
The internet breaks down the barriers of global connectivity, allowing people everywhere to connect instantly. But with this tremendous benefit comes a downside: the dark reality of cyberstalking.
Cyberstalking is the use of the internet and other technologies to harass or stalk someone, which for the victim can lead to severe psychological distress and even tangible harm. While some jurisdictions, including the US, have criminalized cyberstalking, many others have not, creating a problematic gap in international legal frameworks.
This article will guide you through the intricacies of cyberstalking, highlighting its dangers and offering practical strategies to protect yourself in the digital world. Understanding how to protect yourself from cyberstalkers is not just a matter of privacy — it could be essential to your personal safety and mental well-being.
Understanding Cyberstalking
Cyberstalking is a modern form of harassment in which perpetrators use technology to harass, threaten, intimidate, or even defraud victims. These victims often know their harassers, who may be ex-partners, acquaintances, or even family members.
Cyberstalking laws vary, leaving victims unsure of how to keep themselves safe. Some jurisdictions require credible threats of violence before anything can be done to stop the harassment, while others include threats to the victim’s family or define cyberstalking itself as an implied threat.
While the lack of physical presence in cyberstalking doesn’t diminish its seriousness, it can make the harassment more challenging to deal with, depending on the laws where you live.
What Are the Motives behind Cyberstalking?
The motivations for people who engage in cyberstalking are complex and may be partly related to mental health disorders such as personality disorders, depression, schizophrenia, and other psychotic disorders. When used as an attempt to rekindle a relationship, retaliate against perceived harm, or control another person, it may be one aspect of a larger pattern of abusive behaviors meant to control another person.
The online world offers instant gratification to perpetrators, allowing them to pursue their targets from a distance, without the geographical limitations of physical stalking. This creates a sense of detachment and anonymity, making it an attractive way to carry out such harassment.
A type of cyberstalking—called partner surveillance—also occurs within relationships. Have you ever heard of a friend or acquaintance who monitors their partner’s digital activities? The goal is to track their movements, gather information, or maintain the upper hand in the relationship. The motives in these cases vary, but they are often rooted in a sense of insecurity or possessiveness
In cyberstalking, the perpetrator may contact or harass the victim directly, or in other cases, the stalker may spread misinformation or malicious content about the victim online. Whether the method is direct or indirect, cyberstalking is an invasion of privacy and can have serious emotional and psychological effects on the victim.
Where Is Cyberstalking Illegal?
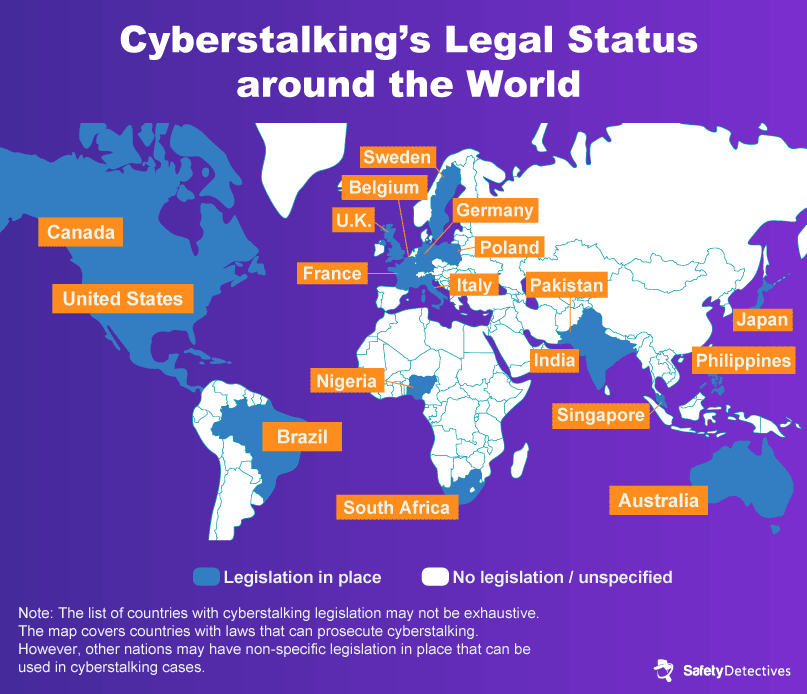
Cyberstalking laws vary widely across the globe. In the United States, Australia, and Poland, cyberstalking is recognized as a criminal offense. However, cyberstalking is not explicitly illegal in much of Europe, Russia, or China.
