
Intro
Breastcancer.org, a world-renowned breast cancer charity, has suffered a data exposure affecting users of the organization’s website.
The SafetyDetectives cybersecurity team found an Amazon S3 bucket owned by Breastcancer.org that was misconfigured, left publicly available without any authentication controls in place.
Breastcancer.org’s misconfigured bucket has therefore exposed hundreds of thousands of files containing sensitive images belonging to the website’s users. In particular, a portion of these images contained detailed EXIF data, which could potentially be used to locate and harass users.
This exposure points toward the variety of information that can be recovered from the images we post online.
Who is Breastcancer.org?
Founded in 2000, Breastcancer.org is a non-profit organization with a commitment to provide the latest scientifically-backed research on breast cancer and breast health for free through its website.
The organization hopes to empower women to make the right decisions in life, with content that simplifies a vast corpus of complex and confusing medical information.
Breastcancer.org’s published resources are fact-checked by a team of 70+ practicing medical professionals. Outside of the site’s guidance articles, visitors can also find medical news resources, videos, podcasts, webinars, peer-to-peer discussion boards, personalized content recommendations, and Spanish-language resources.
Breastcancer.org is based in Ardmore, Pennsylvania, in the United States, and receives over 28 million web visitors every year according to its website. Throughout its history, Breastcancer.org has reached 220,000 registered members and 174 million people across the world.
What was Exposed?
Breastcancer.org’s unsecured bucket exposed over 350,000 files, totaling around 150 GB of data. The bucket exposed the sensitive images of Breastcancer.org’s website users.
There were two separate datasets exposed on Breastcancer.org’s bucket:
- User avatars
- Post images
User Avatars
User avatars are profile pictures taken from the accounts of Breastcancer.org users. The bucket contained over 50,000 user avatars. Many of the avatars featured images of registered users.
While this is publicly available information, user avatars could be used in conjunction with EXIF data to identify vulnerable users.
You can see examples of user avatars in the following images.

A couple pictured in one user avatar

A man pictured in another user avatar
Post Images
Post images were uploaded to Breastcancer.org by its users. The bucket contained over 300,000 post images and EXIF data was attached to each post image. EXIF data exposes numerous details about the format of an image and the context in which it was captured.
EXIF data in post images included:
- Device details, i.e. brand and model of the camera used.
- GPS location of the captured image.
Some post images featured sensitive content that felt as though it was intended for private viewing. For example, there were results from medical tests and images of nudity (most likely taken for medical purposes) included among the files — contents that a user would not typically post publicly.
We decided to test whether post images were uploaded from public posts or private messages. We created two breastcancer.org accounts and sent an image from one account to the other. The image we sent later appeared in the bucket, confirming our suspicion that private images were exposed.
You can see evidence of post images below.

