
Intro
The Safety Detectives cybersecurity team discovered a substantial data leak affecting an anonymous Chinese ERP software provider and exposing European customers.
The unclaimed ElasticSearch server has exposed more than 300,000 records, equating to around 500MB of data. This breach primarily affects eCommerce buyers, although some eCommerce sellers may be at risk too.
What Do We Know About the Company?
The server owner is, at the time of publication, unknown. We believe that the server belongs to a Chinese tech company operating an ERP platform — this caters to eCommerce businesses selling on sites like Amazon and Shopify.
“ERP” stands for “enterprise resource planning.” ERP platforms allow users to manage several aspects of their business; from accounting to procurement, project management, risk assessment and compliance, as well as various supply-chain-related operations. Such platforms help retailers manage the day-to-day operations of their business in real-time.
In short, ERP software makes life easier for business owners by integrating multiple processes into one simple program.
References throughout the server indicate that the ERP services are provided by a Chinese company. All of the products we saw while investigating the server appear to be Chinese exports and many of the database’s logs are written in Chinese, too.
Subsource information confirms that the data has been collected by an ERP platform.
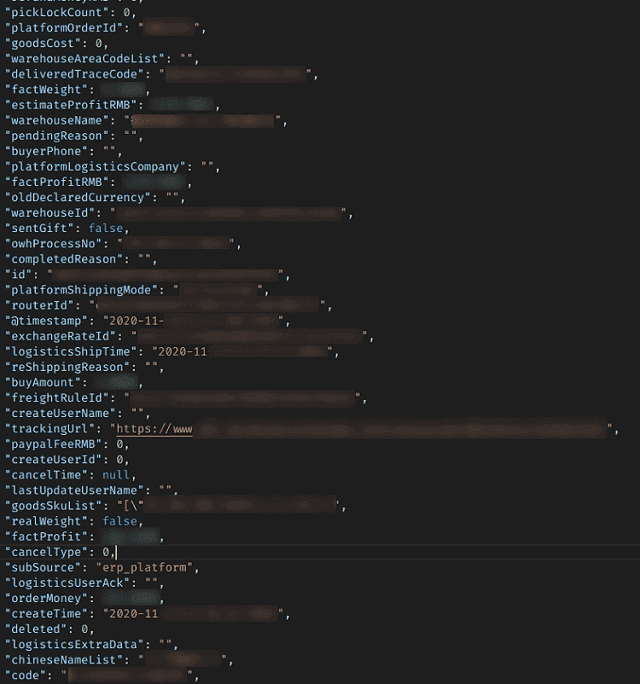
Subsource fields and various references provide limited company information
What Was Leaked?
The ElasticSearch server, hosted by Alibaba Cloud, was left unencrypted without password protection in place. It exposed 329,144 sensitive records totaling around 500MB of data.
The server’s content primarily leaks data for eCommerce buyers, i.e. the shoppers purchasing products from businesses using the ERP platform.
160,036 payment records leak various forms of buyer PII through purchase logs and featured invoice links. Leaked buyer data includes:
- Buyer names
- Phone numbers
- Email addresses
- Delivery addresses
- Billing addresses
- Ordered items
- Prices paid
The server leaked delivery information, too, which could place both eCommerce buyers and sellers at risk. Exposed delivery details include:
- Courier service names
- Order tracking URLs & tracking codes
- Shipping times & dates
The logs and invoices also exposed some data for eCommerce sellers using the ERP platform, such as:
- Seller names
- Seller email addresses
- Billing information; leaked products sold, product prices, and time of sale
- Estimated profits; from each sale
While the server seems to belong to a Chinese tech company, much of the buyer data exposed in its purchase logs belongs to European customers. The PII of Danish and French eCommerce buyers could be found amongst the records, and German eCommerce customers featured prominently on the database.
Evidence of buyer PII (names, purchase details, contact information, and addresses) can be seen in the following screenshots.
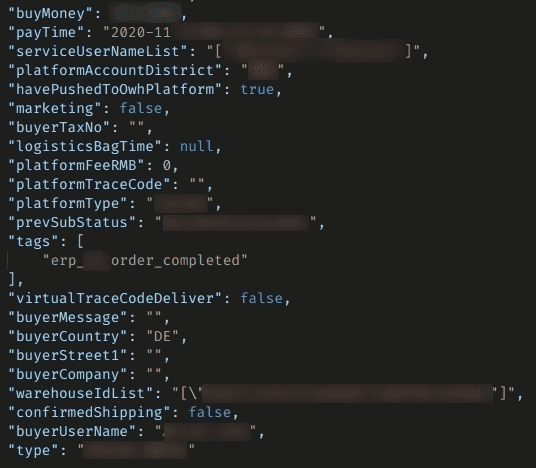
A German buyer’s name and purchase details feature on the server

Buyer phone numbers are visible
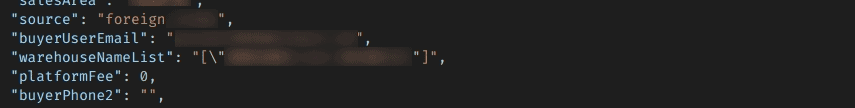
Buyer email addresses can also be found in the server’s logs
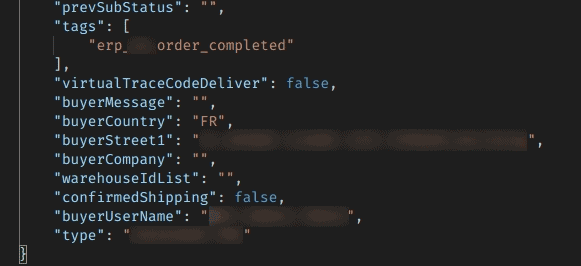
The delivery address for a French buyer
Leaked delivery information includes a range of sensitive data regarding couriers and the status of eCommerce buyers’ orders. You can see evidence of delivery information below.
