
EFB (Electronic Flight Bag) information, including sensitive flight details, source code, and staff data, was left accessible.
An AWS S3 bucket containing Pegasus Airlines’ “Electronic Flight Bag” (EFB) information was left without password protection, leaking a range of sensitive flight data, according to the SafetyDetectives cybersecurity team.
The bucket’s information was linked to an EFB software developed by PegasusEFB that pilots use for aircraft navigation, takeoff/landing, refueling, safety procedures, and various other in-flight processes.
PegasusEFB’s open bucket left data including flight charts, navigation materials, and crew PII accessible to anyone. The bucket also exposed the EFB software’s source code, which contained plain-text passwords and secret keys that someone could use to tamper with extra-sensitive files. We didn’t test these credentials for ethical reasons.
Almost 23 million files were found on the bucket, totaling around 6.5 TB of data. This exposure could impact the safety of every Pegasus passenger and crew member around the world. Affiliated airlines that are using PegasusEFB could also be affected.
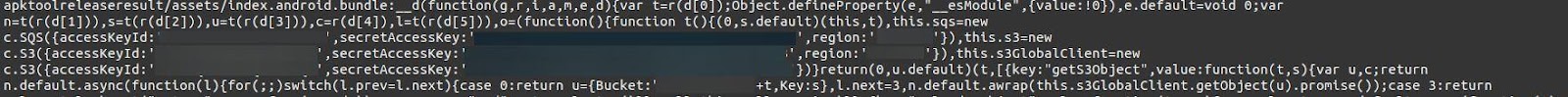
Passwords and secret keys could provide access to extra-sensitive files
PegasusEFB’s open bucket was discovered on February 28th, 2022, as part of the SafetyDetectives cybersecurity team’s large-scale web mapping project. SafetyDetectives researchers use web scanners to find unsecured data stores. Upon discovery of the bucket, our researchers examined PegasusEFB’s exposed data.
We emailed Pegasus Airlines on March 1st, 2022, regarding PegasusEFB’s open bucket. On March 20th, 2022, we sent a follow-up message to Pegasus and reached out to PegasusEFB. On March 24th, 2022, we responsibly disclosed the data exposure to Pegasus EFB after making contact with the company.
The AWS S3 bucket was promptly secured and PegasusEFB later replied, thanking us for the notification.
Who Is the Company?
Founded in 1990, Pegasus Airlines is a Turkish carrier that specializes in low-cost domestic and international flights. The Turkish private equity firm Esas Holding AS owns a majority stake in the company. Pegasus is headquartered in Istanbul and generated US$620 million in revenue in 2021.
PegasusEFB, a company affiliated with Pegasus Airlines, owns the open bucket containing Pegasus’ EFB information. Several airlines use the PegasusEFB software, including Pegasus, IZair, and Air Manas according to its website.
We know PegasusEFB owns the Electronic Flight Bag due to references in the bucket’s content.
PegasusEFB’s admin panel installation window
What Was Exposed?
PegasusEFB’s open AWS S3 bucket exposed sensitive flight data, crew PII, and source code from the EFB software. Amazon is not responsible for the misconfiguration of PegasusEFB’s bucket.
Sensitive Flight Data
Over 3.2 million files contained sensitive flight data. Spreadsheets (around 2.9 million files) and acceptance forms (over 290,000 files) were the two most-prevalent datasets containing this information.
- Acceptance forms, detailing minor issues found during pre-flight checks
- Flight charts and revisions, used to assist in navigation and landing
- Spreadsheets, containing information on airports, flights, crew shifts, etc.
- Documents and memorandums, incl. Insurance documents, permits, & safety guidelines
- SIL – safety integrity level, logs containing regulations and source code
You can see evidence of these files in the screenshots below.
