
The SafetyDetetectives security team discovered a data breach affecting CashMama, a money lending platform based in India, which exposed a comprehensive array of customer data that was invasively collected and stored.
CashMama’s Amazon S3 bucket was left in open form, exposing sensitive and personal data for hundreds of thousands of customers.
CashMama’s misconfigured bucket revealed enough sensitive data to potentially expose its users to the most damaging forms of cybercrime.
Who Is CashMama?
Founded in Hyderabad, in India’s Telangana region back in 2018, CashMama was a consumer finance application that offered instant money lending services to its users.
CashMama is now defunct after it was allegedly involved in an instant loan app scandal.
While primarily aimed at young professionals, CashMama promised convenience with a loan application and screening process that was 100% online. Customers could expect timely approval, even without a loan history or credit card, and once approved, CashMama users could receive their loan within a matter of minutes. The app offered loans between 3,000 and 5,000 rupees (around US$40 to US$65) with short-term tenures.
CashMama was owned by the parent company Onion Credit Private Limited which also operated other instant loan apps with data on the open bucket, such as Loan Zone and MeraLoan. Each of these apps is implicated in allegations of racketeering, according to The Indian Express.
Onion Credit Private Limited representatives were arrested by Indian authorities in late 2020 following allegations of blackmail, harassment, coercion, and financial fraud (as per The Indian Express). CashMama’s open bucket demonstrates functionality that allowed its owners to snoop on customers via several mobile apps and related services.
Following our analysis, it appears that the bucket belongs to CashMama due to references to the company in stored emails.
An email from the CashMama team found on the bucket
What Was Exposed?
CashMama’s misconfigured Amazon S3 bucket exposed more than 6.5 million files, totaling over 1TB of data.
The bucket’s content included PII and sensitive data belonging to the customers of at least four instant loan apps: CashMama, Loan Zone (also known as Vayloan), MeraLoan, and an unidentified app.
The unidentified app’s data was stored under an app name, though, we could not specify exactly which app this name referenced. A small portion of files have an unknown origin — this data could’ve been collected for one of the loan apps mentioned, or, it could’ve been collected for a completely different instant loans app.
There may be customers of various other associated instant loan apps exposed on the bucket as well.
We observed a large amount of personal data that was collected for each app. In fact, we observed 10 different file collections on the bucket. Each file collection was comprised of one or more folders that contained similar files. Each collection’s data relates to one of the instant loan apps on the bucket.
You can see each collection of files, followed by the app we believe is associated with those files, in the list below.
- Loan agreements (CashMama)
- Epoch files (CashMama)
- ID photos files (LoanZone/Vayloan)
- SMS data (LoanZone/Vayloan)
- SMS & contact history (LoanZone/Vayloan)
- Vayloan fingerprint data (LoanZone/Vayloan)
- MeraLoan applications & contracts (MeraLoan)
- Unidentified app files (unidentified app)
- Unknown app’s files (unknown app)
- Processed ID cards (unknown app)
Each folder contained files that featured the PII and sensitive data of customers. We’ll now walk you through the data exposed on CashMama’s bucket, along with an explanation of the files that contained each dataset.
Paperwork & PIIs
Paperwork & PIIs data were exposed in three of the aforementioned collections on the misconfigured AWS S3 bucket:
- Loan agreements
- MeraLoan applications & contacts
- Unknown app’s files
Paperwork & PIIs data exposed the customer PII and sensitive data of CashMama, MeraLoan, and another unknown app’s users. You can see a list of exposed paperwork & PIIs below.
Note: The exposed app (or apps) is named in brackets when the data was not collected for all three apps (CashMama, MeraLoan, & the unknown app).
- Full names.
- Dates of birth.
- Home addresses.
- Parents’ names (of CashMama users).
- Marital status (of CashMama users).
- Occupations (of CashMama users).
- Nationalities (of CashMama users).
- National IDs (of CashMama users).
- Email addresses (of CashMama users).
- IFSC codes* (of CashMama users).
- Related person’s names (of CashMama users).
- Related person’s phone numbers (of CashMama users).
- Photos (of CashMama users), incl. people, people’s income, ID cards, and department tax cards.
- Genders (of CashMama & MeraLoan users).
- Bank accounts (of CashMama & MeraLoan users).
- Loan details (of CashMama & MeraLoan users), incl. loan amount, interest rate, tenure, purpose of loan, etc.
- Phone numbers** (of CashMama & unknown app users).
- Company info (of MeraLoan users).
- PAN numbers (of MeraLoan & unknown app users), i.e. national IDs.
- Location histories (of unknown app users).
- Payment histories (of unknown app users).
*A unique 11-digit code used for online fund transfer in India.
**Note: MeraLoan users’ phone numbers were exposed in a different dataset.
Loan agreements exposed a large portion of this PII and sensitive data, information that belongs to CashMama’s customers. Loan agreements appear to document contracts between customers and instant loan companies. Alternatively, loan agreements could have been sent to the non-bank financial companies (NBFCs) funding the loans. There were almost 300,000 Loan agreements on the misconfigured bucket.