A picture of a nude woman on the bucket
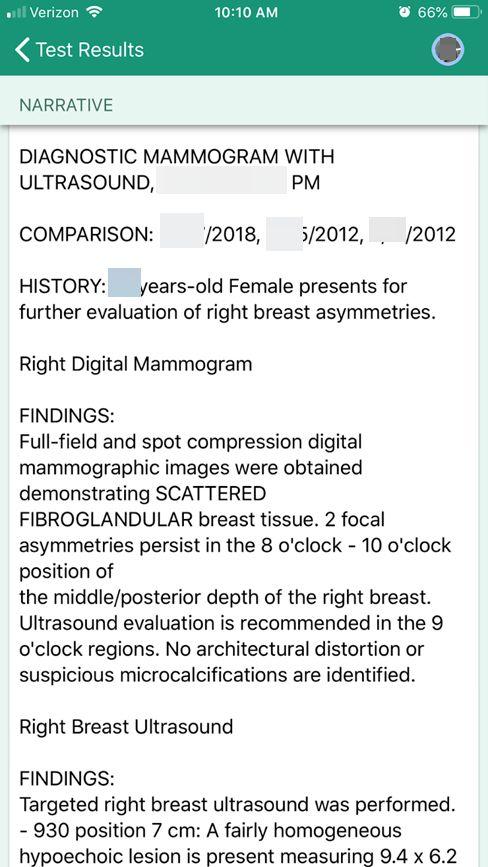
One user’s ultrasound results
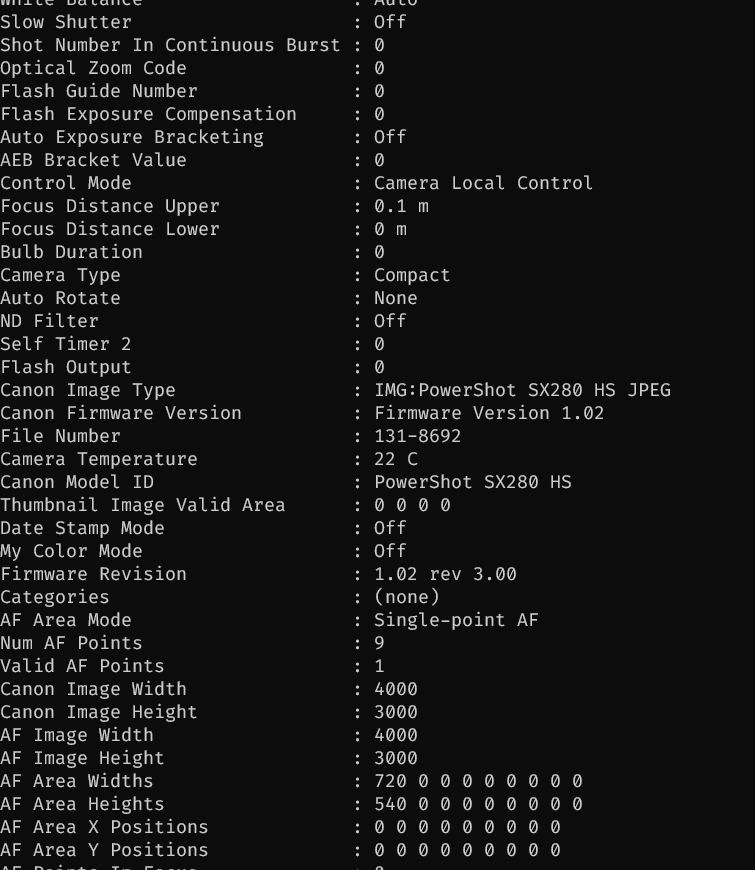
EXIF data exposed a range of info specific to each image
Breastcancer.org’s open bucket was live and being updated at the time of discovery.
It is important to note that Amazon doesn’t manage Breastcancer.org’s bucket and this misconfiguration is not Amazon’s responsibility.
Breastcancer.org reaches users around the world and we’d expect there are a significant number of American and European users with images on the bucket.
The Breastcancer.org website suggests it has over 200,000 registered users, though, it seems unlikely that all of these users are exposed based on the bucket’s files. There are over 50,000 user avatars on the bucket, so 50,000 should stand as a minimum estimate of the number of users exposed.
The number of exposed people could be higher, however, considering that users could be exposed in post images even if their user avatar is not included on the bucket.
You can see a full breakdown of Breastcancer.org’s data exposure in the table below.
We discovered Breastcancer.org’s unsecured bucket on November 11th, 2021. It contained files dating back to April 2017, though, filenames suggest some of these images date back to 2014 and were migrated to the bucket in 2017. We saw recent files on the bucket, too, dated mid-November 2021. This suggests the bucket was still in use when we found it.
On November 17th, 2021, we messaged breastcancer.org regarding its data exposure. We sent another message to both newly-found and previously-contacted people from the organization on November 21st, 2021. We didn’t receive a reply and on December 14th, 2021, we sent further messages to AWS, the US Computer Emergency Response Team (CERT), and additional breastcancer.org employees regarding this data exposure.
We found the bucket secured on May 4th, 2022.
Breastcancer.org and its users could experience various impacts as a result of this incident.
Data Exposure Impact
We cannot and do not know whether malicious actors accessed the content of Breastcancer.org’s S3 bucket. With no security controls in place, hackers and cybercriminals could have read or downloaded the bucket’s images. This data could be used to subject users to criminal activities.
Breastcancer.org may also face legal implications for the status of its AWS S3 bucket.
Impact on Users
Exposed Breastcancer.org users could experience forms of harassment if hackers accessed the bucket’s data.
There are no contact details belonging to users exposed on the open bucket. However, cybercriminals could target EXIF data to identify users. A picture of a person’s house, for example, could be used to locate that person if geolocation data is attached.
Malicious actors could identify vulnerable users to launch vicious and spiteful attacks against them. Hackers could reference a person’s medical condition or nude images to berate them with hurtful comments. With GPS locations exposed on the server, online harassment could spill over into the real world.
Impact on Breastcancer.org
Breastcancer.org may be investigated by data protection authorities in several jurisdictions for exposing users’ data. It’s more than likely Breastcancer.org has users from nations around the world exposed on the bucket. However, we won’t check the location data of exposed photos for ethical reasons.
Breastcancer.org could come under the scrutiny of the Federal Trade Commission (FTC) if the organization has mishandled the data of US citizens. The FTC protects consumers from unfair or deceptive business acts or practices. Any breach of the FTC Act could land Breastcancer.org with a maximum penalty of US$100 million or the imprisonment of guilty individuals in severe cases.
Preventing Data Exposure
What steps can users take to mitigate the risk of data exposure and cybercrime?
Here are a few tips to prevent data exposure:
- Only provide your personal information to companies, organizations, and entities that you trust 100%.
- Only visit websites with a secure domain name (i.e. websites that have a “https” and/or closed lock symbol at the beginning of their name).
- Be especially vigilant when providing your most sensitive forms of data, such as your social security number.
- Create super-strong passwords that use a mix of letters, numbers, and symbols, and update these passwords regularly.
- Don’t click a link online unless you’re certain the source is legitimate. This includes links in emails, messages, or phishing websites that are masquerading as a legitimate domain.
- Edit your privacy settings on social media sites. Your social media accounts should only display content to friends and trusted users.
- Avoid displaying or typing important and highly-sensitive forms of data (such as credit card numbers or passwords) when connected to a public or unsecured WiFi network.
- Educate yourself about cybercrime, data protection, and the methods that reduce your chances of falling victim to phishing attacks and malware.
About Us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including 2.6 million users exposed by an American social analytics platform IGBlade, as well as a breach at a Brazilian Marketplace Integrator platform Hariexpress.com.br that leaked more than 610 GB of data.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.