
The SafetyDetectives cybersecurity team has discovered a major data leak affecting the software company called StoreHub.
StoreHub is based in Malaysia and provides a point of sale (POS) software system which is mostly used in restaurants and retail stores.
The exposed data was stored on a StoreHub’s Elasticsearch server that was left open without any password-protection or encryption. The unprotected server potentially compromised the information of thousands of restaurants and retail stores, along with their staff and roughly 1 million customers.
Who Is StoreHub?
StoreHub was founded in 2013 in Malaysia and currently has their headquarters in Petaling Jaya. Their product is used by over 15,000 businesses according to their website, primarily in the Southeast Asia region.
The company sells POS software primarily to F&B (food and beverages) businesses, such as restaurants, but also to retail stores.
POS software is primarily used to process and record purchases and transactions in customer-facing businesses (restaurants, cafes, bars, shops, etc.), as well as issuing receipts and tracking sales of particular items – such as meals in a restaurant, or individual pieces of clothing in a store.
StoreHub also offers a full suite of business management tools and analytics. These include e-commerce and online delivery, inventory management, employee management, loyalty programs, and customer analytics.
As a result, StoreHub was able to collect data from over 1 million people from across Southeast Asia – primarily the customers of businesses using its software.
What Was Exposed?
Our cybersecurity team discovered that Storehub had misconfigured one of their Elasticsearch server, causing it to leak over 1.7 billions records and over 1 terabyte of data. This exposed almost 1 million customers in Malaysia and potentially across Southeast Asian countries.
StoreHub sells POS software to customer-facing businesses, so the exposed data comes in two categories:
- Data from customers of businesses using StoreHub
- Data from businesses using StoreHub
Data from Customers of Businesses using StoreHub
Exposed personally identifiable information (PII) from customers includes:
- Full names
- Phone numbers
- Physical addresses
- Email addresses
- Type of device used
The server also exposed data related to payments and order information belonging to the customers, exposing PII such as:
- Transaction dates
- Ordered items
- Store locations
Some of the order details exposed partially masked credit card information.
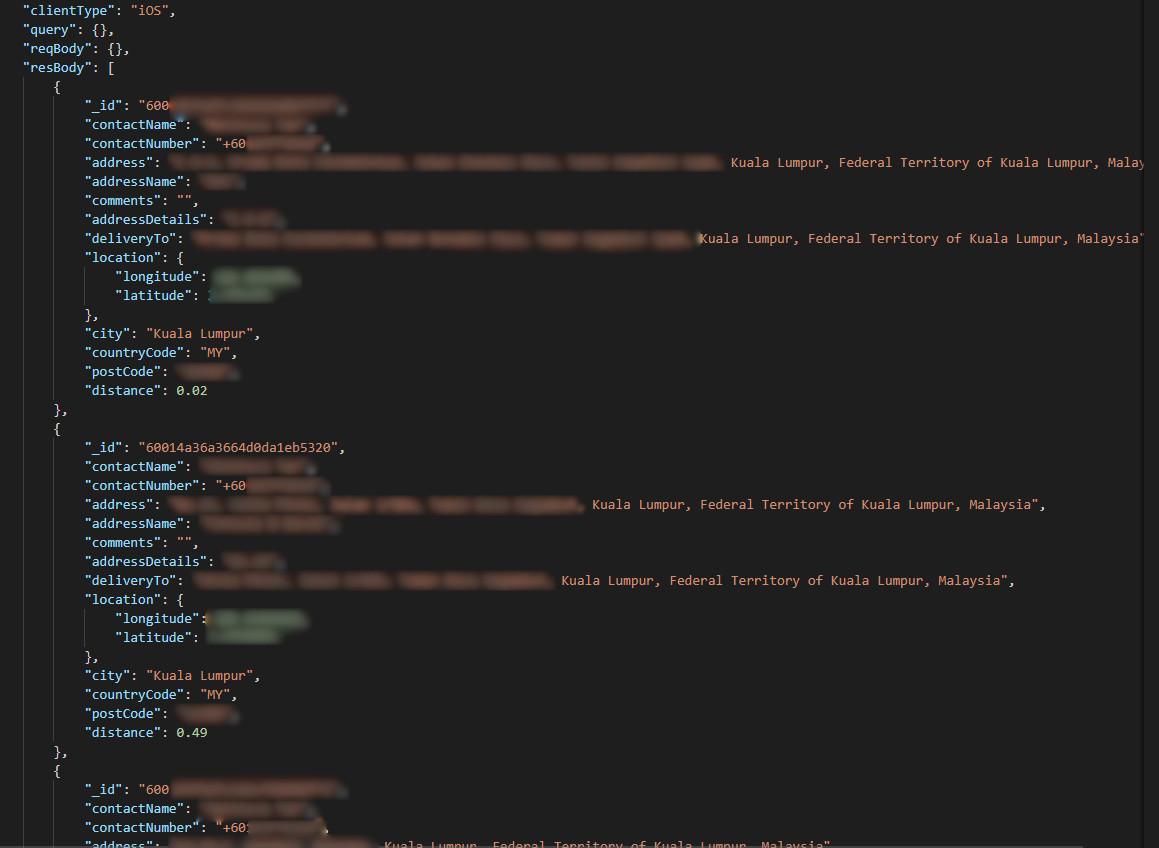
Leaked log lines showing customers’ full names, phone numbers, and addresses.
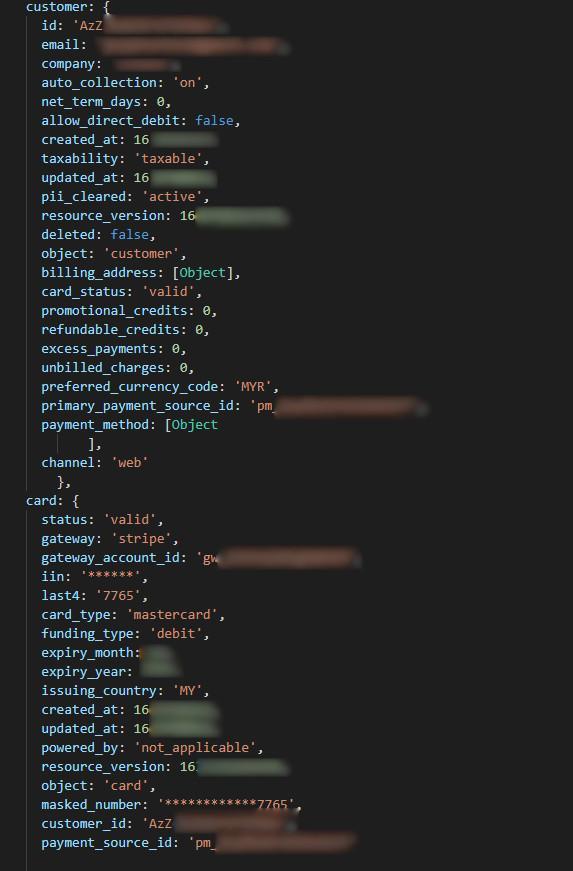
Payment log lines showing email address, card type, and last four digits of card number.