MeraLoan applications & contacts exposed MeraLoan customers’ loan applications and phone contact lists. As such, these files exposed a range of MeraLoan customer PII and sensitive customer data. A folder containing over 10,000 loan applications, submitted by customers, exposed a portion of the data you can see above.
The unknown app’s files exposed a range of user PII and sensitive data, though, we don’t know for which app this information was collected. The unknown app’s files were formatted differently from other logs we observed on the bucket. We don’t know why this was the case. Perhaps, these were logs collected and sent to an associated NBFC. There were over 100,000 of the unknown app’s files on the bucket.
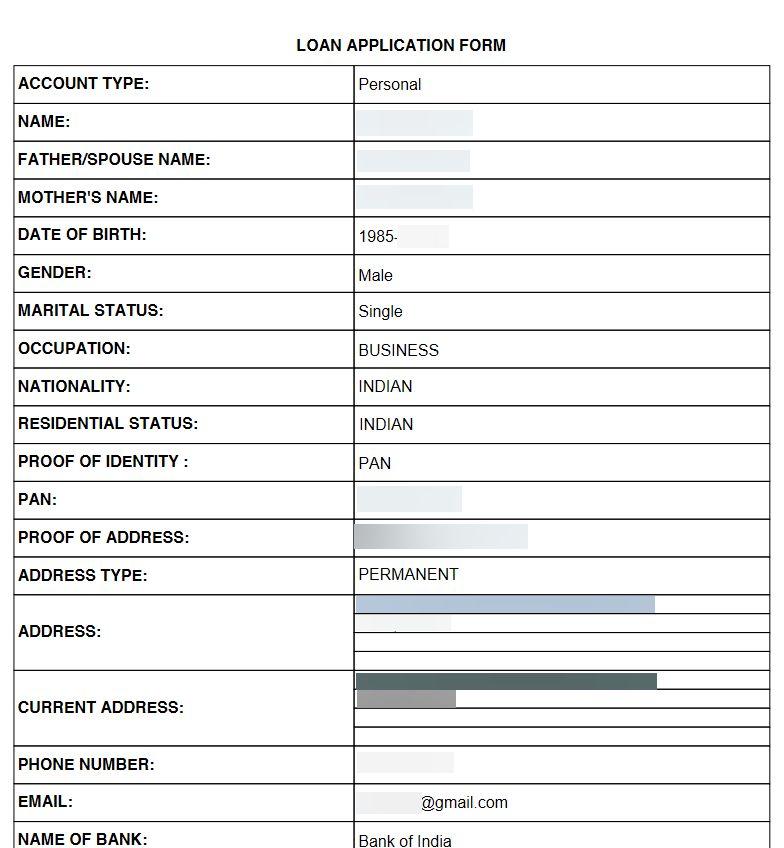
A CashMama user’s data in a loan application
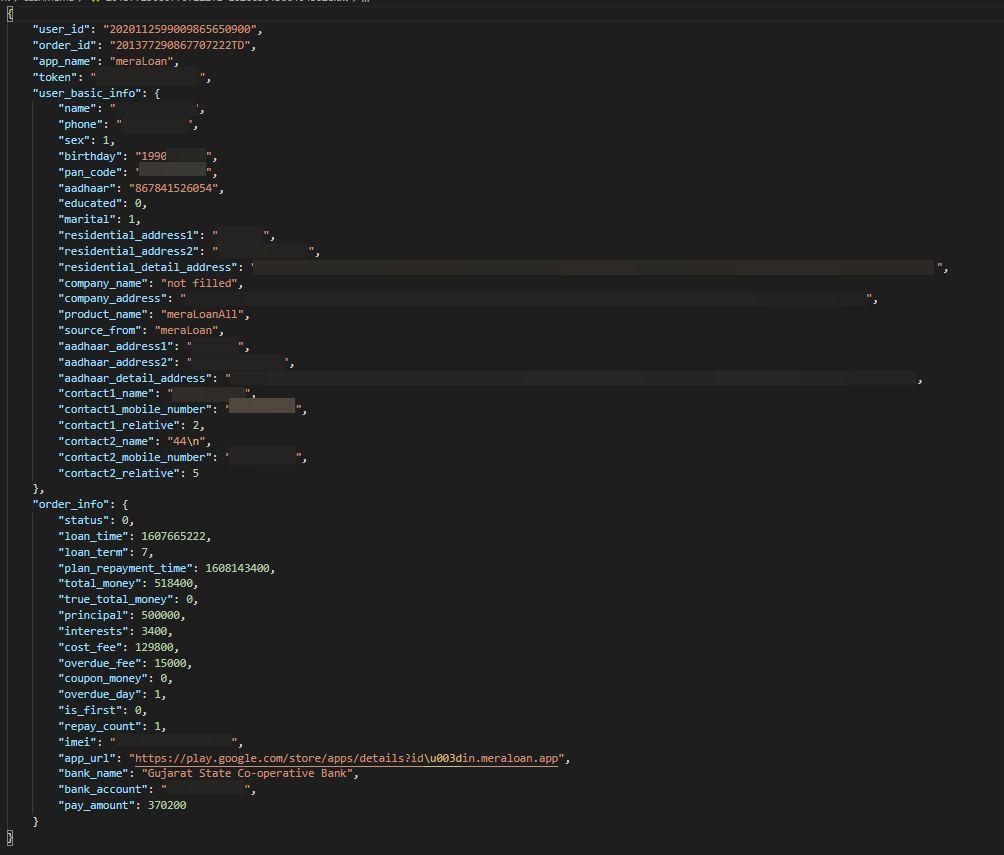
Data from MeraLoan applications
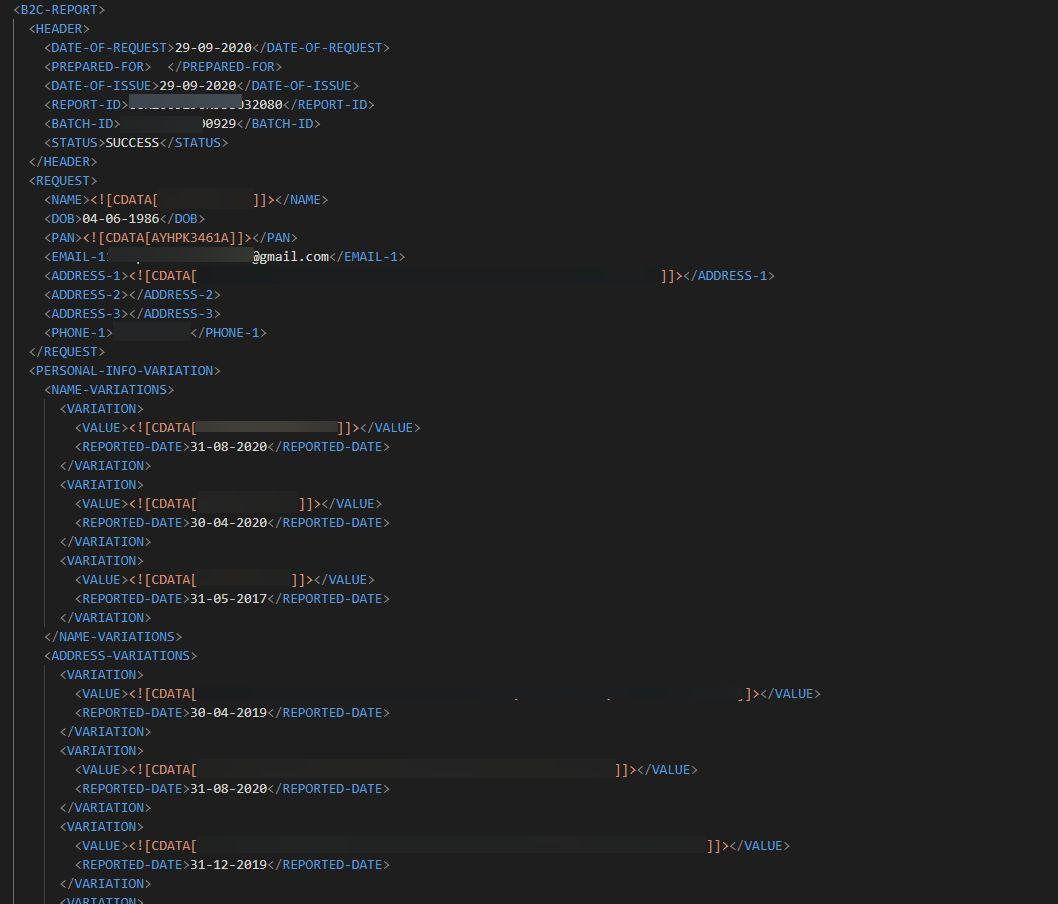
Logs of unknown PII look slightly different
Pictures
Pictures data were exposed in three of the aforementioned locations on the AWS S3 bucket:
- Epoch files
- ID photos files
- Processed ID cards
Pictures exposed the customer PII and sensitive customer data of CashMama, LoanZone (most likely), and an unknown app’s users. There were three datasets exposing this information on CashMama’s AWS S3 bucket:
Note: The exposed app (or apps) that collected each dataset is named in brackets.
- Images data* (of CashMama users):
- Filenames
- Device models
- GPS coordinates
- Times images were taken
- ID photos (likely belonging to LoanZone users):
- Photos of people
- Photos of users’ ID cards (front and back)
- Plaintext IDs (of an unknown app’s users):
- ID card data (incl. name, D.O.B., address, etc.)
*Note: The related images were not included.
Images data included technical information about users’ photos without containing photos themselves. Images data exposed the PII and sensitive data of CashMama customers and was found on epoch files. Nearly 200,000 epoch files exposed the data of around 100,000 CashMama customers.