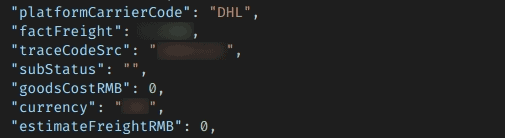
“DHL” is named as the courier for several orders
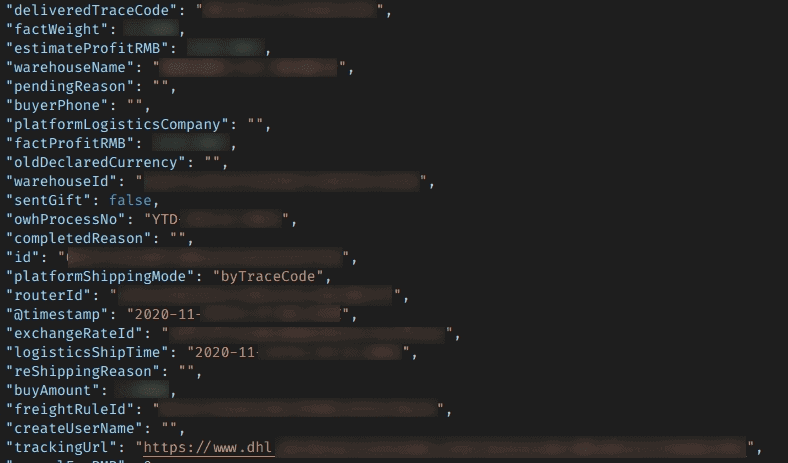
Tracing codes, tracking URLs, and shipping dates & times are on the server
Most of the leaked information relates to eCommerce buyers, though, exposed seller names, email addresses, and “estimated profit” information affects eCommerce vendors using the unknown ERP platform.

“PlatformAccount” fields show email addresses for ERP users
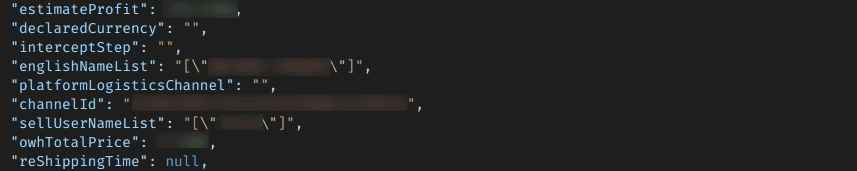
“EstimateProfit” and “SellUserNameList” fields leak the personal and business information of sellers
As mentioned, the open ElasticSearch server’s purchase logs contained numerous links to invoices.
These invoices exposed both buyer and seller PII, including names, billing, and delivery addresses for buyers and the names and addresses of sellers. Purchase information has also been leaked, including products purchased and prices paid. This could impact both buyers and sellers.
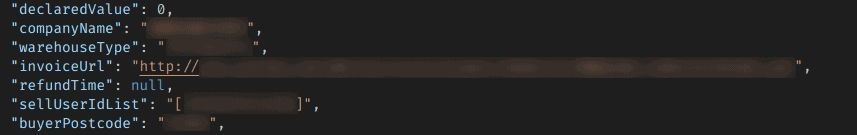
Links to invoices can be accessed in the server’s logs
An invoice from the anonymous server
You can find a full breakdown of this data breach in the table below.
We discovered the open ElasticSearch database on July 25th, 2021. The content of the server seems to have been exposed since November 2020.
We reached out to the Alibaba Abuse Department regarding this data breach. Alibaba didn’t reply, even after we sent a follow-up message, and we later contacted German CERT who replied to our message promptly. German CERT was also unable to reach the hosting provider.
In order to help close this breach, we contacted some of the leaked ERP customers found within the content of the open Elasticsearch database. We did not receive a reply from any of these people.
Data Breach Impact
A data breach of this magnitude leaks information for thousands of people. We cannot know whether hackers have accessed the server’s content.
The majority of the server’s data belongs to eCommerce buyers. This group stands to face the highest amount of risk if hackers accessed the server’s logs. Users of the ERP platform (eCommerce sellers) are also at risk of this data breach, while the unnamed ERP platform will likely face legal implications once it has been identified.