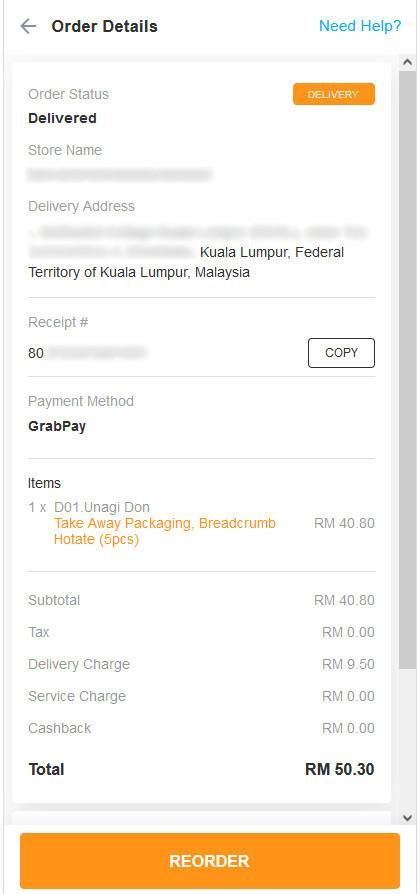
Leaked order history showing receipt number, items ordered, price, and physical address
Data from Businesses using StoreHub
The leak also affected the businesses using StoreHub and their staff members. Leaked information from the businesses include:
- Check-in/Check-out times from employees
- Employee names
- Store names
- Store physical addresses
- Store email addresses
Our cybersecurity team also saw leaked access tokens, which bad actors could use to login to and modify the businesses’ websites, potentially causing more harm. Which we couldn’t test for ethical reasons.
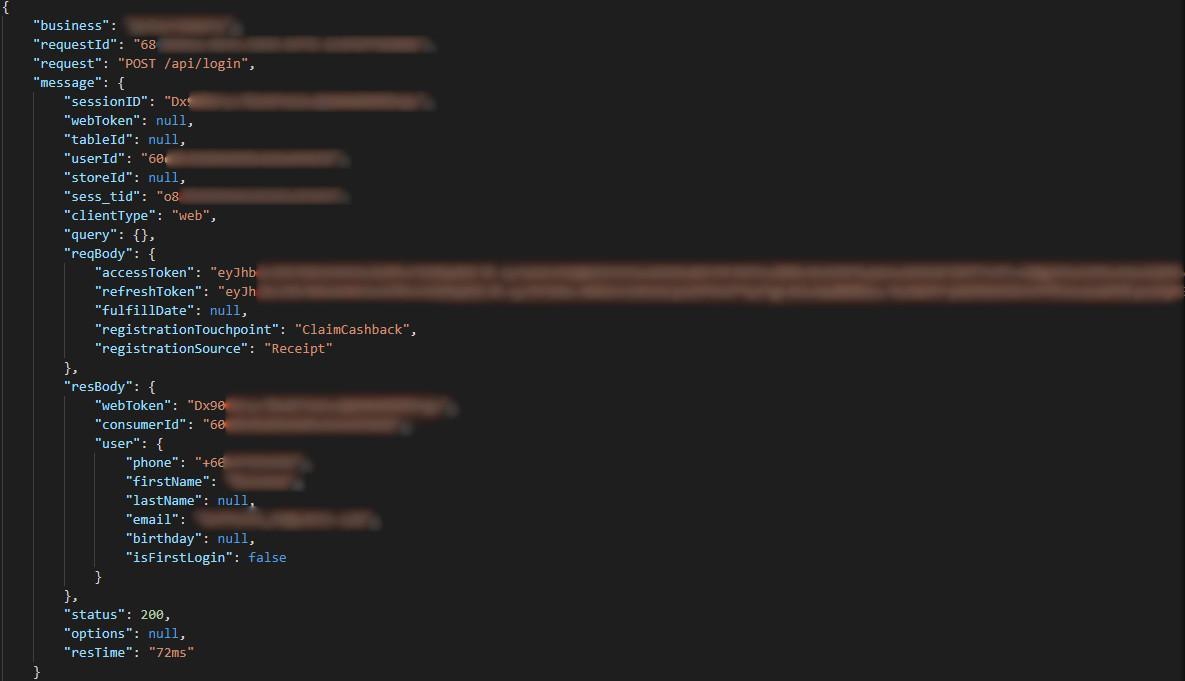
Leaked business log lines showing a user login access token
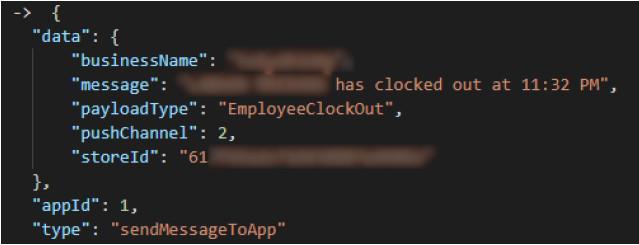
Leaked log lines of an employee clocking out
The table below shows a breakdown of this StoreHub data leak.