Epoch files were dumped in two stages into two separate folders and contained a range of user information. The first folder of epoch files contained data that was collected from users’ phones and images data was found in this folder. In the second folder, CashMama conflated mined data with data that customers provided in the CashMama app, linking real people with their phone data.
ID photos files contained ID photos presumably collected during the application and identification process. We believe these photos exposed the PII of LoanZone/Vayloan customers, though, we can’t be certain. Over 2.3 million of these files were observed on the open bucket.
Processed ID cards contained over 170,000 plaintext IDs. Here, ID cards were converted into plaintext via optical character recognition—a technology that scans images for text. This allows the company to reference the data easily on the bucket. Plaintext IDs contained customer PII and sensitive customer data. However, we’re not quite sure why (or for which app) this data was collected.
You can see evidence of the pictures data exposed in these files below.
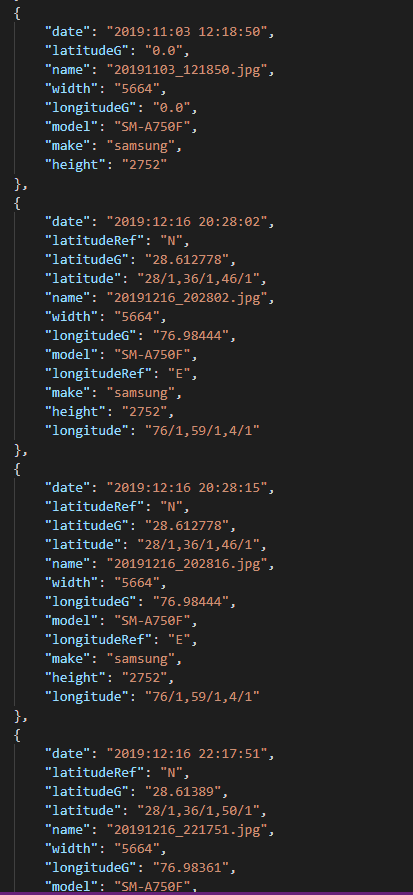
Detailed image metadata of CashMama’s customers

Photo of a LoanZone customer in “ID photos”

ID card information processed in plaintext
Phone-Related Data
Phone-Related data was exposed across several different file collections on CashMama’s open AWS S3 bucket:
- Epoch files
- SMS data
- SMS & contacts
- Vayloan fingerprint data
- MeraLoan applications & contracts
- Unidentified app files
As such, customers of CashMama, LoanZone (most likely), MeraLoan, and an unidentified app have customer PII and sensitive customer data exposed in at least one of the following datasets:
Note: The exposed app (or apps) is named in brackets when the dataset was not collected for all four apps (CashMama, LoanZone, MeraLoan, & the unidentified app).
- Contacts:
- Names
- Phone numbers
- SMS Messages (of CashMama, LoanZone, & an unidentified app’s users):
- Message contents
- Message times
- “From” phone numbers
- Contact names
- Device info (of CashMama & LoanZone users):
- Screen sizes
- Storage space
- Available storage space
- Device memories
- Operating systems
- MAC addresses
- IMEI numbers
- & more
- Installed apps (of CashMama & an unidentified app’s users):
- App names
- Technical names
- Install dates
- App versions
- Battery status (of an unidentified app’s users):
- Users’ phone battery
- GPS locations (of an unidentified app’s users):
- GPS locations at different times/dates
Epoch files contained the contacts, SMS messages, device info, and installed apps of CashMama users.
SMS messages that most likely belong to LoanZone/Vayloan customers were found in SMS data and SMS & contact history files. SMS & contact history files also contained the contacts data of exposed users. Both file types contain customer PII and sensitive customer data that was likely mined from users’ phones. SMS & contact history files were repeatedly updated with fresh data to track any changes on users’ phones.
CashMama’s AWS S3 bucket contained nearly 650,000 SMS data files and almost 1 million SMS & contact history files — the latter exposed phone-related data for over 350,000 customers.
Device info that likely belonged to LoanZone/Vayloan users was also found in a Vayloan fingerprint data folder. We saw over 600,000 files in this folder that contained this form of sensitive user data.
MeraLoan users had their mobile phone contacts data exposed in MeraLoan applications & contracts files. One folder on the bucket stored over 7,000 files containing MeraLoan users’ contacts. We don’t know whether or not the app requested access to users’ contacts to gather this data. If the app did request access, users need to be aware that access to contacts gives the app permission to download all contact files, including the details contained within contacts.
Users of an instant loans app that we were not able to identify had a range of phone-related data exfiltrated from their device and stored in unidentified app files, including contacts, SMS messages, installed apps, battery status, and GPS locations.
Nearly 300,000 files (including duplicates) contained phone-related data belonging to the unidentified app’s users; these files exposed customer PII and sensitive customer data.
You can see evidence of the various forms of phone-related data mentioned in the screenshots below.
