
The SafetyDetectives cybersecurity team found an unsecured Microsoft Azure Blob Storage server belonging to retail outlet Raven Hengelsport (otherwise known as Raven Fishing B.V.), with PII for hundreds of thousands of customers left potentially vulnerable to hackers.
Primarily located in the Netherlands, Raven is a store specializing in fishing tackle and equipment. The company has leaked a massive amount of data, with 450,000 logs of customer information on the open database equating to some 18GB of data.
Who is Raven Hengelsport?
Operating within the fishing tackle retail market, Raven sells an extensive range of products to customers across the Netherlands and Europe. The Raven.nl website serves as a supermarket for fishing enthusiasts, supplying everything from expected goods such as rods, reels, and tackle boxes, to more all-encompassing products like tents, boats, and clothing items.
Raven Hengelsport is headquartered in Dronten, Netherlands, not far from the Dutch capital city of Amsterdam. While Raven.nl offers a wide range of products online, the company also has several major stores dotted throughout the Netherlands and the rest of Europe.
Raven is a medium-sized business with more than 100 employees and a sizable annual revenue of around $20 million (as per zoominfo).
Raven’s online platform delivers products to various countries throughout Europe, even operating as a vendor on Amazon’s Danish store. Though, most of the sensitive information on the unsecured Azure Blob Storage server seems to relate primarily to Raven’s business that is conducted with Dutch citizens.
Customers who are located in various other EU nations are included on the database too, with Raven’s business extending to France, Belgium, and Germany amongst others.
We know that the server belongs to Raven.nl as the same files can be seen in the open Blob Storage as can be identified on the Raven.nl website.
What was leaked?
An estimated 450,000 records were leaked by Raven Hengelsport’s open Azure Blob Storage server, equating to roughly 18GB of data.
These files contained records that consisted of two different data sets, order details and logs of PII, both of which expose the sensitive personal information of Raven’s customers:
- Order details from Raven.nl – containing customer IDs, delivery dates, discounts, shipping fees, payments, and shipment tracking numbers.
- Customer PII – names, surnames, addresses, genders, phone numbers, email addresses, and even the titles of some customers’ businesses were also leaked.
There were around 3,000 rows of information containing the online order details of customers, evidence of which you can see below.
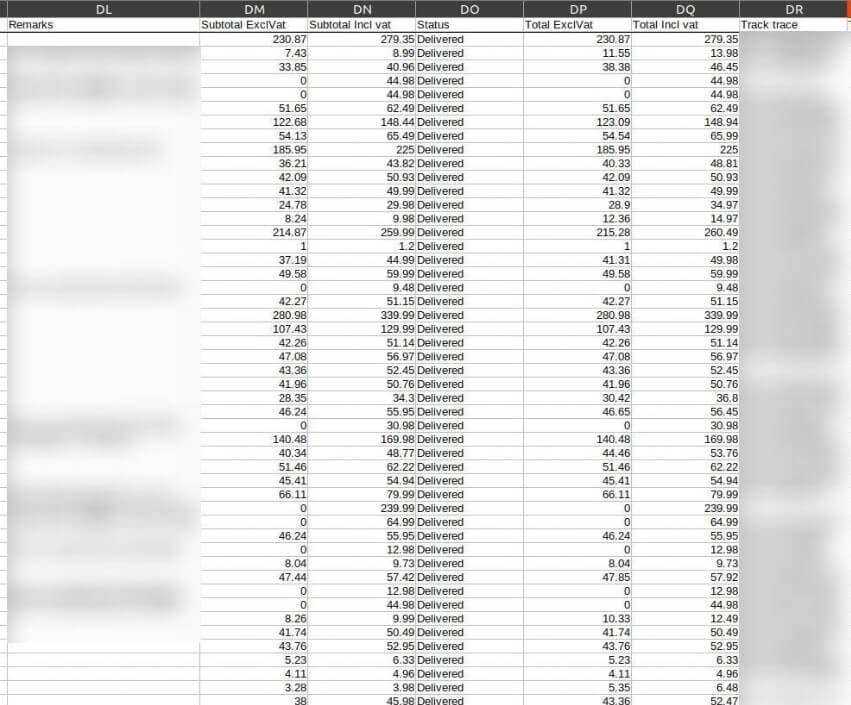
The vast majority of leaked records on the server consist of general customer details, with 425,000 of these records leaked in total.
PII details of customers were leaked amongst numerous rows of data, some of which even outlined the titles of certain customers’ businesses.
