
Updated on: October 23, 2024
If you’ve ever received a text message saying there was some kind of problem (like with your “recent delivery” or your PayPal account or your Amazon account) with instructions for you to click on a link to resolve the issue, you have likely been the target of smishing — SMS-based phishing (“SMiShing”).
Here’s how smishing works: A hacker sends you an SMS (i.e. text message) asking you to click on a link. If you click on the link in the message, you’ll be redirected to a fake website asking you to provide your information onto a phishing form — a fake webform that’s controlled by the hackers but looks identical to a webform you’re familiar with (like a PayPal login page or an Amazon login page) — or the website will try to download malicious software onto your device that will be able to track everything you do.
The hacker is trying to get your sensitive information via a text message (i.e. SMS). They will urge you to provide personal information — a social security number, a credit card number, or health insurance information — claiming that you must give your information or something bad will happen (like your electricity will be shut off, your credit card will be blocked, or your online account will be terminated).
Smishing is one of the easiest ways for hackers to steal user data because the user is literally handing the hacker all of their information. And since people are increasingly glued to their phones, it’s no surprise that the number of smishing attacks has skyrocketed in recent years. But even though people are getting hacked by malicious mobile messages every day, telecommunications companies are working fast on attacking SMS-based scams.
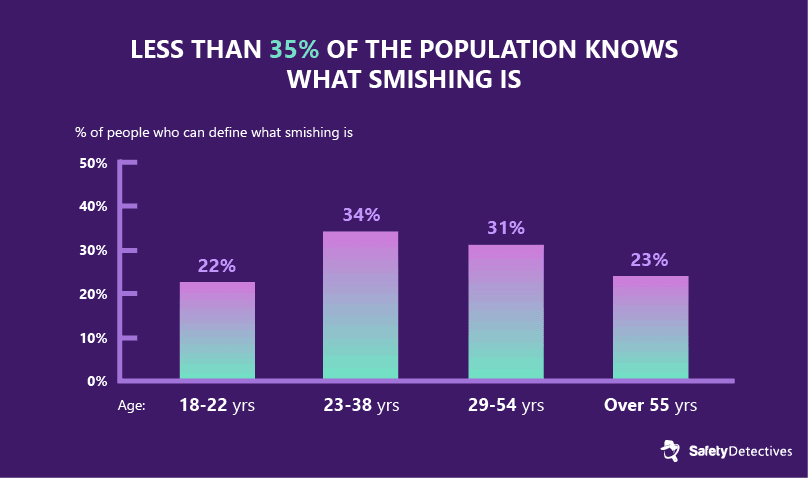
#1. Less than 35% of the population knows what smishing is.
For mobile users, especially older users, it can be very difficult to assess the authenticity of a text message. This is one of the reasons why SMS-based fraud has such a high rate of success.
Proofpoint, a security software company that processes more than 80% of North America’s mobile messages, reported that only 23% of users over 55 had been able to correctly define smishing — but millennials didn’t do much better, with only 34% of people 23-38 years old demonstrating awareness of the term.
#2. Smishing is causing millions of dollars in losses.
Because most smishing texts contain links to phishing websites, it can be hard to find separate statistics for smishing and phishing attacks.
The IC3 (Internet Crime Complaint Center), the FBI’s cybercrime complaint division, has documented over 2,800 complaints of phishing and spoofing (a cybercrime tactic where a person or program masquerades as another), costing over $3 million in losses.
But it’s not just a problem in the USA. The European Payments Council reported that more than 166,000 phishing victims had made complaints between June 2016 and July 2019, with $26 billion in losses.

#3. An average of $8,199 per person was lost in 2024 due to tax-related phishing and smishing scams.
According to McAfee’s 2024 Tax Scam Study, 1 in 4 Americans has become a victim of a tax scam, with the average loss amounting to $8,199. In fact, this type of fraud has become so common that the IRS started its 2024 Dirty Dozen list, an annual compilation of the most prevalent tax-related scams, with a crucial alert about the rise of phishing and smishing scams.

#4. Smishing attacks can steal user information using fake two-factor authentication (2FA) messages.
If you’ve ever received a one-time password to verify your identity on PayPal or Amazon, then you’ve used SMS-based 2FA — however, this very same technology can be used to steal your login information, redirect you to fake login pages, or even use hacking techniques to send one-time passwords intended for your phone to completely different devices.
That’s one big reason why the National Institute for Standards and Technology (NIST) recommends against using SMS-based 2FA passwords — if you don’t rely on it, you won’t fall victim to it.

