
Intro
The SafetyDetectives security team discovered a data breach affecting the French children’s fashion e-commerce website melijoe.com.
Melijoe is a high-end children’s fashion retailer based in France. An Amazon S3 bucket owned by the company was left accessible without authentication controls in place, exposing sensitive and personal data for potentially hundreds of thousands of customers.
Melijoe has a global reach and, consequently, this incident impacts customers located around the world.
What is Melijoe?
Founded in 2007, melijoe.com is an e-commerce fashion retailer that specializes in luxury children’s clothing. The company offers clothing for girls, boys, and babies. Melijoe.com also features top brands, such as Ralph Lauren, Versace, Tommy Hilfiger, and Paul Smith Junior.
“Melijoe” is operated by the company officially registered as BEBEO, which is headquartered in Paris, France. According to MELIJOE.COM, BEBEO has a registered capital of around €950,000 (~US$1.1 million). The Melijoe service has generated €12.5 million (~US$14 million) over 2 rounds of funding (as per Crunchbase).
Melijoe merged with the prominent Swedish children’s fashion conglomerate the Babyshop Group (BSG) in late 2020 — a company with an annual turnover of 1 billion SEK (~US$113 million) across a range of high street and e-commerce stores.
Several indicators confirm that Melijoe/BEBEO has a bearing on the open Amazon S3 bucket. While brands, birthdates, and other contents in the bucket suggest the owner is a French children’s fashion retailer, there are also references to “Bebeo” throughout. Most importantly, the bucket contains sitemaps for melijoe.com:
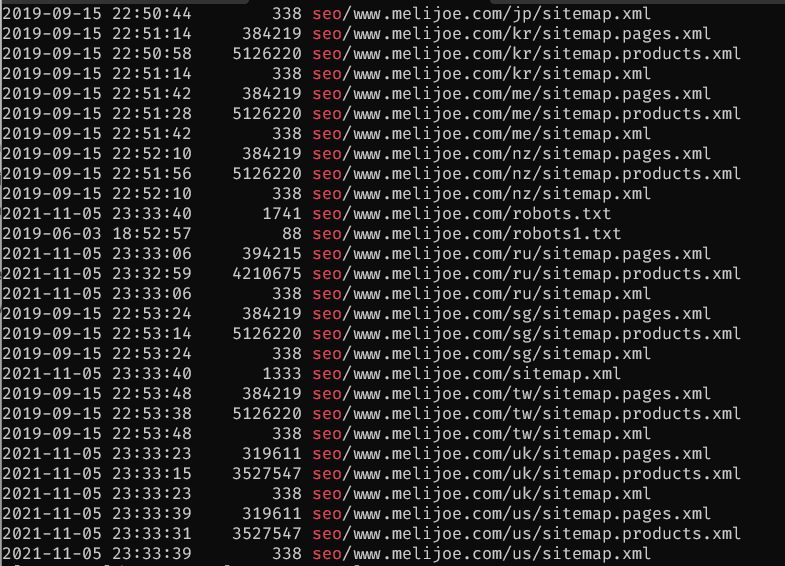
Sitemaps found within the open bucket reference melijoe.com
What was Exposed?
Altogether, melijoe.com’s misconfigured Amazon S3 bucket has exposed almost 2 million files, totaling around 200 GB of data.
A few files on the bucket exposed hundreds of thousands of logs containing the sensitive data and personally identifiable information (PII) of Melijoe’s customers.
These files contained different data sets: Preferences, wishlists, and purchases.
There were other file types on the bucket, too, including shipping labels and some data related to melijoe.com’s product inventory.
Preferences
Preferences data were exported from customer accounts. The data exposed details of consumers’ tastes, likes, and dislikes concerning their purchasing decisions. There were tens of thousands of logs found on one file.
Preferences exposed forms of customer PII and sensitive customer data, including:
- Email addresses
- Names of children
- Genders
- Dates of birth
- Preferences of brands
Preferences data can be collected via purchase data and on-site clicks. Preferences are often used to personalize each customer’s product recommendations.
You can see evidence of preferences below.

Logs of customer preferences were on the bucket
Wishlists
Wishlists data revealed details around customers’ on-site wishlists—collections of desired products curated by each customer. Again, this information appeared to have been taken from customer accounts. There were over 750,000 logs on one file with data belonging to over 63,000 unique users’ email addresses.