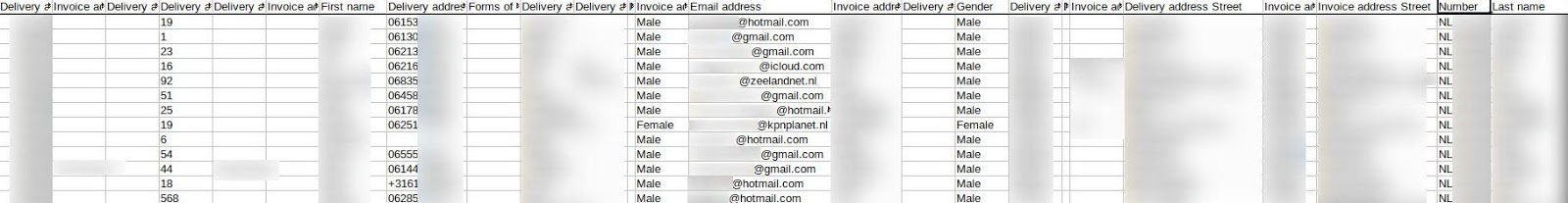
Customer PII could be found in tables.
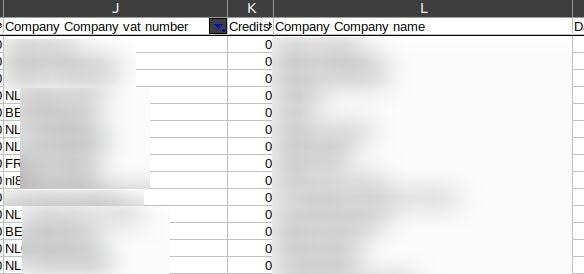
Company details have also been leaked.
The end of the table shows over 425,000 logs were leaked in total.
While more than 425,000 records containing general PII were leaked, in addition to thousands of other logs, our research shows that not all of the customer records included in the database were unique. It’s therefore likely that there was more than one log of data for each customer stored on the open server. Despite over 450,000 total records, only 246,000 of the email addresses featured on the database were unique. It’s sensible to suggest that at least 246k people are affected, given the number of unique email addresses featured on the server.
The server is located in the Netherlands, which is where Raven Hengelsport is situated. This breach primarily affects Dutch citizens, whose information makes up the bulk of the leaked records.
Though, various logs contained the data of European citizens from nearby countries, including (but not limited to) Belgium, France, Denmark, and Germany.
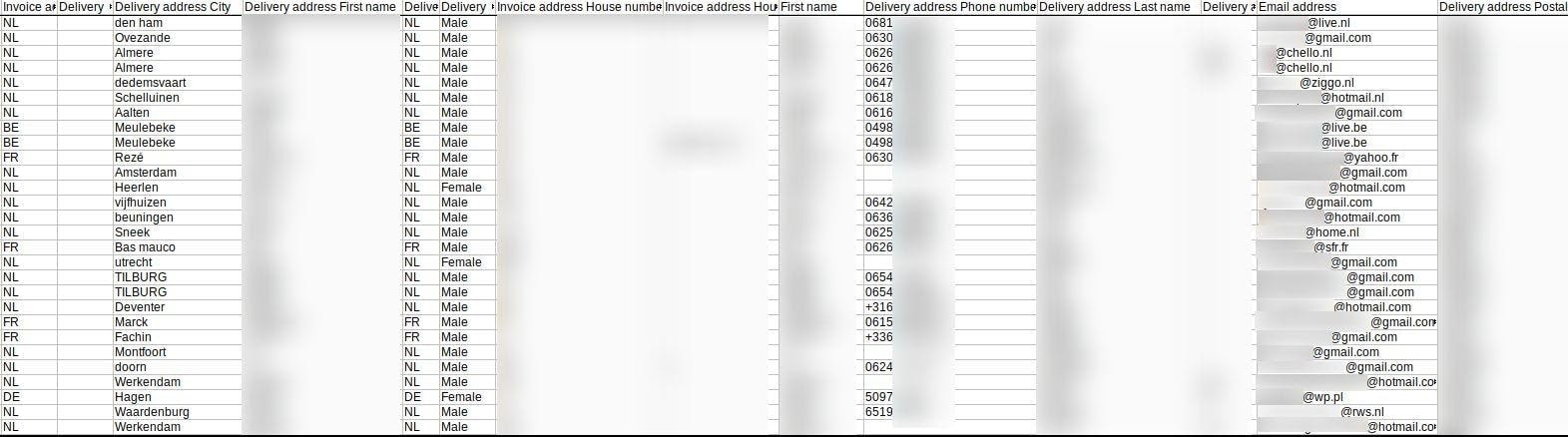
The Information of Various EU Customers Is in Leaked Records.