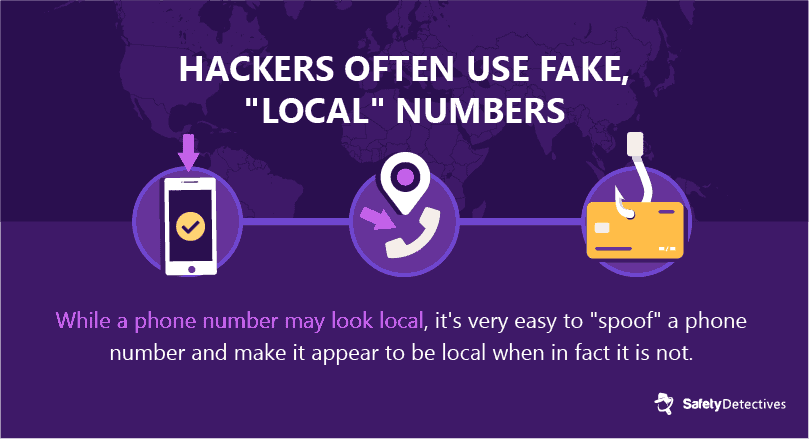
#5. Fake numbers used by hackers are often local numbers.
Hackers can pretend to be texting you from your same area code, giving them a layer of authenticity that deceives many people. By tracking your metadata, hackers can gain access to your area code and “spoof” a local number — this allows hackers from different countries to appear to be texting you from your town or city.
Hackers can even spoof numbers of people you know, tricking you into handing over personally identifiable information.
Spoofing, the act of hiding your true number behind a geo-targeted phone number, has long been illegal for domestic callers in the US. But in 2019, the FCC made it illegal for text messages and international calls to be spoofed as well. But this doesn’t mean much for hackers — they still run robo-text operations with spoofed numbers (as long as they don’t get caught).
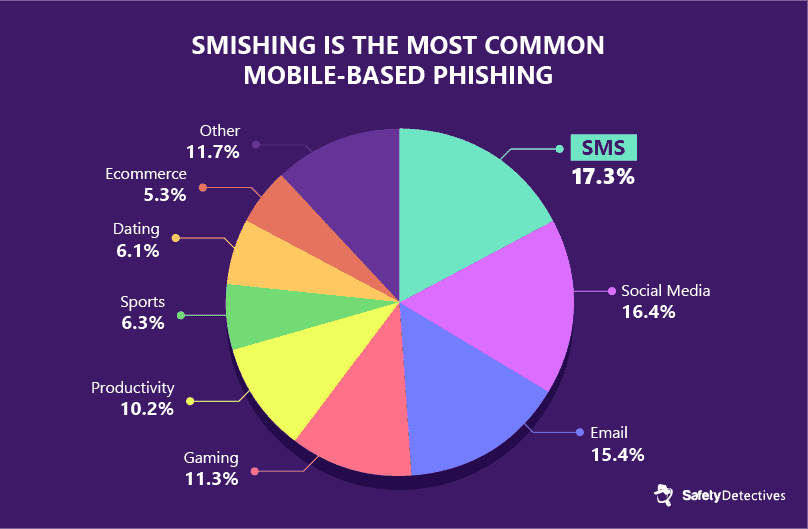
#6. SMS-based phishing is the most common type of mobile-based phishing.
According to a 2018 report by the cloud-infrastructure provider Wandera, 17% of its enterprise users encountered phishing links on their mobile devices. Compare this to only 15% of users who received a phishing email and 16% who received phishing links via social media apps.
In 2020, the Bank of Ireland was forced to pay out €800,000 to over 300 bank customers who gave their information away in a single smishing scam.
#7. In 2022, 27.6% of mobile users tapped on 6 or more smishing links.
A report published by Lookout in 2022 shows that smishing scams are becoming ever more sophisticated — as a consequence, more and more people are falling prey to this type of mobile fraud.

#8. Fake delivery notifications are a common smishing attack.
With the huge spike in business for delivery services like Amazon and DoorDash, we’ve seen a similar spike in fake delivery notifications.
These can be as vague as a message that says, “your package is being held at the post office, click here to claim”, or it can be more specific ‘spear-smishing’, which can claim to be from a retailer you recently purchased from and include your name and address.
Regardless, it’s really important that you avoid clicking or following links to delivery notifications. If you want to track a package, you can go to the official website of the retailer or delivery service in question, but never trust links sent via SMS from unknown numbers.

