
You think you have the right mindset when it comes to cybersecurity? Read this interview and then think again.
If you run an online business, you are probably making one of these critical mistakes:
- Thinking that small risks are “small”
- Looking at cybersecurity issues from the wrong angle
- Being complacent and reactive
Safety Detectives asked Oleksandr Filipov, CEO of Datami and partner of SSD Technology, to discuss the real dangers and best solutions to fix these gaps in cybersecurity awareness, and also shared his tips to increase your online privacy from his experience providing over 400 Successful Penetration Tests and specialized cybersecurity services rated 5-stars on Clutch.
What are the most overlooked and underestimated cyber threats in your industry?
People often overlook small security risks, thinking they’re not a big deal. However, when these tiny issues add up, they can become a big problem. After testing, we find various vulnerabilities, but clients usually only fix what they think is a serious problem. Attackers know this and target these small issues.
Imagine a tiny mistake, like a message saying an email isn’t linked to any account. This small thing can actually let attackers get into the entire user account. It’s a big deal because if we ignore these small risks, it can lead to major problems, like losing data and money.
If we don’t take care of these small issues, the consequences are huge. User accounts can get hacked, leading to bigger problems like losing important information and making customers lose trust in business.
Here is a better, simple and proactive security plan…
Focus on all the risks, big and small, instead of just fixing the big problems. We use continuous monitoring and regular checks to catch these small issues before they become big problems. This way, we can keep systems safe and our customers’ information secure.
Catch small cybersecurity issues before they become big
What further steps do you usually suggest your customers to enhance their online security?
Implementing SSL (HTTPS) is crucial for encrypting data during online transactions, safeguarding personal and payment information. Without this, there’s a heightened risk of data interception and compromise, emphasizing the need to ensure the entire website uses HTTPS.
Enabling Two-Factor Authentication (2FA) adds an extra layer of security by requiring users to provide two forms of identification. This reduces the risk of unauthorized access, enhancing the overall protection of customer accounts.
Regularly applying security updates to the e-commerce platform and associated software is essential for maintaining a secure online environment. Failing to do so increases susceptibility to the latest threats and exploits, making prompt updates crucial for robust security.
Utilizing a Web Application Firewall (WAF) acts as a shield against potential threats, filtering and blocking malicious requests. This protection is particularly relevant, preventing attacks such as SQL injections and cross-site scripting, significantly reducing the risk of compromising the e-commerce site.
Implementing regular backups of the website’s data is crucial for ensuring continuity and minimizing the impact of a security incident. Without this measure, there is a risk of data loss and prolonged downtime, underscoring the importance of regularly backing up data and storing it securely offsite.
Can you share any experiences your company has had with cybersecurity incidents and the lessons learned?
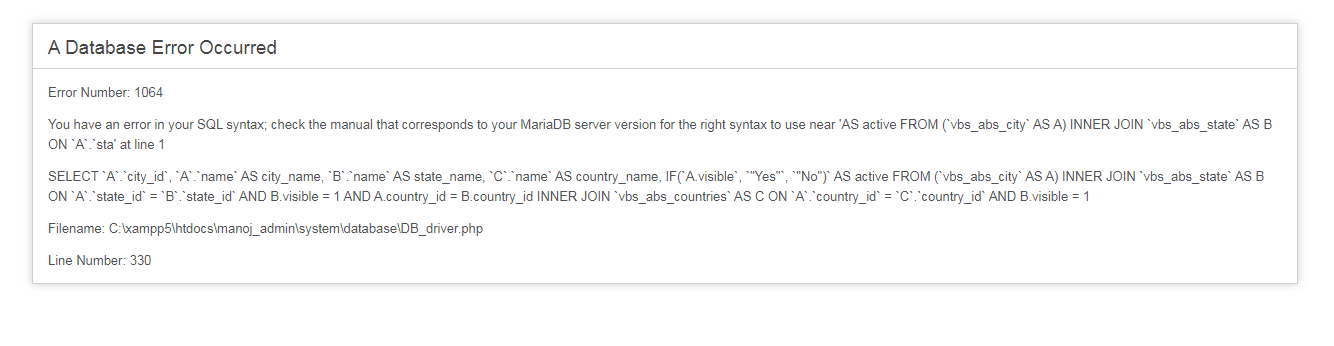
During a routine penetration test, we encountered a significant cybersecurity incident on a client’s website related to a SQL injection vulnerability. This vulnerability allowed potential attackers to access the entire database, posing a severe threat to the confidentiality of sensitive information.