Wishlists exposed forms of customer PII and sensitive customer data:
- Email addresses
- Date products were added to wishlists
- Date products were removed from wishlists (if removed)
- Item codes, used to ID products internally
Wishlists were created by customers themselves and not via tracking on-site behavior. Wishlists varied from one item long to thousands of items long. Longer wishlists could allow one to know more about customers’ favorite items.
The following screenshots show evidence of wishlists.
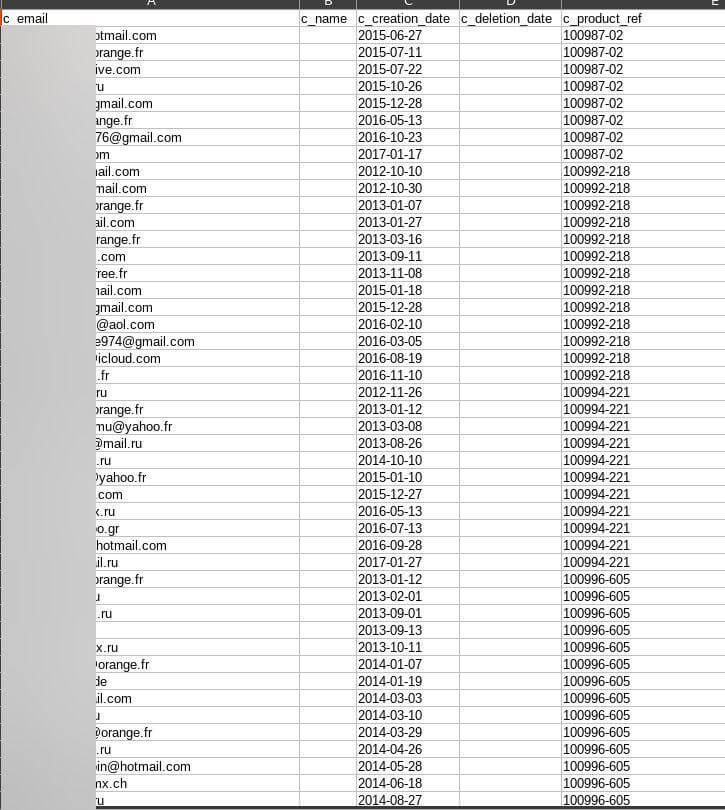
Vast logs of customer wishlists featured on a file
Purchases
Purchases data showed over 1.5 million items bought in hundreds of thousands of orders. There were orders from over 150,000 unique email addresses on a single file.
Purchases exposed customer PII and sensitive customer data, including:
- Email addresses
- Ordered items’ SKU code
- Time of order placed
- Financial details of orders, incl. prices paid and currency
- Payment methods, i.e. Visa, PayPal, etc
- Delivery information, inc. delivery addresses and delivery dates
- Billing addresses
Purchases data seemingly affected the largest number of users compared to the other two datasets. These logs extensively detail the purchasing behavior of Melijoe customers. Again, this reveals private information which could be used against consumers.
Some customers purchased a large number of products, while other customers bought just one or two items. As with wishlists, customers who ordered more items had more information exposed about their favored products.
The screenshots below show evidence of purchase logs.
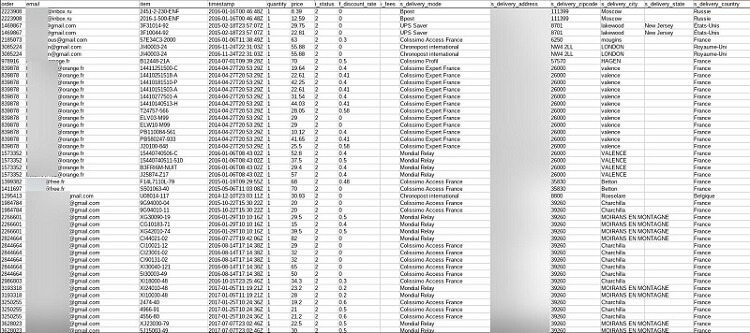
Purchases logs exposed numerous forms of data
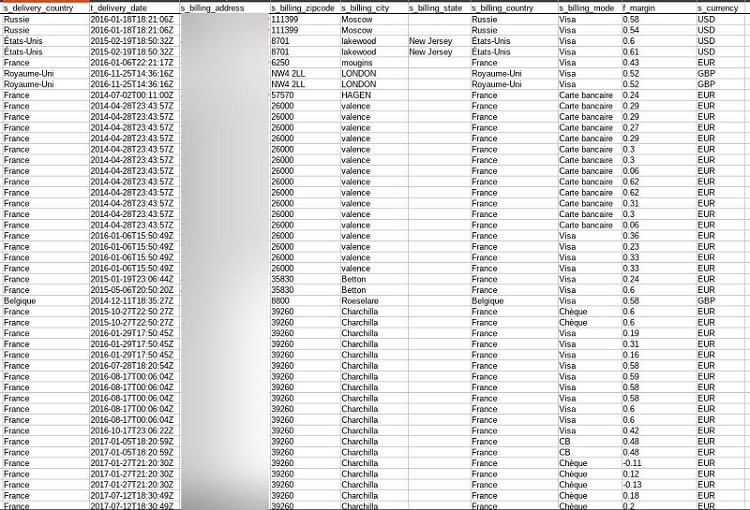
Delivery, billing, and currency information was found within the logs, too
Shipping Labels
Melijoe’s AWS S3 Bucket contained shipping labels. Shipping labels were associated with the orders of Melijoe customers. There were more than 300 of these files on the bucket.