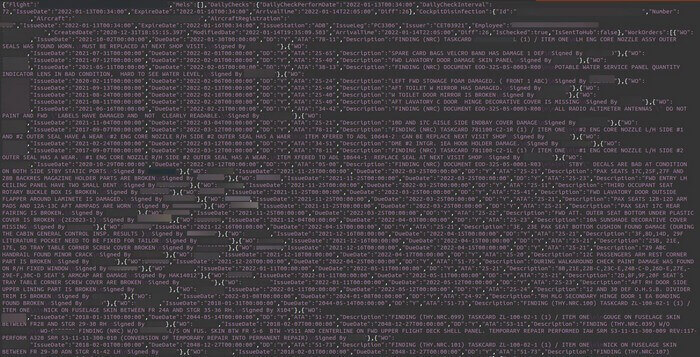
Acceptance forms detailed pre-flight checks
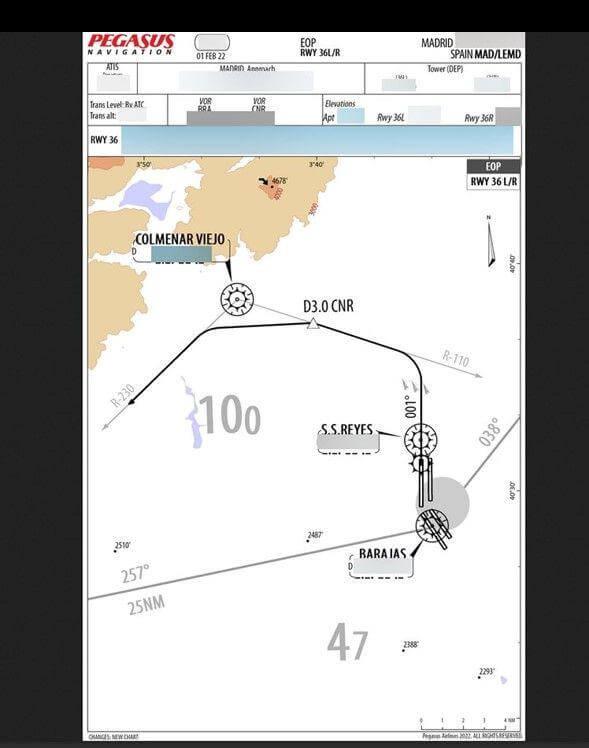
Flight charts featured navigation information
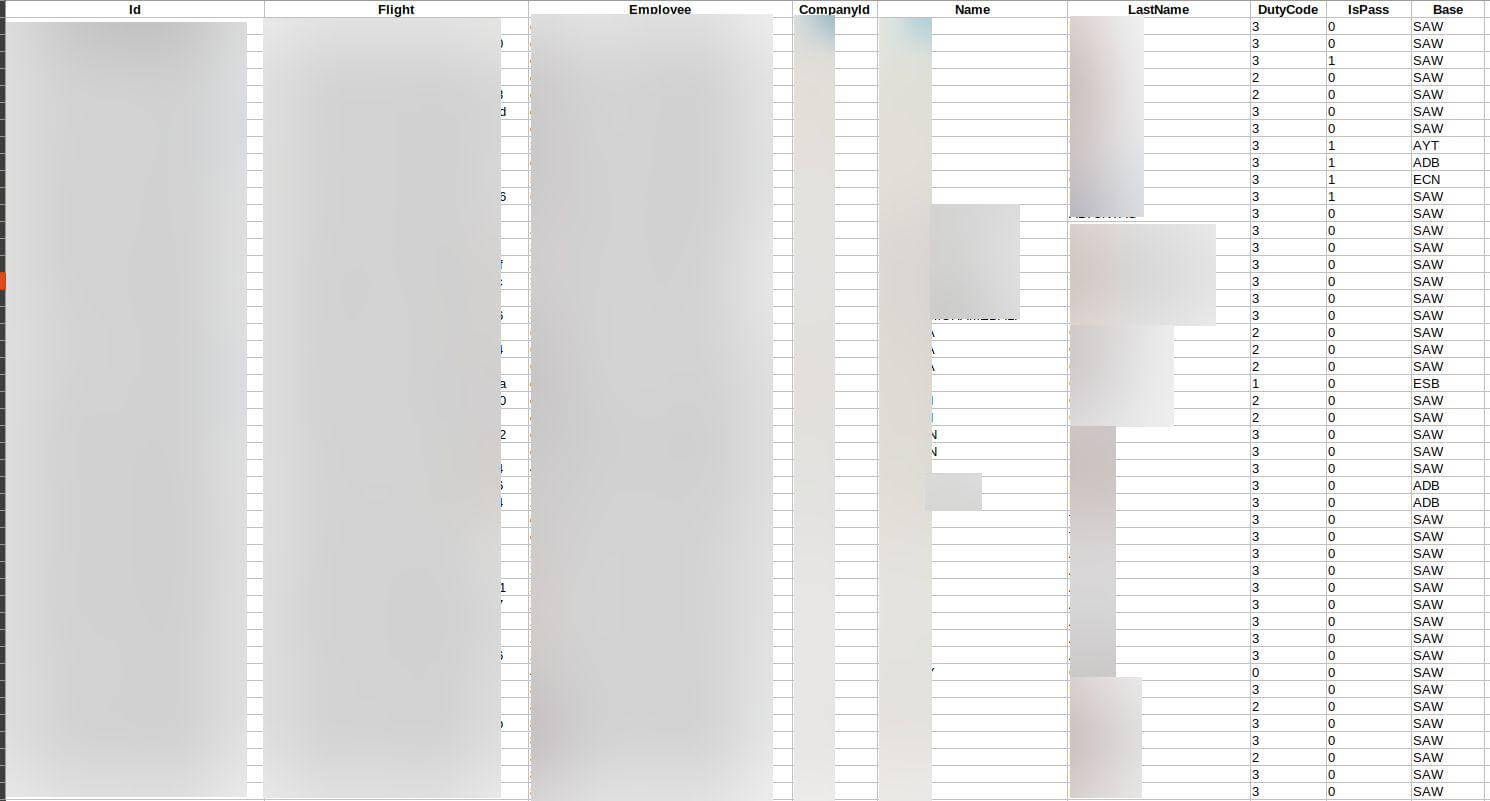
.CSV files showed flight and crew information

Some files contained safety guidance
Crew PII
More than 1.6 million files on the bucket featured crew PII. The vast majority of these files contained the following:
- Photos of staff
- Signatures
You can see examples of crew PII below.

