
Hackers claimed to have cracked i2VPN’s admin credentials, accessing its main admin dashboard with information from hundreds of thousands of users.
The cybersecurity team from SafetyDetectives has reportedly uncovered an incident involving i2VPN. Hackers have posted what is alleged to be confidential information from i2VPN, including the admin’s e-mail address and password, on Telegram on Monday, May 29, 2023.
i2VPN is a freemium, no-registration VPN proxy server app available to download on Google Play and the App Store.
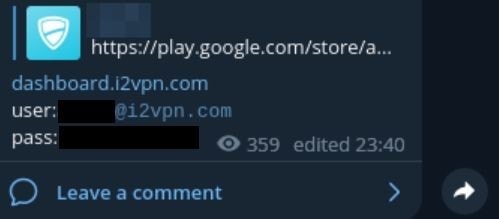
Screenshot of the message exposing the VPN service’s dashboard URL and admin credentials
The hackers shared the VPN service’s dashboard URL, admin’s credentials (e-mail address and password) on an Arabic-speaking hacker channel together with the message “حالا هی برید vpn های ناامن رایگان نصب کنید,” which, based on a web-translation, reads as “Now go install a free, unsecure VPN service.” They also included screenshots of what appears to be the backend of the dashboard, showing data centers and users’ subscription panels and revealing some user information.
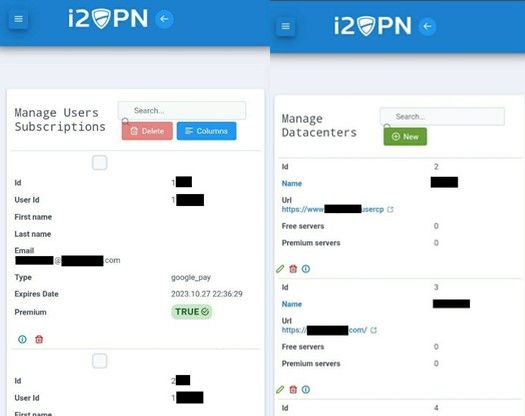
Screenshots of what is alleged to be the VPN admin dashboard interface
While the hackers did not directly leak user data, the breached admin panel credentials supposedly allow access to a significant amount of user data and data centers.
According to statistics from Google Play, as of May 2023, i2VPN has been downloaded over 500,000 times. The app is also available for iOS devices though the exact number of downloads from the App Store is not publicly available.
It’s conceivable — but not definitively known — that each of the estimated 500,000 downloads from the Google Play Store (as well as each iOS download) correlates with an individual user account potentially impacted by this alleged breach. In other words, the purported data leak could potentially affect at least half a million individuals.
The information exposed in the screenshots shared included:
- User IDs
- User account names
- Registered email addresses
- Details relating to premium subscriptions, including subscription payment methods and expiry dates
Hackers could use the information above to spy on users’ activities and commit fraud.
Below is a breakdown of the data exposed in the breach:
Potential Impacts
Hackers can potentially use i2VPN’s exposed admin credentials to access personal information or find a backdoor to monitor users’ browsing activities.
Cyberattackers could also use the exposed account information for phishing attempts, using the registered names and email addresses to impersonate individuals or lure them into divulging sensitive personal information.
What Should You Do if You Think You’re Affected?
If you have an i2VPN account or subscription, consider the following steps to enhance your security, especially if you’ve noticed unusual activity in relation to your account.
- Consider whether you wish to continue using the service in light of these reported concerns.
- Consider reviewing accounts, platforms, and websites you accessed while connected to the VPN service and take measures to safeguard them, such as changing user credentials.
- Consider scanning your device for sensitive files or communication and immediately transfer or remove them to protect against further compromise.
What Are Telegram Leaks and Why Should You Care?
Telegram is a private messaging platform that hackers may commonly use to communicate covertly. It uses encryption and offers anonymity to its users. This means it’s a great platform for hackers who want to post about data breaches and make the information available to many people, even the least tech-savvy.
SafetyDetectives’ cybersecurity researchers scour Telegram and the dark web to find the latest cyberattacks and data breaches. Hackers often post information on these channels before the cybersecurity incident is publicly known.
By reporting on these incidents, we’re able to inform potentially affected parties earlier so that they can act quickly to protect their data.
The details presented in this article represent potential risks rather than confirmed breaches. The extent and duration of the claimed exposure and who might have accessed the data remain uncertain. Our intention in sharing this is not to alarm but to educate our readers about potential online vulnerabilities.
For those who may be using similar services, it’s crucial to stay alert and mindful of any unusual activity. We encourage a proactive approach to online safety, ensuring the safeguarding of personal information wherever possible. Always remember: your digital well-being is in your hands.