Shipping labels exposed several examples of customer PII:
- Full names
- Phone numbers
- Delivery addresses
- Product barcodes
You can see a shipping label for one customer’s order below.
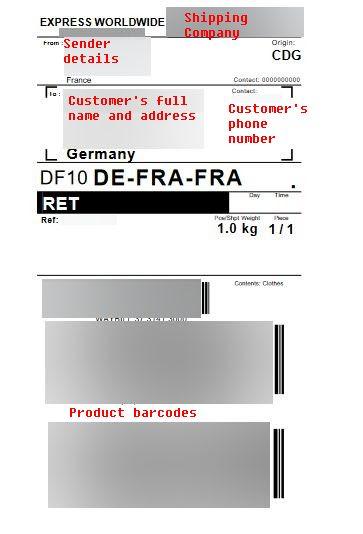
A shipping label found on the bucket
In addition to the data mentioned above, Melijoe’s bucket also contained information about Melijoe’s product catalog and stock levels.
We could only analyze a sample of the bucket’s contents for ethical reasons. Given the large number of files stored on the bucket, there could be several other forms of sensitive data exposed.
Melijoe’s Amazon S3 bucket was live and being updated at the time of discovery.
It’s important to note that Amazon doesn’t manage Melijoe’s bucket and, therefore, isn’t responsible for its misconfiguration.
Melijoe.com sells products to a global customer base and, as such, customers from across the globe have been exposed in the unsecured bucket. Primarily, customers from France, Russia, Germany, the United Kingdom, and the United States are affected.
We estimate that up to 200,000 people have had their information exposed on Melijoe’s unsecured Amazon S3 bucket. This figure is based on the number of unique email addresses we saw on the bucket.
You can see a full breakdown of Melijoe’s data exposure in the table below.
The bucket contained files that were uploaded between October 2016 and the date we discovered it—November 8th, 2021.
According to our findings, the data on files related to purchases and wishlists that were made over several years. Purchases detailed on Melijoe’s bucket were made between May 2013 and October 2017, while wishlists were created between October 2012 and October 2017.
On November 12th, 2021, we messaged Melijoe regarding its open bucket and on November 22nd, 2021, we sent a follow-up message to some old and new Melijoe contacts. On November 25th, 2021, we reached out to the French Computer Emergency Response Team (CERT) and AWS, and sent follow-up messages to both organizations on December 15th, 2021. The French CERT replied and we responsibly disclosed the breach. The French CERT said they would contact Melijoe but we never heard back from them again.
On January 5th, 2022, we contacted the CNIL and followed up on January 10th, 2022. CNIL replied a day later, informing us that “the case is being handled by our services.” We also contacted the French CERT on January 10th, 2022, who told us “Unfortunately, after many reminders, the owner of the bucket did not respond to our messages.”
The bucket was secured on February 18th, 2022.
Both melijoe.com and its customers could face impacts from this data exposure.
Data Breach Impact
We cannot and do not know whether malicious actors have accessed the files stored on Melijoe’s open Amazon S3 bucket. With no password protection in place, however, melijoe.com’s bucket was readily accessible to anyone who may have found its URL.
That means a hacker or criminal could have read or downloaded the bucket’s files. Bad actors could target exposed Melijoe customers with forms of cybercrime if that were the case.
Melijoe could come under scrutiny for data protection violations as well.
Impact on Customers
Exposed melijoe.com customers are at risk of cybercrime because of this data breach. Customers have extensive examples of personal and sensitive data exposed on the bucket.
As mentioned, customers with bigger wishlists or larger purchase histories have had more information exposed about their favored products. These individuals could face more tailored and detailed attacks as hackers can learn more about their likes and dislikes. These customers could also be targeted based on the presumption they are wealthy and can afford to buy a lot of high-end products.