A photo of one crew member

A crew member’s signature
Source Code
Source code from PegasusEFB’s software was also found on the bucket. Nearly 400 files (in .apk, .exe, .dll, .msi, and other formats) contained plain-text passwords and secret keys. These files were left accessible and could allow anyone to delete, modify, or upload data to additional encrypted or password-protected databases, files, and folders on the bucket.
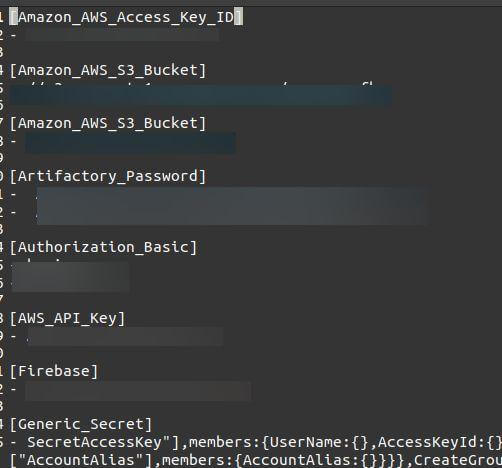
Buckets and keys listed in logs
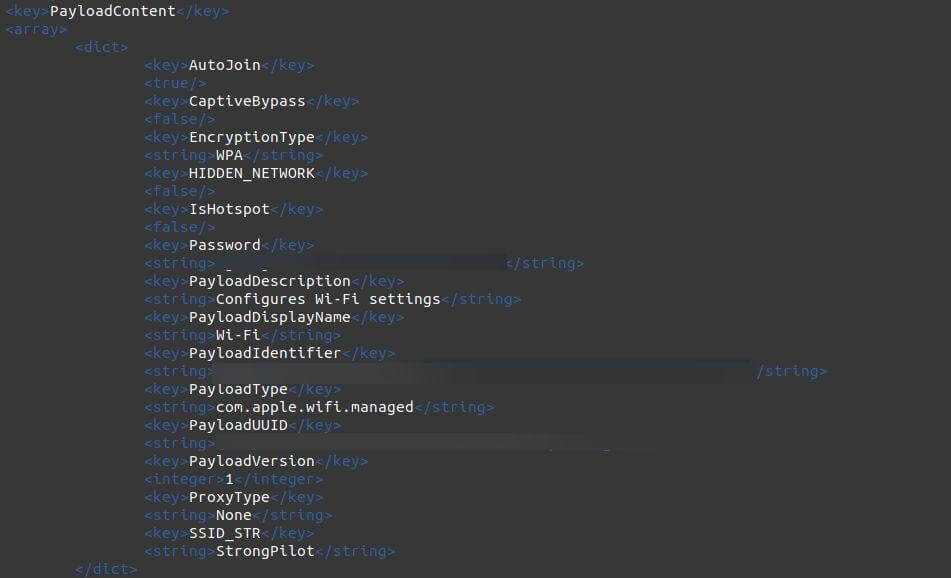
Passwords for private WiFi connections
Files on PegasusEFB’s bucket dated from July 19th, 2019. You can see a full breakdown of PegasusEFB’s data exposure in the table below.
Data Exposure Impact
We do not and cannot know whether bad actors accessed PegasusEFB’s unsecured AWS S3 bucket. If anyone has read or downloaded the bucket’s files, millions of people could face potentially catastrophic threats.
Bad actors could tamper with sensitive flight data and extra-sensitive files using passwords and secret keys found on PegasusEFB’s bucket. While we can’t be certain that pilots will use the bucket’s files for upcoming flights, changing the contents of files could potentially block important EFB information from reaching airline personnel and place passengers and crew members at risk. With millions of files containing recent and possibly relevant flight data, unfortunately, an attacker could have numerous options to cause harm if they found PegasusEFB’s bucket.
Pegasus’ open bucket could facilitate other crimes. A bad actor could identify airplane staff via pictures, signatures, and crew shifts and force them to smuggle goods, weapons, or drugs across borders. What’s more, attackers could use security guidelines to identify weak points in an airport or airplane’s security.
Staff members should seek assistance from law enforcement if they’re approached or contacted by malicious individuals. PegasusEFB may check the accuracy of critical documents, while airlines and airports should change exposed security protocols where possible.
At the very least, PegasusEFB’s open bucket has violated the privacy of airplane staff. With this in mind, PegasusEFB may have breached Turkey’s data protection regulation, the Law on the Protection of Personal Data (LPPD). Turkey’s Personal Data Protection Authority could therefore impose a maximum fine of approximately US$183,000.
About Us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including 2.6 million users exposed by an American social analytics platform IGBlade, as well as a breach at a Brazilian Marketplace Integrator platform Hariexpress.com.br that leaked more than 610 GB of data.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.