You can see a full breakdown of the Raven Hengelsport data breach in the table below.
Raven’s open Azure Blob Storage server was found on March 10th, 2021.
We immediately tried to get in touch with Raven once we discovered the open database, but did not receive a response from Raven regarding the breach.
We later attempted to contact Raven through the live chat feature on their website. On the first attempt at reaching Raven here, Raven’s customer support agent ended the live chat without responding to our message.
On the second attempt, we were connected with the same member of staff who told us that they couldn’t give us further contact details. We were informed that our request would be passed onto the relevant parties and we should be contacted if Raven saw fit.
We also submitted a report to the Microsoft Security Response Center (MSRC) about its customer’s (Raven’s) security breach. Since the security issue did not affect or abuse Microsoft Online Services directly, MSRC decided not to take any action on the open server.
We contacted Microsoft Customer support to see who could help us inform Raven about the data leak, although Microsoft Customer support ultimately was not helpful either.
A few months later after several additional attempts, a representative from Raven finally got back to us and the data was secured.
Data Breach Impact
A data breach of this nature has damaging consequences, both for Raven Hengelsport and for the innocent customers who have had their data leaked.
Raven will likely come under scrutiny from the EU’s data protection laws (GDPR), which could land the company with a fine of up to €20 million, or 4% of Raven’s annual turnover (whichever is greater).
Though, this is the maximum fine for a data breach. Small or medium-sized businesses are likely to receive a more lenient penalty should GDPR decide to issue sanctions.
The breach significantly affects a portion of Raven’s customer base as well, not to mention a significant number of the Dutch population. Hackers may have accessed personal information that was left unsecured on Raven’s server, meaning some Raven customers may be vulnerable to several different types of cybercrime.
Hackers could launch scams and fraudulent attacks with something as simple as an email address or phone number, building trust with the victim’s PII and eventually convincing them to hand over money or additional forms of sensitive personal information. Banners for the Raven website could also be found on the database, which may allow bad actors to create a fraudulent copy of Raven’s online store.
Cybercriminals could use leaked PII, along with details about orders/order fulfillment, to pose as a representative of Raven Hengelsport. Customers who’ve had their business names leaked could even be targeted by scams tailored to their specific trade or field of business.
Hackers can also send targeted emails to victims, again building trust with PII to convince the customer to click a link. This is called a phishing attack. Once the victim has clicked on the link, their device will be infected with malicious software. This allows the hacker to conduct further criminal activities, such as fraud or snooping.
Criminals who have obtained specific order details, like delivery dates and tracking numbers, could use this information in conjunction with customer addresses to outright steal the shipped goods, intercepting the products before they reach the customer.
Corporate espionage is another possibly damaging outcome for Raven Hengelsport. Rival businesses of Raven could get hold of customer purchase details, like discounts, ordered products, and payments. Those rival businesses could use the phone numbers, email addresses, or home addresses of Raven customers to launch targeted advertising campaigns, offering similar products and undercutting the price of Raven’s products.
Ultimately, this would take business and customers away from Raven Hengelsport.
Preventing Data Exposure
So, what steps should we take to minimize our risk of exposure, and lessen the damaging impact of a data leak?
Here are a few tips to prevent data exposure:
- Only give your data to companies/individuals you know, or can completely trust.
- Make sure the website you’re on is secure. Secure website domains have a ‘https’ and/or a closed lock symbol at the beginning.
- Do not give out information that can easily be used against you (government ID numbers and personal preferences should be kept to yourself).
- Use letters, numbers, and symbols to create rock-solid passwords.
- Don’t click links in emails (or anywhere online) that you cannot be sure are from a reputable source.
- Make sure your privacy settings on social media sites only show your content and personal information to trusted people.
- Avoid using credit cards or typing out passwords on unsecured Wi-Fi networks.
- Educate yourself on data protection, cybercrime, and the different ways you can avoid phishing attacks and ransomware.
About us
SafetyDetectives.com is the world’s largest antivirus review website.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data. The overarching purpose of our web mapping project is to help make the internet a safer place for all users.
Our previous reports have brought multiple high-profile vulnerabilities and data leaks to light, including some 200+ million users exposed by Chinese social media management company Socialarks, as well as a breach at major cosmetics brand Avon that leaked more than 7 GB of data.
For a full review of SafetyDetectives cybersecurity reporting over the past 3 years, follow SafetyDetectives Cybersecurity Team.