
The SafetyDetectives research team discovered a significant data leak affecting the Brazilian software company WSpot.
WSpot provides a WiFi management solution that allows businesses to control various functions of their on-premises WiFi network and router.
WSpot’s misconfigured Amazon S3 Bucket was left in open form, exposing the sensitive information of potentially millions of Brazilian citizens.
Who Is WSpot?
WSpot helps businesses manage and enhance the functions of their WiFi network and router through the WSpot web portal.
The product is a “WiFi management software.” It provides added security and control for businesses that allow guests to connect to their WiFi without a password. Customer authentication via a captive portal, enhanced data collection, and customizable bandwidth limits are just three of the services available to users.
WSpot is based in Campinas, Brazil, and has some high-profile customers, including Sicredi, Unimed, and Pizza Hut.
Visitor Data Leaked
WSpot’s data breach has compromised over 226K files totaling 10GB of data. Among logs on these files is an array of sensitive and personal data relating to WSpot’s clients and their visitors.
Amazon does not manage WSpot’s server and isn’t responsible for its configuration. Amazon only provides the platform for WSpot’s responsible data storage, and the Amazon S3 Bucket server was left without any authentication procedures in place.
We discovered two different file types exposed on the open database — SMS logs and guest reports. There may be more information exposed that was not visible in our sample data.
84MB of files containing SMS logs were found on WSpot’s database. There were an estimated 280,000 total log entries of this type.
SMS logs leaked two forms of personal and confidential visitor data. This data belongs to the people that connected to each WSpot client’s WiFi:
- Email addresses
- SMS contents; including user passwords that were disclosed via SMS
SMS logs leaked another form of data relating to WSpot clients:
- Company names
A minimum of 550MB of guest reports in “.csv” format was also exposed in this data breach. That posits an estimated total of 2.5 million log entries, though, a portion are thought to be duplicates.
Exposed guest reports reveal several different types of visitor PII. This PII belongs to citizens that connected to each WSpot client’s public WiFi:
- Full names
- Email addresses
- Phone numbers
- Genders
- Dates of birth
- Addresses and postal codes; Brazilian postal codes are named “CEP” numbers
- CPF numbers; e. Individual taxpayer numbers
An exact estimate of the number of affected people is difficult given the presence of duplicate files and log entries. An estimated 2.5 million Brazilian citizens may be affected by this data breach.
SMS logs leak account credentials. These records show messages containing plaintext login details — information sent to people who were registering their WSpot accounts. This practice is referenced as a feature on WSpot’s website (“credentials via SMS”).
You can see evidence of SMS logs in the screenshot below.
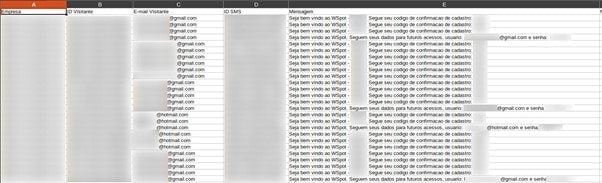
SMS logs contain emails and passwords in plain text
Spreadsheets of guest reports in “.csv” format appear to be website logs created and maintained by each WSpot client’s WiFi router. The IP addresses of users featured on the records are all local IP addresses — this suggests they were collected by routers within a private network to identify user devices. The presence of MAC addresses within the records — network card IDs that are only known to devices within a local network — confirms this suspicion.
You can see evidence of guest reports in the following image.
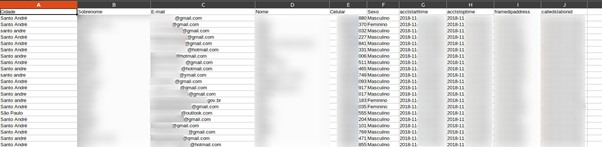
Guest reports contain a range of PII
Some guest reports featured visitors’ answers to custom questions on registration forms, as well as visitors’ dates of birth. This information was likely collected by WSpot’s software to create a database of visitors. Just like the other records of guest reports, all of the listed IP addresses are local and only known within local networks.
You can see evidence of guest reports that feature visitors’ answers below.

Certain guest reports leak dates of birth and question answers.
The following table provides a full breakdown of this data breach.
The SafetyDetectives research team found the server on September 2nd, 2021. WSpot’s unprotected Amazon S3 Bucket was live and being updated at the time of discovery.
After discovering WSpot’s database, the SafetyDetectives research team sent a responsible disclosure of the data breach to WSpot on September 7th, 2021. A follow-up message was sent a day later to which WSpot replied, securing the breach on September 8th, 2021.
WSpot’s exposed Amazon S3 Bucket database has affected a large number of people, and all parties could face various criminal risks given the nature of its leaked content.
Data Breach Impact
Affected parties could face several cyber risks should hackers have accessed the content of the unprotected S3 Bucket.
We cannot know whether hackers have accessed the server. However, with inadequate security procedures in place, unethical hackers could have found the server and could have easily read or downloaded its data.
In this case, Brazilian citizens, WSpot clients, and WSpot must understand the risks they may face.
Brazilian Citizens
First and foremost, the guests of WSpot clients have had their data exposed. The affected parties all reside within Brazil, which is where WSpot offers its services.
Most of the server’s content supposedly relates to members of the general public who have connected to each client business’ WiFi router — routers that are managed through the WSpot platform.
Affected citizens could face scams, phishing attempts, and account takeovers.