Some real-life examples of cyberstalking include:
Example #1: A former eBay executive admitted to committing several felonies in an attempt to intimidate a Massachusetts couple. The motive was to pressure the couple to stop publishing a newsletter that focused on eBay sales. The individual sent public tweets and threatening messages directly to the publishing company via Twitter. In addition, the executive escalated the situation by visiting the couple’s home and secretly placing a GPS tracker on their vehicle.
Example #2: A Texas man cyberstalked a woman who wouldn’t date him. He used over 100 different social media accounts to send threatening messages to her and anyone he thought she was dating. After more than half a year, the situation escalated to the sending of death threats through these accounts. He also posted her name, address, and other sensitive information online.
These cases highlight the importance of having legal measures in place to protect individuals from this threat. This disparity in legal recognition underscores the importance of knowing your local laws and seeking appropriate help if you are a victim of cyberstalking.
Methods Cyberstalkers Use
Cyberstalking can take many forms, and each method has its own insidious way of violating your privacy and security. This section explores the many tactics used by cyberstalkers, shedding light on their methods to better equip you with the knowledge to protect yourself.
Forms of Surveillance
The surveillance techniques used by cyberstalkers can be incredibly sophisticated, taking advantage of the very tools and platforms designed to connect us. Forms of surveillance include:
- Social Media Monitoring: The perpetrator closely monitors the victim’s activities on social networking platforms including posts, comments, likes, and friends lists. They may also use features such as Street View or geo-tags. At the most extreme, they may gain access to their victims’ accounts and even impersonate them online.
- Cyber and Electronic Surveillance: Electronic surveillance is the capture and analysis of any form of electronic signal, including telephones, satellite communications, radio frequencies, and the Internet. Cyber surveillance refers to the monitoring of the Internet and digital networks. Both forms of surveillance can take advantage of “smart” or “connected” devices that are becoming increasingly prevalent in our lives.
- Stalkerware and Spyware: Spyware is malware designed to covertly observe and track actions on a victim’s device. This can include browsing habits, keystrokes, personal communications, and financial information. Stalkerware, a subset of spyware, is tailored for personal surveillance and enables access to private messages, location data, call logs, and even live audio or video feeds from a device.
- GPS Monitoring: GPS-enabled devices, such as smartphones and wearable technology, has facilitated a form of surveillance where a person’s location can be tracked without consent. A common method exploits the metadata in digital pictures, which includes geotagged information pinpointing the time and location where the photo was taken.
Forms of Abuse
Stalking is often part of a pattern of criminal behavior, and can include activities such as doxing, identity theft, and various forms of harassment. These abusive behaviors serve as tools to exert control, instill fear, and cause harm to the victim.
- Email Spamming: Spamming involves sending bulk messages to the victim’s email address. The sheer volume can jam the inbox, making it difficult for the victim to find legitimate communications. This tactic serves a dual purpose: it floods the victim with irrelevant information and distracts them from the stalker’s true intentions.
- Email Bombing: An email bomb is a type of denial-of-service (DoS) attack aimed at an email server. The stalker sends a mass of emails to the victim’s inbox in a short period. The goal is to overwhelm both the inbox and the corresponding email server, rendering them non-functional. This disrupts the victim’s communication and can lead to the loss of important emails and data.
- Defamation: In the context of cyberstalking, defamation is a tactic in which the perpetrator uses social media and other websites to spread false information about the victim to defame their character. This is intended to damage the victim’s reputation, community standing, and personal relationships to isolate them from their social circles, weaken their support systems, and cause psychological distress.
- Doxing: The perpetrator publishes the victim’s personal information without consent. This can include details like home addresses, phone numbers, email addresses, workplace information, and other sensitive data. The objective of doxing is to breach the victim’s privacy and expose them to further harassment, intimidation, and even physical danger.
- Impersonation: In the context of cyberstalking, impersonation is when the stalker assumes the identity of the victim or another person to deceive, harm, or exploit. This can be particularly damaging as it both infringes on the victim’s privacy and can lead to misrepresentation and further harassment. Types include social media, email, and online impersonation, as well as phishing, spoofing, and catfishing.
- Revenge Porn: This typically occurs when intimate images or videos shared privately between individuals are distributed without consent. Often, perpetrators use these materials as a form of revenge or coercion after a relationship ends. The impact on the victim can be devastating, leading to emotional distress, reputational damage, and social isolation.
- Sextortion: This form of abuse involves threats to release intimate images or information unless the victim complies with certain demands, which can include more images, sexual favors, or even money. The threat of public exposure is used as leverage to exploit and control the victim.
- Financial Abuse: This is a manipulative tactic employed by abusers to gain power and control within a relationship. By controlling the victim’s finances, the abuser effectively restricts their independence and freedom. Methods might include restricting access to funds, sabotaging employment, exploiting financial resources, and hiding or misusing assets.