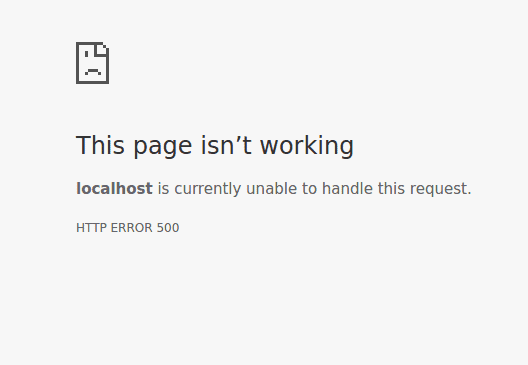
Our initial recommendation was to address the root cause by modifying the source code to eliminate the vulnerability. However, the client opted for a quick fix by replacing the error message associated with the SQL error, displaying a generic 500 error instead.
Upon conducting a follow-up penetration test, we discovered that the initial fix was inadequate, and the vulnerability persisted, leading us to identify a blind SQL injection attack vector. This type of attack exploits the application’s response to true or false questions, providing an alternative means to access the database. Despite the client’s attempt to conceal the issue through error message manipulation, the underlying problem remained unresolved.
This experience underscored the importance of addressing cybersecurity issues at their roots, emphasizing the need for thorough remediation rather than superficial fixes. The incident also reinforced the significance of ongoing vigilance and proactive security measures to prevent similar occurrences in the future.
Do you think the level of cybersecurity awareness is improving in your industry?
In recent years, as our industry has increasingly transitioned assets and operations online, there has been a noticeable improvement in cybersecurity awareness. Positive trends include a growing acknowledgment of the critical role cybersecurity plays in safeguarding financial transactions, sensitive data, and ensuring compliance with regulations. The realization that cyber threats, including large-scale data breaches and the evolving landscape of cyber warfare, pose substantial risks has led to a heightened focus on establishing robust security postures.
However, despite these positive strides, there is still a need for improvement in certain areas.
What is secure today may become vulnerable tomorrow
A persistent misconception we often encounter is the belief that once a business undergoes a cybersecurity evaluation and addresses identified vulnerabilities, it achieves a state of absolute security. Where threats evolve rapidly, and what is secure today may become vulnerable tomorrow. It is crucial to convey that there is no such thing as a system being ultimately 100% secure. Continual monitoring, regular personnel training, and the implementation of updated security measures are essential components of building and maintaining a reliable security framework.
Believing that a one-time security evaluation ensures perpetual safety can lead to complacency and a lack of vigilance, creating an environment susceptible to emerging threats.
To debunk these misconceptions and promote better cybersecurity awareness, there is a need for ongoing education and communication within the industry. Emphasizing the importance of continuous monitoring, adapting to evolving threats, and adopting a proactive stance towards cybersecurity are steps that can enhance awareness and build a more resilient security culture. Regular training programs, dissemination of updated security protocols, and transparent communication about the ever-changing nature of cybersecurity contribute to a more informed and vigilant industry.
What cybersecurity challenges do you see coming in the near future, and how do you plan to cope?
Looking ahead, one big challenge in cybersecurity is the growing use of smart technology that can learn and adapt – Artificial intelligence (AI).
Bad actors are using AI to make their attacks more clever, making it harder for regular security measures to catch them. We’re planning to use AI too, but in a good way, to help us spot and stop these tricky attacks.
The tricky part is finding the right balance. We want to use AI to protect against cyber threats, but we also need to be careful because bad actors can use it too. Our plan is not just to rely on AI but also to train our team continuously and work with experts. We want to be ready for new challenges and stay updated on the latest trends.
We’re learning from conferences, online forums, and trusted publications to make sure we’re using the best strategies to keep our systems safe. It’s like staying one step ahead in a game – we’re making sure we know the moves before the bad players do.