Our cybersecurity team discovered this leak on January 12, 2022. The server content seems to have been exposed since at least late November of 2021.
Upon finding the leak, our cybersecurity team followed the rules of ethical hacking by leaving the server and data untouched, then contacting the responsible company.
We emailed StoreHub as soon as we discovered the leak. On January 18, we sent a follow up email to them and we sent an email to StoreHub’s chief technology officer. We received no response by January 27, so we contacted Malaysian CERT and Amazon Web Services (the hosting company). Both responded promptly.
We were able to disclose the leak to the Malaysian CERT on January 28. The Malaysian CERT asked us for more information on February 2, but the server was secured by then. We estimate the server was secured between that period from January 28 to February 2.
Data Leak Impact
Exposed PII leaves victims vulnerable to theft and fraud from bad actors who get their hands on the PII details.
We have no way to confirm if unethical hackers have discovered this data leak, but affected businesses and customers should be on alert for the following potential threats.
Scams & Fraud
The exposed PII leaves customers vulnerable to fraud attempts. For example, bad actors could call victims and gain their trust by confirming purchase information involving the price and date of a transaction—or even the last four digits of a credit card number.
After gaining trust, the bad actors could acquire further information from the victim which could then allow them to inflict actual harm by accessing their bank or abusing credit card information.
Account Theft
The leak contains account tokens, which most likely belong to the businesses using the StoreHub server. Bad actors could make use of these tokens to login as the businesses or customers and potentially modify account details.
This could harm the business in a variety of ways, depending on what the bad actors choose to do. For ethical reasons, we can’t test the capabilities of the exposed tokens. However, a theoretical example is that they could allow bad actors to modify the menu on a restaurant’s account or take down the business’s listing entirely. Exposed tokens also could put customers at risk, as bad actors could potentially modify the site to collect even more sensitive PII and further compromise the victims.
Risk of Property Theft for Customers
The detailed information from the leak creates many vulnerabilities for customers. Information in the leak could allow bad actors to track and intercept orders which the customer has already paid for.
The leak also indicates the times that some customers generally leave their homes. In the wrong hands, this information could put the customers’ property at risk for a physical break in.
Risk of Property Theft for Businesses
The leak contains long lists of staff check-in and check-out times, which tells bad actors exactly how many employees are generally in the store during specific times. If they intended to physically break in and steal from the business, this information would help in the theft.
Preventing Data Exposure
What can you do to protect your data and minimize your risk of cybercrime?
Here are some ways you can minimize your risk of data exposure:
- Only provide your personal information to individuals and companies whom you trust.
- Only visit secure websites. Secure websites have domain names that begin with ‘https’ and/or a closed lock symbol.
- Be extra careful when asked to provide the most important forms of personal information (i.e. social security numbers, government ID numbers, and personal preferences).
- Create super-strong passwords using a combination of letters, capitals, numbers, and symbols. Update your passwords regularly.
- Do not recycle passwords across services. Use a password manager if necessary
- Don’t click links in emails, SMS messages, or anywhere else on the internet unless you are completely certain that the source/sender is genuine. If unsure at all, go to the company’s website and find the link there.
- Edit your social media privacy settings. Your accounts should only display your content and personal details to trusted users and friends.
- Limit the tasks you perform and the information you display when connected to public Wi-Fi. For example, do not purchase a product and type out your credit card details on public WiFi.
- Use online sources to learn about cybercrime, data protection, and the steps you can take to avoid phishing attacks and malware.
About Us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including some 200+ million users exposed by Chinese social media management company Socialarks, as well as a breach at Brazilian eCommerce integrator platform Hariexpress that leaked over 1.75 billion records.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.