
SafetyDetectives had the chance to talk to Patrick W Cieni, Head of Software at xCRUD. We looked at their approach to data protection, and the current state of security for their clientele and the apps industry in general.
What is xCRUD and how does it work?
xCRUD is a web application framework that simplifies the process of creating and managing database-driven applications. The “x” in xCRUD stands for “extended,” and it’s designed to extend the capabilities of CRUD (Create, Read, Update, Delete) operations commonly used in web development. xCRUD is a PHP-based framework, and it provides a set of tools and features to streamline the development of web applications with a user interface for database operations.
Overall, xCRUD is designed to save developers time and effort by automating the creation of common web application components for managing database data, thus speeding up the development process and reducing the need for writing extensive code from scratch. It’s especially useful for developers who need to create data-driven applications quickly and efficiently.
Companies across the world have used xCRUD to develop their business solutions. Our estimate, based on our client support, is that we have $1.5million worth of projects running on xCRUD. In fact, we have done custom xCRUD projects worth $230k for our clients using xCRUD.
What steps have you taken to ensure the security of your platform?
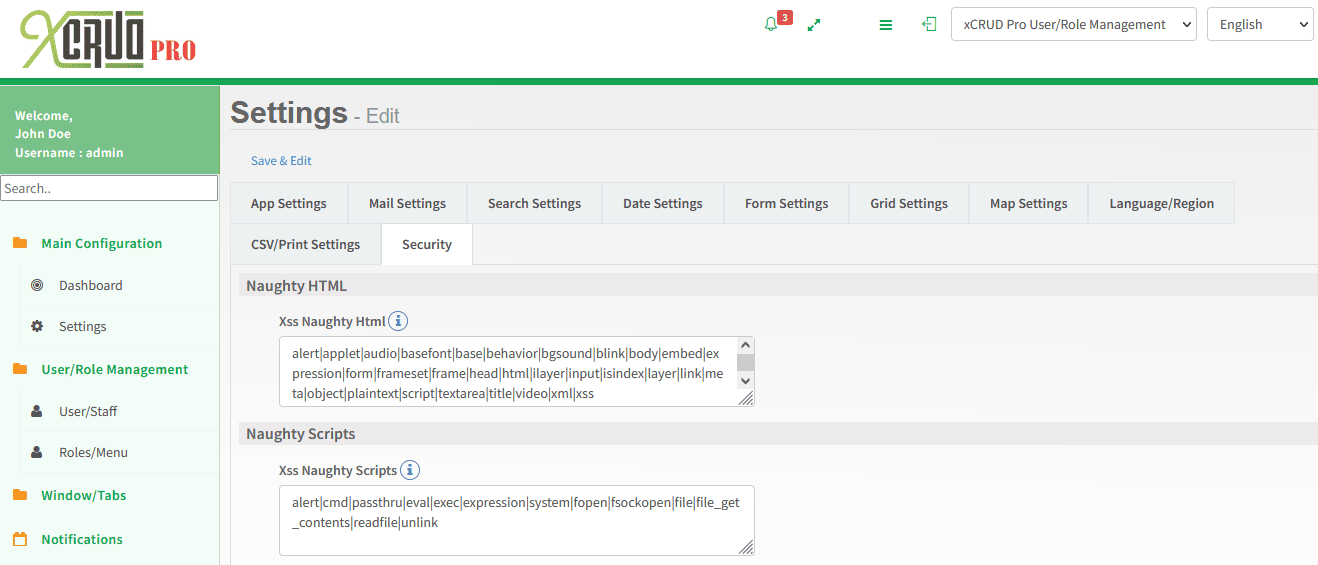
“XCRUD Pro offers comprehensive user and role management capabilities. You have the ability to create and manage users, establish custom roles, specify access privileges for different windows and menus based on those roles, and seamlessly assign users to their respective roles.”
xCRUD Pro has an authentication module that implements password hashing and verification using the bcrypt algorithm, a widely recognized and secure method for securely storing and verifying passwords.