- Threats: These are commonly used to intimidate and control cyberstalking victims. They can range from indirect threats such as subtle insinuations of harm to explicit threats of harm and even death. Stalkers might create doctored videos that depict harm toward the victim. Threats are a powerful tool for a stalker, enabling them to exert psychological pressure and control over the victim without needing physical proximity.
- Blackmail: The stalker typically threatens to reveal or distribute private information or images unless the victim meets specific demands. These demands can vary widely but often include requests for money, sexual favors, or other actions that further victimize the individual. The effectiveness of blackmail as a tactic lies in its ability to instill fear and a sense of powerlessness in the victim.
The History of Cyberstalking
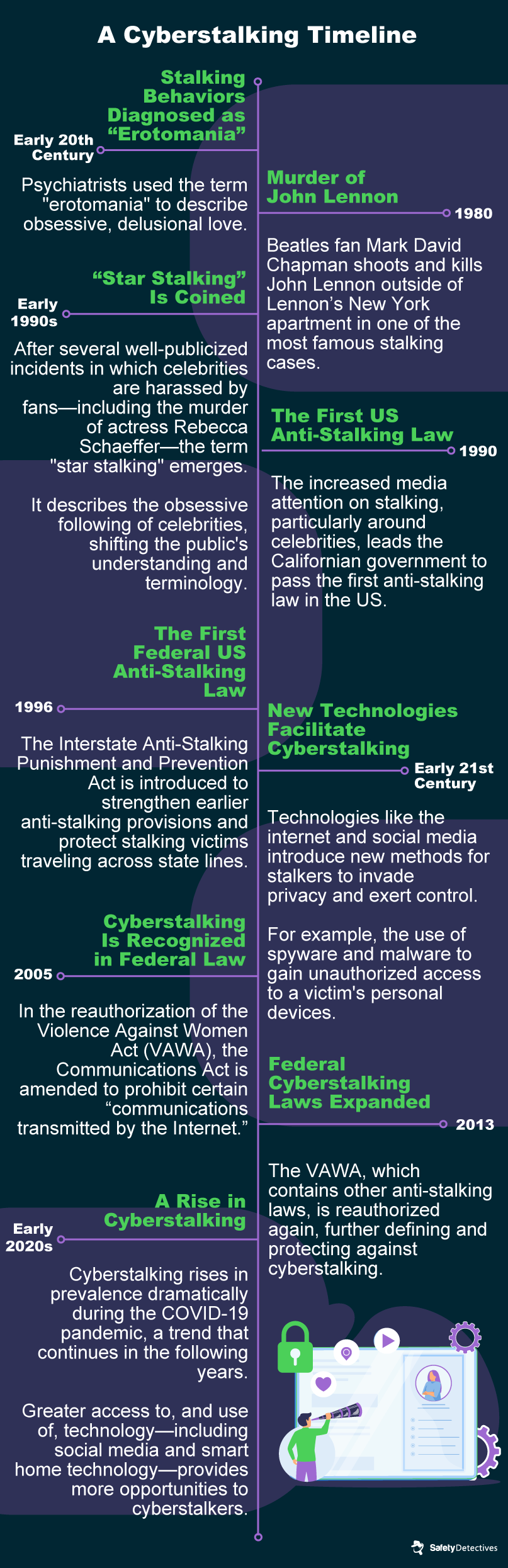
How society understood stalking, once thought to be an obsessive love called “erotomania,” changed in the 1980s and ‘90s. During this time, high-profile celebrities including Madonna and Steven Spielberg were stalked and threatened. In extreme cases, celebrities—including John Lennon, Rebecca Schaeffer, and Monica Seles—were even attacked.
The high-profile nature of these victims helped amplify the need for anti-stalking legislation. Eventually enacted in all 50 states, the first anti-stalking law was passed in California in 1990.
Examples of what we would now call stalking can be found throughout recorded history, including Zeus’s subterfuge in his pursuit of mortal women and Romeo’s behavior in “Romeo and Juliet.” The way these stories are still shared today highlights stalking’s deep roots and lack of critical examination in our society.