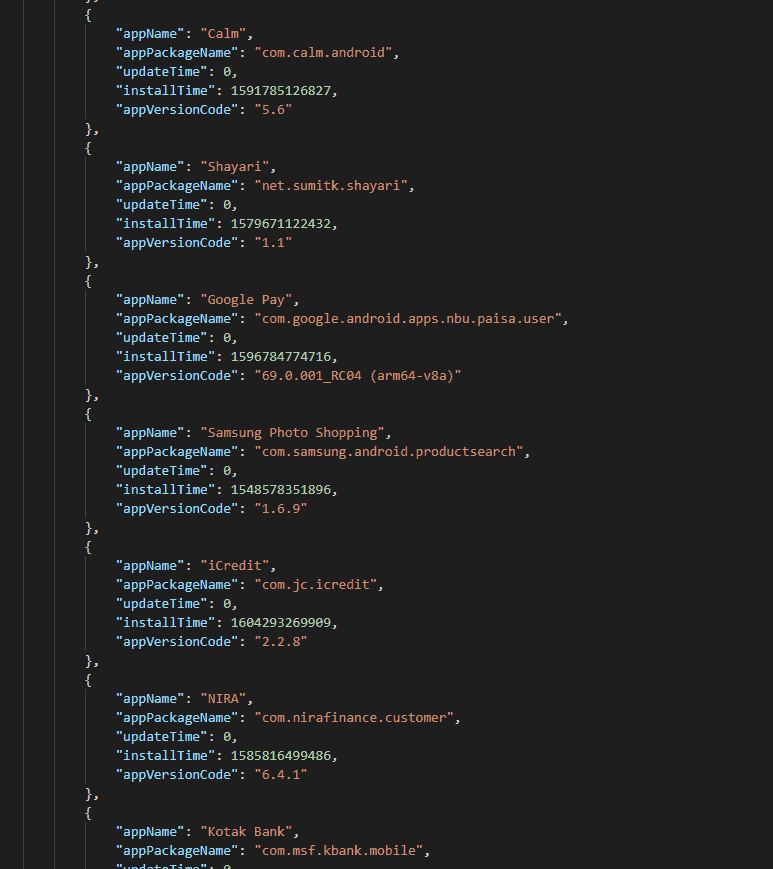
App data in stage 1 epoch files
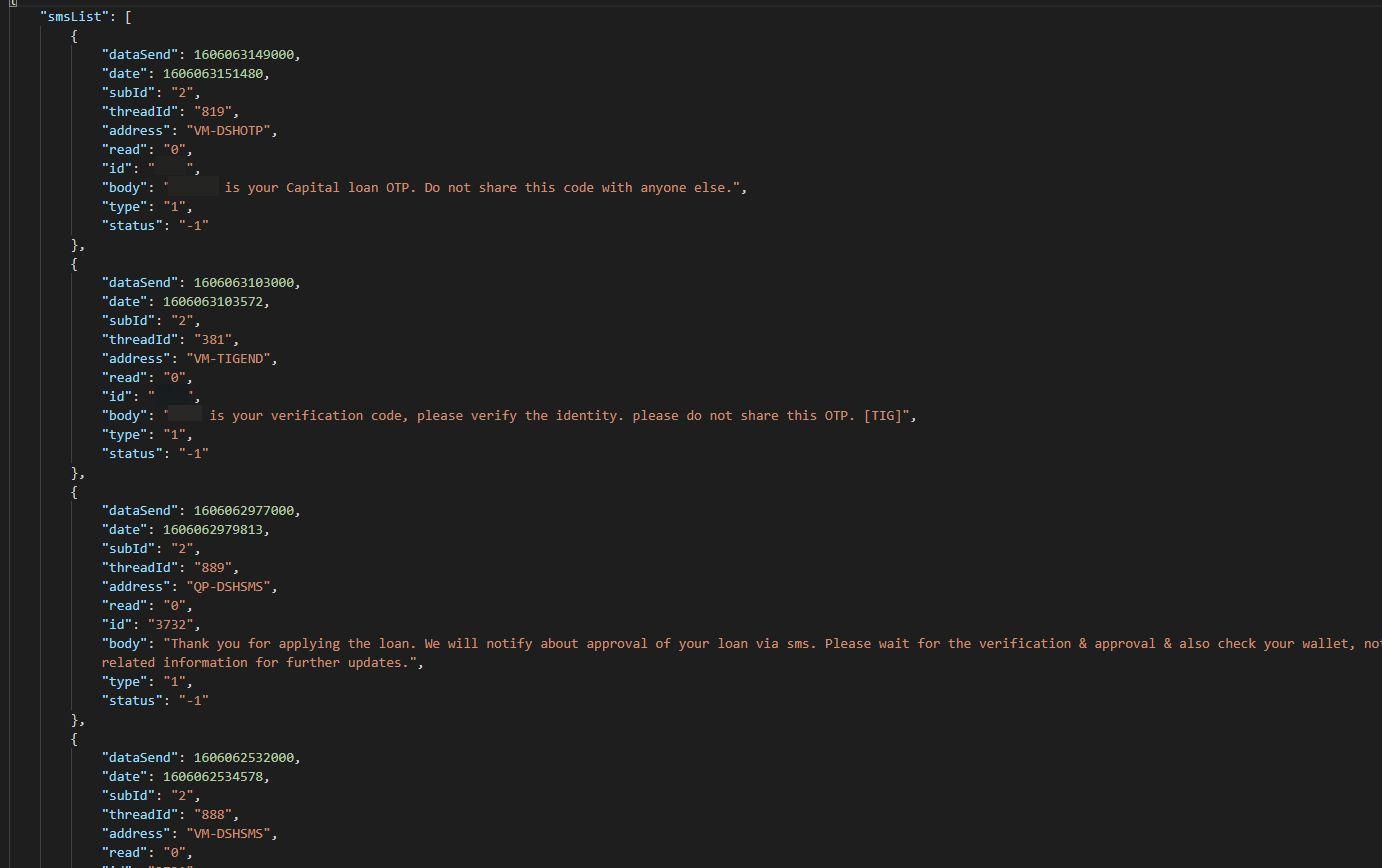
SMS information relating to LoanZone’s customers
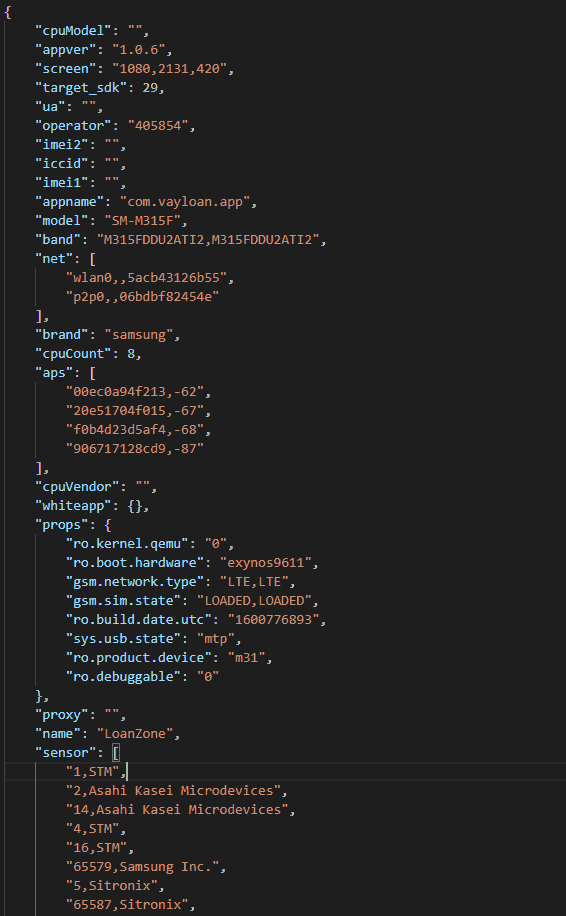
User device information found in Vayloan fingerprint data
MeraLoan contacts
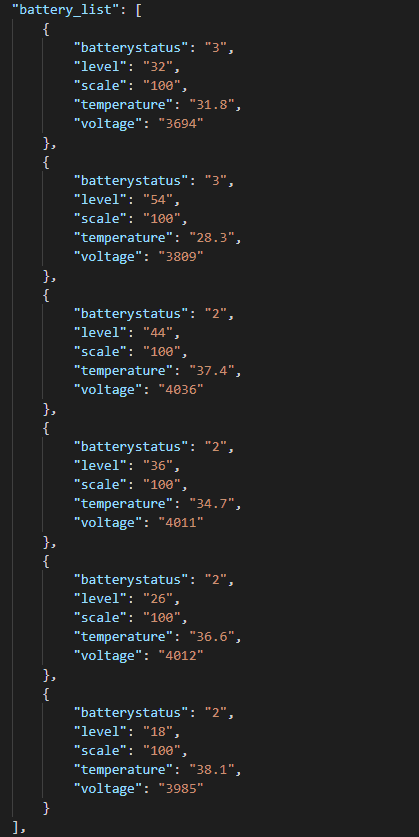
Battery status of an unidentified app’s users’ phones
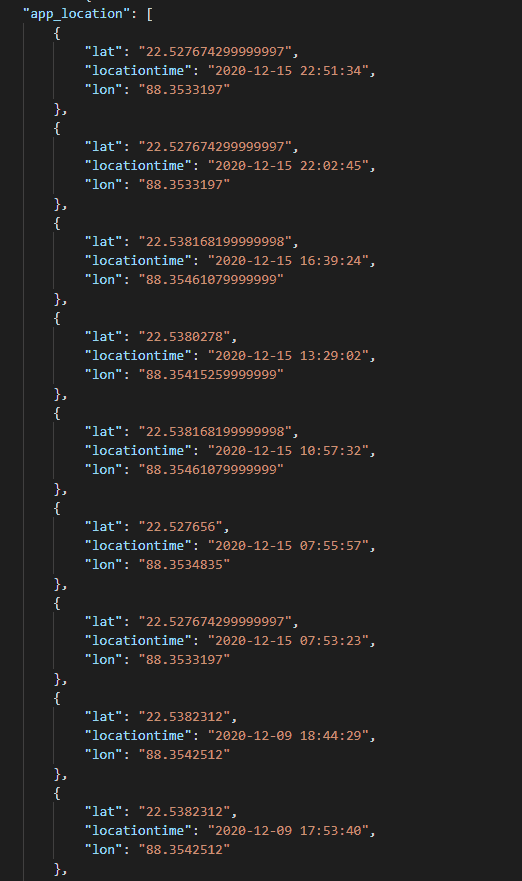
GPS location data of an unidentified app’s customers
Technical Data
Technical data was exposed in one of CashMama’s bucket’s file collections:
- Epoch files
Technical data exposed the PII and sensitive data of CashMama customers in a single dataset:
- Final stage data:
- Full names
- Dates of birth
- Ages
- Genders
- Marital statuses
- Occupations
- Salary categories
- Home addresses
- Email addresses
- PIN codes (possibly related to the service)
- Family members’ names
- Family members’ phone numbers
- Friends’ names
- Friends’ phone numbers
- GPS locations
- Loan amounts requested
Final stage data exposed CashMama users in the second stage of epoch file dumps. In other words, final stage data contained information that was both collected from users’ phones and submitted by users. This data was merged in this final stage to identify which users owned the mined data.