We also provide a session expiration time of a configurable 30 minutes, which is a common security practice to limit the risk of session hijacking.
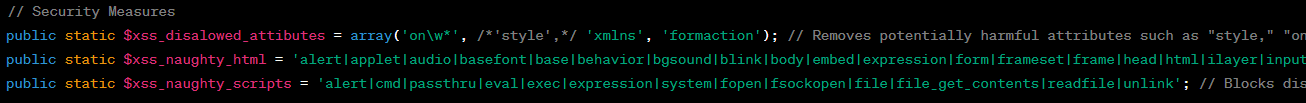
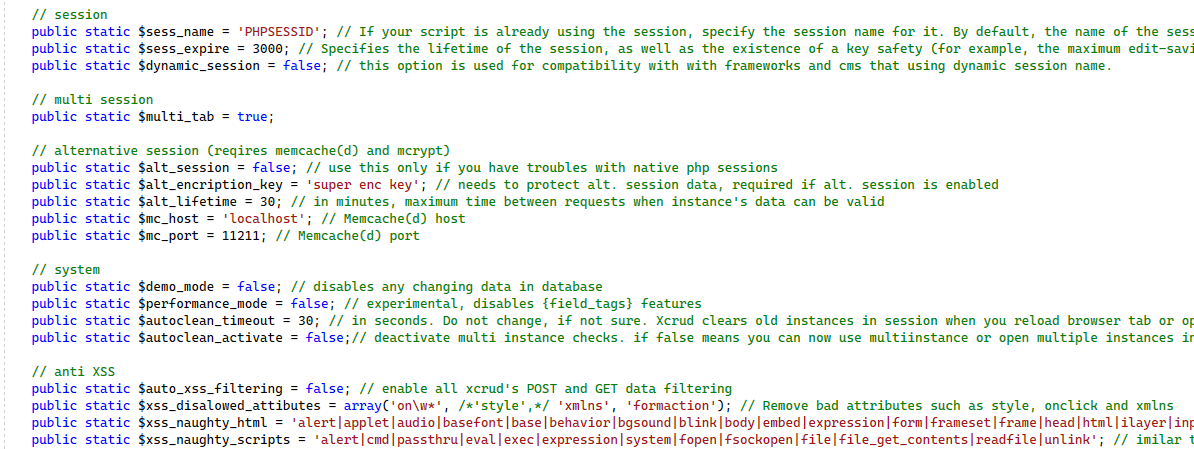
We also implemented a security mechanism to sanitize user input and prevent XSS attacks – It restricts the use of certain attributes, HTML tags, and potentially harmful scripts to minimize the risk of malicious code execution within the application.
Note: security is a complex and evolving field, and relying solely on such measures may not provide complete protection. It’s crucial to keep the code and security practices up to date and consider other security measures like input validation, output encoding, and parameterized queries to ensure a robust defense against web-based attacks.
We are striving to meet the ISO 27001 by June, 2024. Achieving compliance with ISO 27001 and SOC 2 is an ongoing process, and it requires dedication and resources to maintain a strong security and privacy posture. We collaborate with cyber security experts, who assist us in achieving the ISO 27001 certification and to improve our security features.
Performing regular security audits, especially on our clients running our xCRUD solutions like CRM, is the best way for us to identify and address potential weaknesses in our xCRUD infrastructure in a timely manner.
To give a real-life example of how we handle security, a major Motor Valuation platform recently went under the looming threat of a potential data breach. Leveraging xCRUD’s robust cybersecurity framework, our platform swiftly detected and thwarted a series of sophisticated hacking attempts. With its vigilant monitoring, user access controls, and state-of-the-art encryption protocols, xCRUD ensured that customer data remained impervious to the threat. This resounding success story is just one example of how xCRUD has consistently and effectively protected sensitive data against cyber threats, demonstrating its unwavering commitment to cybersecurity excellence.
