SafetyDetectives cybersecurity team found the open Elasticsearch server while checking IP addresses at a particular port. The server was live and being updated at the time of discovery.
You can see evidence of server logs that exposed student data in the following screenshots.
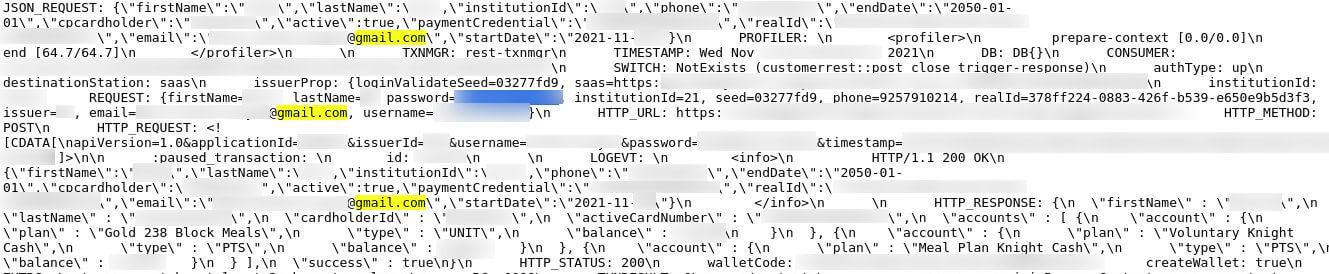
Log in details, wallet balances, and other PII in the server’s logs
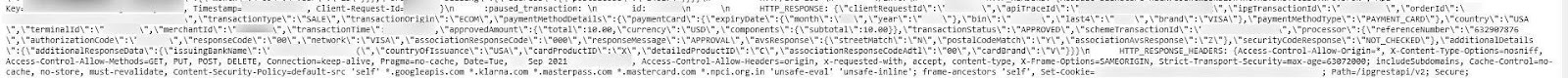
Transaction and payment details were exposed on the server too
The data exposure affects students who are Transact Campus account holders. Families could be affected, too. For example, a parent’s payment details could be exposed if they fund a student’s tuition fees or financially support a student through a Transact Campus account. Any person with an account and/or payment details linked to an account at one of the exposed colleges could be affected.
It’s impossible to know exactly how many people were exposed in this incident. However, the volume of email addresses and phone numbers exposed on the server suggests an estimated 30,000-40,000 students are affected.
Transact Campus deals with US higher education institutions and, as such, the exposed Elasticsearch primarily impacts US citizens.
You can see a full breakdown of this data exposure in the table below.
We discovered the open server on December 6th, 2021, and subsequently reached out to Transact Campus on December 8th, 2021.
We followed up our initial contact with Transact Campus on the 9th and 14th of December, 2021, but did not receive a reply. We emailed the US-CERT on January 9th, 2022, and sent follow-up messages to some key contacts on January 13th, 2022 — Transact Campus replied on the same day. On January 14th, 2022, we responsibly disclosed the leak to Transact Campus and on January 16th, 2022, the data breach was secured.
Transact Campus later replied to our messages, and told us that the Elasticsearch server was not under their control:
“Apparently this was set up by a third party for a demo and was never taken down. We did confirm that the dataset was filled with a fake data set and not using any production data.”
Note: We checked a sample of users on the open Elasticsearch and this data seemed to belong to real people.
Statement from Foundry:
“This incident did not affect any systems at Transact; it was isolated to a single Foundry gateway server. The potential exposure was discovered by a third party security company that actively scans for vulnerable Elasticsearch clusters. Rather than test data as intended the Elasticsearch server pulled in production logs that contained clear text username and passwords of fewer than 700 students who attempted to register for meal plan account access between October 10, 2021 and January 14, 2022. Only registration attempts logged within that timeframe accounts for the accounts that were affected.”
Statement from Transact:
“Also anyone accessing the production logs would have been unable to engage in transactions on the Transact platform using username and the clear text password alone. Transact did force a password change out of an abundance of caution. Transact also engaged in a significant diligence effort after receiving notice from SafetyDetectives. Protecting Transact client and student data and the systems that collect, process, and maintain this data is of critical importance. Therefore, the security of systems, applications and services include controls and safeguards to offset possible threats. Transact’s information security and privacy measures are implemented to guard against unauthorized access to, alteration, disclosure or destruction of data and systems. Transact is committed to providing the highest level of security for its clients and will continue to monitor the current situation and any other potential threats to the security of its systems.”
Data Exposure Impact
We cannot and do not know whether malicious actors accessed the database while it was unsecured. The server’s content could place exposed students at risk of cybercrimes if bad actors have read or downloaded the server’s data.
Spam marketing, phishing attacks, and scams are possible with contact details, full names, and other sensitive details exposed for Transact Campus users. Attackers could conduct spam marketing campaigns with so many leaked email addresses, sending phishing messages, malware, and scams to thousands of people.
In a phishing attack, a cybercriminal could masquerade as a trustworthy individual (such as a college employee) to convince students to provide additional forms of personal data, such as CVV numbers on the back of credit cards. Phishers could also convince a student to click on a malicious link. Once clicked, malicious links can download malware onto the victim’s device, which could supplement other forms of data collection and cybercrime.
Exposed students could also be targeted with scams if cybercriminals accessed the server. In a scam, a cybercriminal attempts to trick the victim into paying them money. Like phishing attacks, cybercriminals could use other forms of exposed data to target the victim. For example, a cybercriminal could convince an exposed student to pay outstanding tuition fees directly to the attacker.
Exposed account credentials were stored in plain text and this presents further risks for affected students. If any hacker accessed the server, they could’ve easily read the unencrypted usernames and passwords. A cybercriminal could gain access to students’ accounts with this information, and they could potentially alter details and threaten to rack up sizable charges unless a fee is paid.
Preventing Data Exposure
What can we do to protect our data and minimize the risk of cybercrime?
Here are a few tips to prevent data exposure:
- Don’t provide your personal information to a company, organization, or person unless you trust that entity 100%.
- Only visit websites that have a secure domain name (domains with a “https” and/or closed lock symbol at the beginning).
- Be extra careful when providing your most sensitive forms of data, such as your social security number.
- Create rock-solid passwords that contain a mixture of letters, numbers, and symbols. Update your passwords regularly.
- Don’t click a link online unless you’re completely sure it’s from a legitimate source. Links could be in emails, messages, or on phishing websites that are masquerading as legitimate domains.
- Edit your privacy settings on social media so that your content and information are only visible to friends and trusted users.
- Avoid displaying or typing highly sensitive data (such as credit card numbers or passwords) when you’re using a public or unsecured WiFi network.
- Educate yourself about the risks of cybercrime, the importance of data protection, and the methods that reduce your chances of falling victim to phishing attacks and malware.
About Us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including 2.6 million users exposed by an American social analytics platform IGBlade, as well as a breach at a Brazilian Marketplace Integrator platform Hariexpress.com.br that leaked more than 610 GB of data.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.