
The SafetyDetectives cybersecurity team has uncovered a store in the Dark Web alleging insider access to Telegram servers.
For the non-negotiable price of 20,000 USD, the merchant claims to have unhindered access to Telegram servers “through their employees”; in other words, thanks to at least one insider contact.
The trade offer was discovered on a darknet marketplace for sellers worldwide. However, as with many traders on the Dark Web, it is difficult to verify claims made by individuals concerning their illegal products and services.
What is Telegram?
Telegram is a popular instant messaging service and app. Founded by Pavel Durov and Nikolai Durov, Telegram places a premium on security by supporting end-to-end encrypted messaging, voice, and video calls.
In recent years, Telegram has shifted from a consumer focus to also cater to business users.
Telegram has over 700 million monthly active users and is one of the ten most downloaded apps in the world.
What does the darknet marketplace offer?
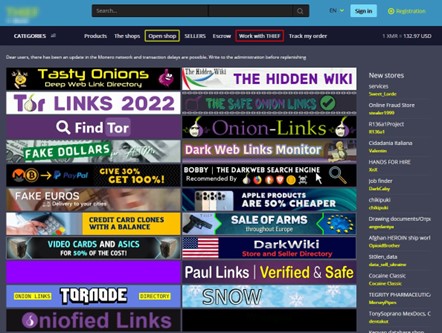
Screen capture of the marketplace’s landing page
The marketplace where we found out about the leak is a darknet marketplace that is not accessible on the clear – or surface – web. It includes illicit software, cracking tools, stolen databases, carding data dumps, drugs, counterfeit money, weapons, and electronics.
The marketplace claims that it can keep payments in escrow if customers select “buyer’s protection”. However, according to activity feeds, there is a mixture of positive and negative reviews related to numerous stores and orders.
Exposed information
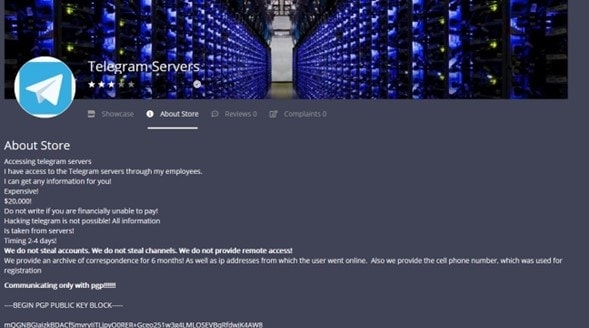
Screen capture of posting alleging access to Telegram servers.
The vendor’s ‘showcase’ advert claims that they can provide access to Telegram servers. Correspondence for approximately six months is on the table, allegedly supplied by insider employees.
The advert reads:
“Accessing telegram servers. I have access to the Telegram servers through my employees. I can get any information for you!
Expensive!
$20,000!
Do not write if you are financially unable to pay!
Hacking telegram is not possible! All information is taken from servers!
Timing 2-4 days!”
The vendor adds that the listing is not related to account or channel theft, and no remote access is provided. Instead, “we provide an archive of correspondence for six months,” alongside IP addresses belonging to active users and registration cell phone numbers.
The impact of the data breach
It is impossible to say how many users, or Telegram servers, may be impacted. However, if the vendor’s claims are valid, an insider in the internal Telegram network would be able to exfiltrate logs and compromise user data. A potential breach of this manner would also undermine the company’s privacy USP (i.e. Telegram’s reputation as a secure messaging app).
Furthermore, the trader insists that no hacking has taken place.
The vendor
It isn’t easy to ascertain the legitimacy of this sales offer. Dark Web marketplaces are rife with scams and fraud, and in this case, the seller’s store, set with a location pin as San Francisco, California, has nothing more than a three-out-of-five star.
At the time of writing, no buyer reviews, issued in relation to the seller, have been published.
Timeline
- N/A: Likely date of the data breach, if genuine
- N/A: Posted online publicly by the vendor
- 16 November 2022: Found by the SafetyDetectives research team
Methodology
SafetyDetectives is constantly looking for new criminal and fraudulent offerings on the Dark Web. We scour new marketplaces for listings indicating recent thefts, vulnerabilities, or active attacks to stay up to date on the latest activities of cyber fraudsters and criminals. .
As ethical researchers, there are limits to determining veracity of claims, as we lack visibility into the contents of raw data published on the dark web. Nevertheless, we remain vigilant in detecting and reporting alleged vulnerabilities on dark web forums.
The presentation of material throughout this article does not imply the expression of any opinion whatsoever on our part concerning the legal ramifications of data incidents highlighted. Statistics and factual data and other information in this article are from sources our researchers believe to be reliable, but we note that errors may occur and information may become out of date.
Preventing data exposure
When third parties hold your data, unfortunately, it is out of your hands when an organization exposes information. However, here are some preventative tips and guidance on what happens after you are made aware of a data breach.
- Be cautious of what information you give out and to whom.
- Check that the website you’re on is secure by looking for HTTPS in the address bar, and/or a closed lock). This shows that communication has at least a basic level of encryption. It would help if you also used a VPN to disguise and secure your online activity.
- Only reveal online what you feel confident cannot be used against you. Avoid sharing or posting sensitive PII, images, or personal preferences that could be troublesome if made public.
- Create secure passwords by combining letters, numbers, and symbols, and consider using a password locker to store complex combinations securely.
- Do not click links or respond to emails unless you know the sender is legitimate. Fraudulent links can send you to malicious websites or expose you to exploit kits, whereas phishing emails are designed to steal your information.
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust.
- Avoid using credit card information and typing out passwords over unsecured WiFi networks.
You can use tools, including HaveIBeenPwned, as well as read our research and keep an eye on the news to find out if you are potentially involved in a data security incident.
If you suspect your data has been leaked, don’t panic. However, it would be best if you tried contacting the organization responsible to discover what happened. Furthermore, it would help if you kept an eye on your credit report and your financial accounts for any suspicious activity indicative of identity theft or fraud.
About us
SafetyDetectives tests, compares, and reviews antivirus software, password managers, parental control apps, and virtual private networks (VPNs) using a robust testing methodology.
The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats. We aim to help the online community defend itself against modern-day cyberattackers while educating organizations on protecting their users’ data.
Find out more about what constitutes cybercrime, the best tips to prevent phishing attacks, and how to avoid ransomware by following SafetyDetectives’ blog and our latest news.