Do you support your customers in preventing and mitigating cyber threats? How?
Our commitment to enhancing security for xCRUD users is evident through our documentation, which already offers valuable insights into minimal security configurations. In our ongoing efforts to further empower our clients, we are excited to announce the upcoming availability of comprehensive security training.
Additionally, users can reach out through our chat platform and email, where our team of security experts promptly provide assistance.
A recent example underscores our commitment: when a client encountered issues due to an adjustment in the ‘sess_expire’ setting that inadvertently compromised their data security, we responded swiftly, fortifying their instance for improved security.
What are the most common vulnerabilities your customers are facing, and how do they deal with them?
Meet Joyce, the Chief Technology Officer of a growing e-commerce company, “ITech Solutions.” ITech Solutions relies heavily on web applications and databases to deliver a seamless shopping experience to their customers. With an increasing amount of sensitive customer data to manage, security was a top priority for Joyce and her team.
Challenges:
ITech Solutions had encountered several security challenges common to online businesses, including SQL injection attempts, Cross-Site Scripting (XSS) attacks, and concerns about data authorization. They needed a solution that could provide a robust defense against these vulnerabilities while allowing them to focus on their core business goals.
Discovering xCRUD:
In their quest for a secure and efficient solution, Joyce’s team stumbled upon xCRUD plugin, a powerful tool for creating, managing, and securing web applications and databases. They were able to integrate it with their wordpress/ecommerce site. Intrigued by its capabilities, Joyce decided to give it a try.
Addressing Common Vulnerabilities:
xCRUD proved to be the answer to ITech Solutions’ security woes. Here’s how xCRUD helped them deal with the common vulnerabilities they were facing:
- SQL Injection: xCRUD’s built-in parameterized queries and input validation ensured that user input was sanitized, making SQL injection attempts futile. Sarah’s team no longer had to worry about attackers manipulating their SQL queries.
- Cross-Site Scripting (XSS): xCRUD implemented rigorous output escaping and content validation, ensuring that user-generated content was displayed securely without the risk of XSS attacks. This helped TechWonders protect their users from potentially malicious scripts.
- Cross-Site Request Forgery (CSRF): xCRUD enabled the implementation of anti-CSRF tokens in their forms and requests, making it nearly impossible for attackers to forge requests. This safeguarded TechWonders’ applications against CSRF attacks.
A Secure Future:
With xCRUD as their trusted security partner, ITech Solutions now had peace of mind, knowing that their sensitive customer data was well-protected. Their focus had shifted from security concerns to business growth and innovation, as they continued to provide exceptional service to their customers.
ITech Solutions’ story is a testament to the power of xCRUD in securing sensitive data and enhancing the overall security posture of businesses. They had successfully turned their security challenges into a success story with the help of xCRUD.
Security features Alone are NOT enough!
Plugins such as xCRUD offer a wide range of security capabilities, but we still see common misconfigurations caused by users, which can still result in new vulnerabilities.
Ensure that xCRUD has been correctly configured and that the server hosting your xCRUD application is well secured (I.e. Install SSL certificate on the server).
And please, avoid changing default security settings as recommended by xCRUD installation!
How do you stay updated on the latest cybersecurity threats and trends?
I find Reddit’s cybersecurity discussions particularly insightful as they provide firsthand accounts of cybersecurity-related challenges.
From those discussions we noticed that a prevailing issue in the realm of cybersecurity is that many digital firms lack awareness of the looming threats and often fail to prioritize cybersecurity on their corporate agendas. Addressing this concern requires a concerted effort to raise awareness about cybersecurity compliance across a spectrum of companies.
What security challenges do you see in the future of your industry, and how do you plan to cope?
As systems become increasingly intelligent, the misuse of AI technology, such as deepfakes and AI-generated phishing attacks, emerges as a substantial threat. This threat stems from the fact that hackers and malicious actors can leverage AI to craft convincing fraudulent content and automate their attacks.