You can see evidence of final stage data below.
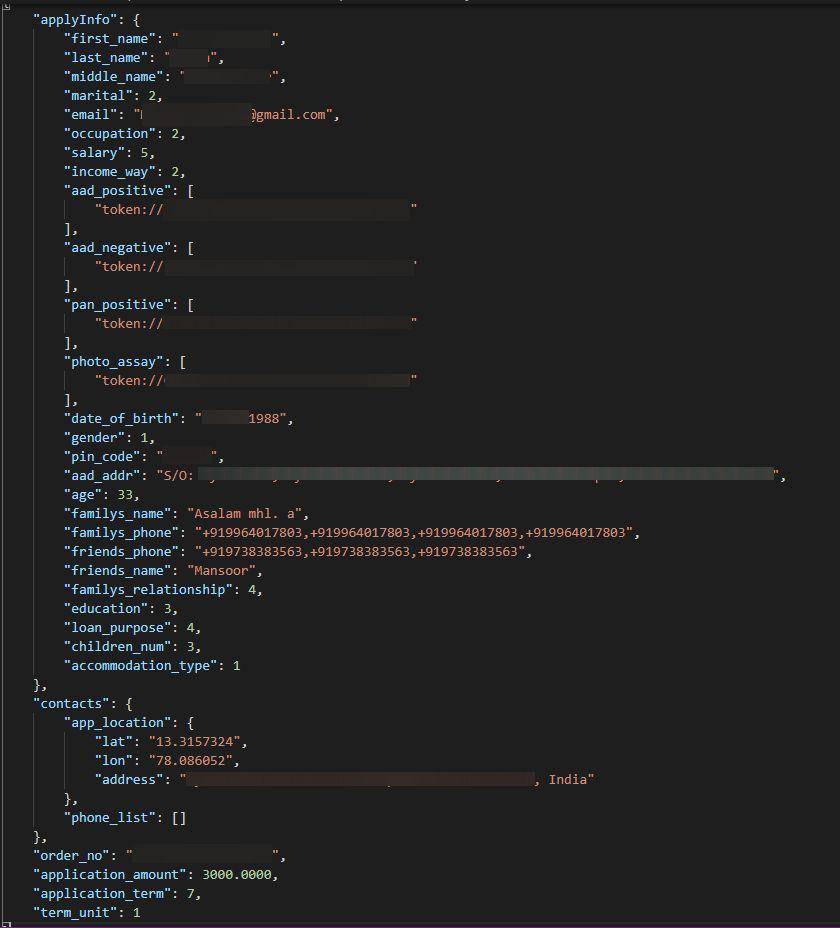
Mined data and user-submitted data combined in the final stage
CashMama’s unsecured Amazon S3 bucket wasn’t live and was not being used at the time of discovery: Files on the bucket were dated from October 2020 to April 2021.
Amazon is not responsible for the management of CashMama’s AWS S3 bucket and is therefore not responsible for this data breach.
Considering the number of unique files we observed, we estimate there are around 200,000 to 600,000 customers exposed in CashMama’s data breach.
The instant loan apps included within the bucket didn’t operate outside of India. We believe Indian citizens are the solely affected nationality based on the content of the open bucket.
You can see a full breakdown of CashMama’s data exposure in the table below.
We discovered CashMama’s open AWS S3 bucket on November 11th, 2021.
We messaged both the Indian Computer Emergency Response Team (CERT) and AWS regarding CashMama’s data exposure on November 25th, 2021. On December 16th, 2021, we sent follow-up messages to the Indian CERT and AWS. Both organizations replied to our messages and we sent a responsible disclosure to the Indian CERT in the following days.