Here are some of the cyber threats eCommerce buyers and sellers may face.
eCommerce Buyers
The PII of eCommerce buyers are leaked from a third party, and moreover, one that is anonymous. This means it’s unlikely buyers will find out their data has been leaked.
Still, eCommerce buyers could suffer a variety of criminal activities — knowledge of the strategies employed by bad actors could prove crucial in identifying and nullifying the threat of cybercrime.
Phishing is one such method cybercriminals can employ with the leaked data. Phishing attacks are a type of social engineering attack where cybercriminals attempt to coerce further sensitive data out of victims or install malware onto the victim’s device to supplement additional crimes.
Specifically, hackers could contact users via phone or email, referencing the user by name to establish trust. The attacker could pose as an eCommerce seller, referencing the user’s order details to build a narrative around the reason for communication. They may say that the buyer has been overcharged, for example, and that the buyer can claim a refund by clicking a link or providing card details. In reality, any one of several narratives could be used by the hacker. Once the user clicks the link, malicious files could be installed on the user’s device.
Other types of fraud & scams are also a possibility. Phishers could conduct fake invoice scams with the wealth of order details available on the server. This involves sending a fake invoice to the user for their purchase. From here, the hacker could convince the user that the original payment was unsuccessful, and the victim must pay the invoice to avoid any issues.
Home addresses are available on the database too. This makes home invasion/burglary a real possibility if PII is sold on to other criminals. Thieves may target users who make high-value orders in the hope the victim’s house is full of expensive goods.
Theft of ordered goods is another risk associated with leaked order details. Tracking links, shipment times, courier information, delivery addresses, and order information provide criminals with enough data to intercept and steal a user’s ordered goods. This could place users in close contact with criminals as well, which is dangerous.
ERP Users (eCommerce Sellers)
Theft affects eCommerce sellers, too. Ecommerce sellers would likely have to shoulder the financial burden of stolen goods — reimbursing users with new products or refunds. Entire shipments of orders could be intercepted at once, and couriers may have to deal with assailants face-to-face.
Elsewhere, exposed users of the ERP platform could be at risk of snooping and business espionage.
For a start, the ElasticSearch server has already exposed a variety of details for eCommerce sellers: product lists, price lists, profit information, and customer lists. Rival businesses could acquire the server’s content and gain insight into other eCommerce sellers. In particular, customer lists, products, and prices paid could be used to prospect customers of eCommerce sellers and undercut their prices — stealing their trade.
Rival companies could also conduct business espionage. Rival companies could contact eCommerce sellers via email, posing as a customer or colleague. This rival could address the seller directly, referencing order/shipment details to build trust. Eventually, the offender may attempt to pry industry secrets from the eCommerce seller. Details they could use to gain a competitive advantage.
ERP Platform
Finally, the ERP Platform that leaked eCommerce buyer and seller data will, in all likelihood, come under the scrutiny of data protection legislation.
Most of the server’s data belongs to citizens of EU member states. The EU’s data protection laws are called GDPR. The EU can act outside of its jurisdiction whenever the data of EU citizens is mishandled. Therefore, GDPR could hand a maximum of up to €20 million to the ERP platform, or 4% of the company’s annual turnover (whichever is greater).
While we do not know for certain, the server also seems to be operated by Chinese owners. This means that Chinese data protection authorities could, potentially, investigate the ERP platform’s leak.
China’s Cybersecurity Law outlines maximum fines of up to RMB 1,000,000 ($155,000) for companies that mishandle consumer data. Guilty individuals could also face additional fines between RMB 100,000-1,000,000 and even imprisonment.
Ultimately, any legal fallout or public knowledge of the Chinese ERP platform’s inadequate data handling practices may reflect poorly on its business. Once the anonymous provider is identified, existing and potential customers alike may choose to avoid the ERP platform for fear of having their data leaked.
Preventing Data Exposure
What steps can we take to avoid data exposure and the damaging after-effects of a data leak?
Here are a few tips to prevent data exposure:
- Only provide your personal information to trustworthy companies/individuals.
- Only visit secure website domains. Secure domains begin with ‘https’ and/or a closed lock symbol.
- Be cautious when asked to provide the most important forms of personal information (keep government ID numbers and personal preferences to yourself).
- Create secure passwords. Use a combination of letters, caps, numbers, and symbols when creating a password. Update your passwords regularly.
- Don’t click a link in an email, SMS message, or otherwise, unless you can be 100% sure the sender is legitimate.
- Edit your privacy settings on social media. Your accounts should only display your content and personal details to trusted users and friends.
- Limit the information you display when connected to a public Wi-Fi network. Typing out credit card details should be avoided at all costs.
- Use online sources to learn about cybercrime, data protection, and the steps you can take to avoid phishing attacks and malware.
About us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including some 200+ million users exposed by Chinese social media management company Socialarks, as well as a breach at major cosmetics brand Avon that leaked more than 7 GB of data.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.