Phishing & Malware
Hackers could target exposed Melijoe customers with phishing attacks and malware if they accessed the bucket’s files.
Melijoe’s Amazon S3 bucket contained almost 200,000 unique customers’ email addresses which could provide hackers with a long list of potential targets.
Hackers could contact these customers while posing as a legitimate employee of melijoe.com. Hackers could reference any one of several exposed details to build a narrative around the email. For example, the hacker could reference a person’s preferences/wishlist to convince the customer they’re being offered a deal.
Once the victim trusts the hacker, the bad actor can launch phishing attempts and malware.
In a phishing attack, a hacker will leverage trust to coerce more sensitive and personal information from the victim. The hacker may convince the victim to disclose their credit card credentials, for example, or click on a malicious link. Once clicked, such links can download malware onto the victim’s device—malicious software that allows hackers to conduct other forms of data collection and cybercrime.
Fraud & Scams
Hackers could also target exposed customers with fraud and scams if they accessed the bucket’s files.
A cybercriminal could target exposed customers through email, using information from the bucket to appear as a trustworthy person with a valid reason to reach out.
Hackers could exploit a target’s trust to conduct fraud & scams—schemes that are designed to trick the victim into handing over money. For example, the hacker could use order details and delivery information to conduct a delivery scam. Here, a hacker could ask victims to pay a fake delivery fee to receive their goods.
Impact on melijoe.com
Melijoe may suffer both legal and criminal impacts as a result of its data incident. The company’s misconfigured Amazon S3 bucket could have violated data protection laws, while other businesses might access the bucket’s content at melijoe.com’s expense.
Data Protection Violations
Melijoe may have violated the EU’s General Data Protection Regulation (GDPR) as the company’s bucket was misconfigured, exposing the data of its customers.
The GDPR protects the sensitive and personal data of EU citizens. The GDPR governs companies on their collection, storage, and use of customers’ data, and any improper handling of data is punishable under the regulation.
The Commission nationale de l’informatique et des libertés (CNIL) is France’s data protection authority and is responsible for enforcing the GDPR. Melijoe could come under the scrutiny of the CNIL. The CNIL can issue a maximum fine of €20 million (~US$23 million) or 4% of the company’s annual turnover (whichever is greater) for a breach of GDPR.
Melijoe’s open Amazon S3 bucket has not only exposed the data of EU citizens but of customers from nations around the world. Therefore, melijoe.com could be subject to punishments from several other jurisdictions in addition to the CNIL. For example, the Federal Trade Commission (FTC) of the United States may choose to investigate melijoe.com for a potential violation of the FTC Act, and the UK’s Information Commissioner’s Office (ICO) could investigate melijoe.com for a possible breach of the Data Protection Act 2018.
With exposed customers from various other continents on Melijoe’s bucket, numerous data protection authorities could choose to investigate melijoe.com.
Competition Espionage
Exposed information could be collected by hackers and sold to third parties that have an interest in the data. This might include businesses that are competitors of melijoe.com, such as other clothing retailers. Marketing agencies may also see value in the bucket’s data.
Rival businesses could use the data to carry out competition espionage. In particular, competitors could access melijoe.com’s customer list to find potential customers for their own business. Rival businesses could contact exposed customers with offers in an attempt to steal business away from Melijoe and bolster their own customer base.
Preventing Data Exposure
What can we do to keep our data secure and mitigate the risk of exposure?
Here are a few tips to prevent data exposure:
- Only provide your personal information to individuals, organizations, and entities that you trust completely.
- Only visit websites with a secure domain (i.e. websites that have a “https” and/or closed lock symbol at the beginning of their domain name).
- Be especially careful when providing your most sensitive forms of data, such as your social security number.
- Create unbreakable passwords that use a mix of letters, numbers, and symbols. Update your existing passwords regularly.
- Don’t click a link in an email, message, or anywhere else on the internet unless you’re certain the source is legitimate.
- Edit your privacy settings on social media sites so that only friends and trusted users can see your content.
- Avoid displaying or typing important forms of data (such as credit card numbers or passwords) when connected to an unsecured WiFi network.
- Educate yourself about cybercrime, data protection, and the methods that reduce your chances of falling victim to phishing attacks and malware.
About Us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including 2.6 million users exposed by an American social analytics platform IGBlade, as well as a breach at a Brazilian Marketplace Integrator platform Hariexpress.com.br that leaked more than 610 GB of data.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.