We followed up with Indian CERT on January 10th, 2022, and CashMama’s open bucket was secured between January 11th, 2022, and January 13th, 2022.
Exposed customers could experience various impacts as a result of this data breach.
Data Breach Impact
We cannot and do not know whether malicious actors accessed the content of CashMama’s AWS S3 bucket. However, the bucket was left without password protection. Anyone who found the bucket’s URL could’ve read or downloaded its contents.
Exposed customers could experience extreme forms of cybercrime if bad actors accessed the sensitive data and PII stored on the bucket.
Identity theft is one such possibility with a wealth of personal information, photos of ID cards, financial details, and more exposed. Cybercriminals could have enough information available to know every detail of a customer’s identity, including their occupation and marital status. They could use the bucket’s information to open bank accounts in the user’s name or obtain further loans and mortgages. The money would be paid into the criminal’s illegitimate bank account and victims could be left with the prospect of financial ruin.
Phishing, scams, and fraud are other possible threats to leaked customers. Bad actors could contact customers, along with entire contact lists, using exposed contact details. Hackers could masquerade as a representative of a bank or instant loans app to convince victims to provide more personal data or to click a malicious link. Hackers could also convince victims to pay fake charges and repayments related to instant loans.
CashMama’s bucket revealed scraped SMS messages which likely detail personal preferences, interpersonal relationships, embarrassing stories, and personal secrets related to customers. Hackers could use any sensitive information to blackmail customers: threatening to post damaging information to friends, family, or online unless the victim pays a fee.
Finally, many users may have stored sensitive PII (such as social security numbers and passwords) in their contact lists. Hackers could examine contact lists to find this information. Ultimately, this data could be used to defraud exposed customers.
Preventing Data Exposure
What steps can we take to mitigate the risk of data exposure? And if we are exposed, what can one do to avoid suffering from cybercrime?
CashMama’s bucket contained data that was seemingly collected from users’ phones. We don’t know whether access to this data was granted by users in app permissions or not. If the apps did request permissions, the bucket demonstrates the extent to which apps can legally gather user data, and how this data collection can ultimately place users in danger. Users must carefully read permissions before downloading an app. Importantly, users must be able to understand the data to which each app permission grants access.
Here are a few more tips to help you prevent data exposure:
- Be cautious when providing your personal information. Make sure you trust the person, organization, or entity 100%.
- Avoid giving out your most sensitive forms of data whenever possible, including government ID numbers and personal preferences.
- Only use websites that are secure (i.e. sites with a “https” and/or a closed lock symbol in their domain name).
- Create secure passwords that use a combination of letters, numbers, and symbols.
- Don’t click links in emails, messages, or anywhere else on the internet unless you know the source is legitimate.
- Double-check your privacy settings on social media accounts: Make sure only trusted users can see your personal information and content.
- Don’t input or display your most sensitive forms of data (such as credit card numbers or passwords) when using an unsecured WiFi network.
- Educate yourself about cybercrime, data protection and the methods you can use top prevent phishing attacks and malware.
Context: What Is the Instant Loan Apps Scandal?
In late 2020, several Indian fintech companies and apps, including Onion Credit Private Limited, Credfox Technologies, and the companies’ various instant loan apps, were implicated in criminal accusations.
The accusations revealed a racket in which customers were offered loans at exorbitant interest rates and coerced into further deals with sister applications. The consequences for failure to repay one’s loan were extreme, with companies allegedly harassing, abusing, and blackmailing customers.
According to police reports, customers who used the apps uploaded a range of personal information during the application process, including PAN numbers (national IDs) and bank account information. Customers also agreed to excessive data collection in compulsory app permissions. The apps were then purportedly sharing the phone numbers of customers and their families with third parties and other instant loan apps.
Loans were issued with interest rates as high as 35% along with large processing fees and GST that could deduce around 1,200 INR (~USD 16) from a 5,000 INR (~USD 67) loan. When customers repaid their loans, they were bombarded with calls from 20-30 similar loan apps. These apps promised customers they were eligible for a new loan based on their previous loan.
Many customers continued to borrow more money, either to repay the first loan or because they didn’t cover their costs, and became embroiled in a vicious cycle of debt. Once a customer couldn’t pay, these loan apps apparently levied penalties of around 3,000 INR (~USD 40) per day. For context, the average monthly salary in India is roughly 31,900 INR (~USD 425).
Defaulters claim they were harassed constantly with abusive calls and blackmail. CashMama and its associated apps apparently messaged customers’ entire contact lists—which were seemingly scraped from phones and stored on the open bucket—defaming the victims until they repaid the loan.
Police were alerted to Onion Credit Private Limited and Cred Fox Technologies following a spate of related complaints, along with three suicides in Telangana linked to instant loan apps. Police arrested 6 people connected with the two companies in late 2020.
About Us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including 2.6 million users exposed by an American social analytics platform IGBlade, as well as a breach at a Brazilian Marketplace Integrator platform Hariexpress.com.br that leaked more than 610 GB of data.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.