Scams
WSpot’s database leaked the email addresses and phone numbers of Brazilian citizens. As such, bad actors could contact people to target them with scams and fraud.
Attackers could launch popular scams using visitor PII to appear trustworthy. For example, in a COVID-19 vaccine scam, attackers may reference someone’s leaked name and date of birth to notify the victim that they are eligible for a vaccine. The attacker may then ask for some form of payment, with no vaccine or vaccination appointment transpiring as a result.
Phishing & Malware
Similarly, hackers may target leaked citizens with phishing attacks. Phishing attacks are a type of scam that attempts to convince the victim to reveal sensitive information or click a malicious link. Phishers will often use this information to supplement scams, fraud, and various other cybercrimes in the future.
Again, hackers could appear trustworthy by referencing the user’s personal data during initial communications. They could pose as a representative of one of the businesses exposed on WSpot’s S3 Bucket.
Attackers could reference products, services, refunds, or other common topics to build a narrative around their reason for communication. Once phishers have built an element of trust, they will try to convince the victim to provide information or click a link. Such links can contain malware and, once clicked, this malware could be downloaded onto the victim’s device — allowing criminals to steal more information to supplement further attacks and/or compromise user accounts.
Account Takeover
SMS logs contained SMS messages which, if accessed by criminals, reveal credentials for user accounts.
Hackers could use passwords in combination with email addresses to gain access to separate accounts of users on various other platforms. For example, a leaked person on the server may use the same email-password combination to sign into their online financial account.
Should hackers input each user’s credentials across countless platforms and websites, they may well gain access to other accounts, along with any assets or data contained within them.
Impact on WSpot Clients
It’s worth mentioning that WSpot clients (the businesses with leaked visitors on the database) could face security risks of their own.
These leaked businesses could encounter similar scams and phishing attempts using the details of their visitors. Bad actors could contact businesses while appearing as a customer that visited the store in the past, referencing their experience or the business’s service as a reason for their communication.
Attackers could also appear as a representative of WSpot, referencing the user list or general business between the two companies. The ultimate goal of the attacker, of course, would likely be to collect information or conduct fraud.
Business espionage is another possibility. WSpot clients have had their business names and a list of their guests leaked with contact details and other forms of PII available. Rival businesses may gain access to the server’s contents, targeting the visitors of WSpot clients with offers and deals in an attempt to steal their trade.
Impact on WSpot
WSpot has mishandled the data of citizens and clients by failing to secure its Amazon S3 Bucket server. WSpot could face various penalties and damages as a result of this data breach.
LGPD Violations
WSpot’s website outlines that the company is in line with Brazilian digital rights laws (Marco Civil da Internet) and the new Brazilian data protection laws (LGDP). However, Wspot may come under the scrutiny of LGDP for leaking user data.
Brazil’s General Data Protection Law is officially known as Lei Geral de Proteção de Dados (LGPD). This law came into effect in late 2020. LGDP protects the data of Brazilian citizens from being mishandled or misused by the businesses or persons who collect and use this data.
Companies that mishandle the data of Brazilian citizens may have to pay sanctions. The maximum fine for a breach of LGPD is 2% of the guilty company’s revenue from the previous year, up to a total of 50 million Brazilian Reals (~$10 million).
Loss of Business
WSpot could potentially experience a loss of business due to this data breach. This is quite a common occurrence for companies that suffer a data leak.
Companies can lose trade from any system downtime related to a data breach. Reputational damage is another possibility for WSpot. Data breaches are not seen in a positive light by other businesses and members of the public. Data security is an aspect of WSpot’s service, too, which may be undermined by this data breach.
Current clients could cease trade with WSpot due to concerns about the security of their data. Potential clients may choose a rival business over WSpot for the same reason.
Competition Espionage
Rival businesses of WSpot that gain access to the leaked list of WSpot clients could prospect these businesses with their own WiFi management solution. Wspot clients could be open to using a new solution for the above-mentioned reasons.
Rival businesses could also contact WSpot posing as one of the company’s clients or indeed a fellow WSpot employee. Callers could reference clients to build trust. From here, rival businesses could attempt to coerce information from WSpot employees, such as industry secrets and insider information on their business.
Preventing Data Exposure
What can we do to protect our data and minimize the risk of cybercrime?
Here are some ways you can avoid data exposure:
- Only provide your personal information to individuals and companies whom you trust.
- Only visit secure websites. Secure websites have domain names that begin with ‘https’ and/or a closed lock symbol.
- Be extra careful when asked to provide the most important forms of personal information (i.e. social security numbers, government ID numbers, and personal preferences).
- Create super-strong passwords using a combination of letters, capitals, numbers, and symbols. Update your passwords regularly.
- Do not recycle passwords across services. Use a password manager if necessary
- Don’t click links in emails, SMS messages, or anywhere else on the internet unless you are completely certain that the source/sender is genuine.
- Edit your social media privacy settings. Your accounts should only display your content and personal details to trusted users and friends.
- Limit the tasks you perform and the information you display when connected to public Wi-Fi. For example, do not purchase a product and type out your credit card details on public WiFi.
- Use online sources to learn about cybercrime, data protection, and the steps you can take to avoid phishing attacks and malware.
About us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including some 200+ million users exposed by Chinese social media management company Socialarks, as well as a breach at Brazilian eCommerce integrator platform Hariexpress that leaked over 1.75 billion records.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.