#9. Even “secure” messaging apps like WhatsApp and Signal can be used to spread malware and phishing links.
Researchers from Lookout and the Electronic Frontier Foundation discovered that an international hacking agency (nicknamed “Dark Caracal”) had been sending phishing links via WhatsApp, Signal, Messenger, and SMS which redirected users to download fake “updates” to their encrypted messaging apps.
These updates were actually malware files with the ability to access user’s screens, keystrokes, and even provide remote access to the hackers who were then able to send smishing links from compromised phones in order to spread the malware infection.
Many of the targets of Dark Caracal’s surveillance malware were citizens involved in defense, government, activism, law, and journalism — but even if you’re unlikely to be a victim of international espionage, it’s important to know that your secure messaging app may not be so secure after all.

#10. You can report spam and smishing texts.
Every major mobile carrier in the US has banded together to create a fraud text reporting service. This service is pretty easy to use — just forward any suspicious messages to the number 7726 (SPAM). You’ll get a text back from your mobile provider asking you to provide the phone number that issued the smish or spam text. This helps to build up a shared database between mobile providers, which can be used to block and even prosecute smishers and hackers.
iOS users using the “Messages” app can report it to Apple and Android users can report it to Google.

Bonus Fact: Telecom companies know this is a problem and are working on fixing it.
In addition to the aforementioned SPAM (7726) text hotline supported by most mobile carriers and laws passed by the FTC and FCC to block spoofing for mobile communications, the Cellular Telecommunications Industry Association (CTIA) has adjusted their best practices by using machine learning and shared databases between telecom providers to block as many suspicious numbers as possible.

How to Protect Yourself from Smishing Attacks
While governments and telecommunications companies scramble to keep up with the millions of scam text messages that are sent out on a daily basis, mobile users have a ton of options for protecting information from hackers and scammers.
-
Don’t follow links from suspicious text messages without verifying the source.
There are plenty of legitimate text notifications informing you about things like deliveries, health information, and even suspicious account activity.
If you receive a message that urges you to take action quickly via SMS, find out whether the message is genuine or not. For example, if your bank texts you a link and tells you to log into your account immediately, call your bank and ask if they sent you a message.
These are some of the most common scam texts going around in 2024:
- Debt scam. The FTC has made it clear that it is against the law for loan collectors to send you a message to collect money without identifying who they are. You should never perform any payment via SMS.
- Refund scam. If you get a text message saying you’ve been given a refund due to an overpayment for a specific service, and it asks for your personal details to finalize the reimbursement, it’s probably a scam.
- Reactivation scam. Scammers may tell you that your account has been compromised via another device and ask you to text back to XXXXX to reactivate your account. Don’t reply to the message. Instead, check your account to confirm that it’s active. If it is, then it’s a scam. If your account is not active, call your service provider and ask why.
- Family emergency scam. Smishing texts often rely on scare tactics to convince users to act without thinking. If you get a text from a hospital, jail, or a stranger bearing bad news about your family, then stay calm and don’t panic. Ask the sender specific questions to verify their identity, and don’t share any of your information until you’ve separately verified that the family member in question is experiencing an emergency. US users can call 1-877-FTC-HELP (1-877-382-4357) for advice.
In general, do not click on any link sent via text message if it asks for your personal information, like bank details or a social security number.
If the message contains a link and an urgent call-to-action, it’s probably a smishing message. If the message comes from an unknown number, don’t respond.
You can notify your mobile provider about spam and smishing texts by forwarding suspicious messages to 7726 (SPAM), which will notify every major telecommunications company that this number needs to be investigated and possibly blocked from their network.
-
Install an antivirus app on your phone.
Consider installing mobile security software that includes SMS filtering, anti-theft, antivirus protection, and web protection.
It doesn’t matter if you’re on Android or iPhone, you can still be susceptible to phishing and smishing attacks. Check out our lists of the best antivirus for Android and iOS if you need help selecting the best app for your needs.
Features to look for in mobile-friendly antivirus software:
- SMS and call monitoring.
- Anti-phishing protection.
- Anti-theft tools.
- App scanning.
- Wi-Fi network monitoring.
Most smishing attacks depend on users giving their information away to phishing sites or installing malware apps on their phone — so a good antivirus app will be able to provide multi-layered protection.
Maintaining Cybersecurity Is a 24/7 Practice
I hope this list has given some clarity about the nature of smishing attacks and that it provided some helpful information to help keep you and your loved ones safe from this growing threat.
A good antivirus app will protect you from malicious texts and links, but there’s no substitute for a cautious mind. As mobile users, we have the power to protect ourselves and educate our friends and family about the tricks being used by scammers to take advantage of people.
Feel free to use any of the graphics and data in this article, with attribution to SafetyDetectives.