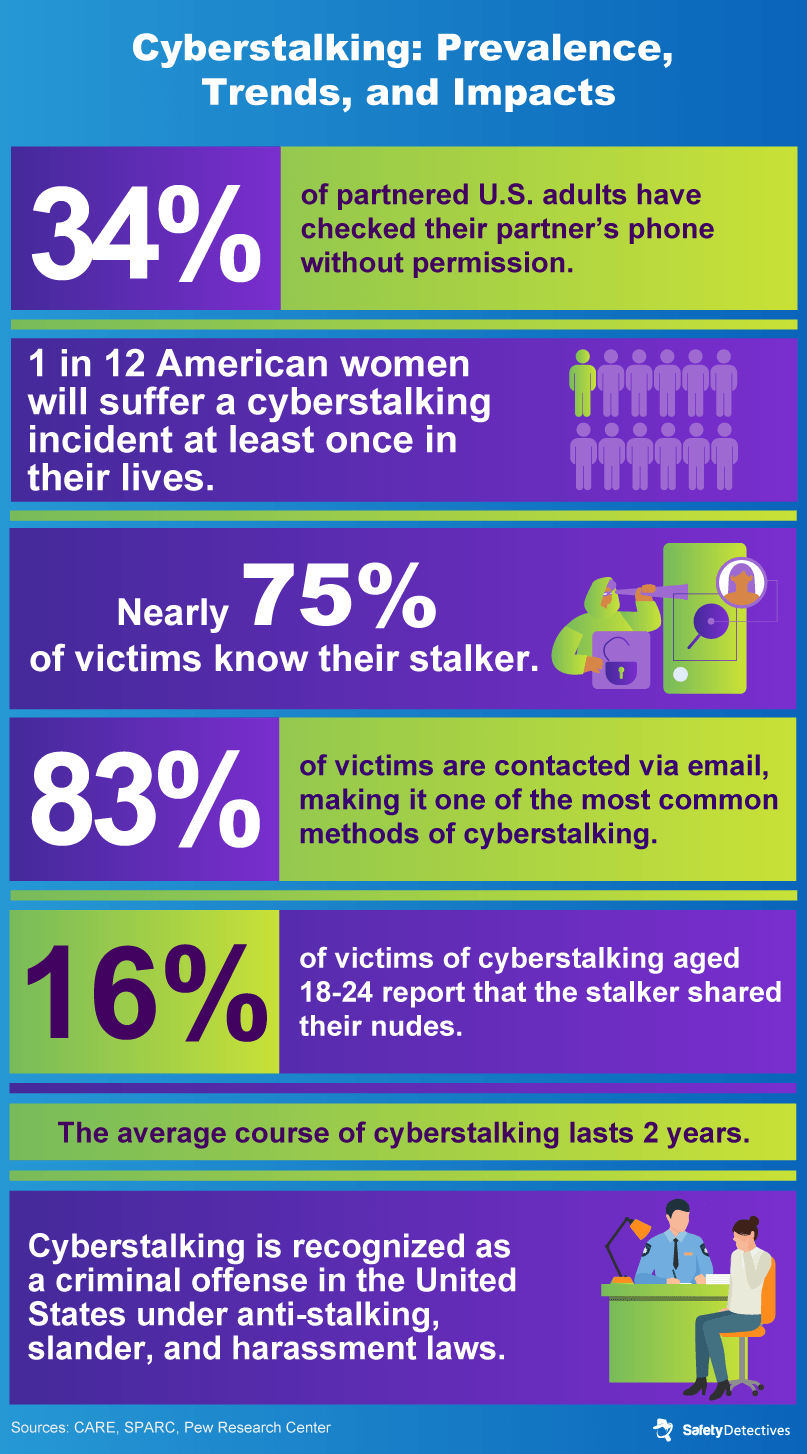
Statistics on Cyberstalking
From the share of victims who know their stalker to the amount of time victims are stalked for on average, here are some statistics on cyberstalking that might surprise you.
Privacy and Security Tips to Avoid Cyberstalking
You can protect yourself from cyberstalking by taking just a few proactive steps. From understanding the importance of privacy settings to being mindful of your digital footprint, these tips can greatly enhance your digital safety and give you peace of mind as you navigate the online world.
1. Keep a Low Profile
Maintaining a low profile online is crucial if you want to protect yourself from cyberstalking, especially if you use digital platforms for self-promotion or business purposes. Balance your need for online visibility with the importance of personal safety. Here are some key points to consider:
- Avoid Sharing Personal Details: Be mindful of the information you share online. Personal details such as your home address, phone number, and other sensitive information should always be kept private. Even seemingly harmless details can provide cyberstalkers with enough information to invade your privacy.
- Be Cautious with Location Data: Geotagging, which refers to the practice of adding geographical identification to photographs, posts, and updates, can be particularly risky. Avoid sharing your real-time location or tagging locations that you frequently visit. Remember that revealing your current location or routine spots can make it easier for a stalker to track you.
- Use Discretion in Business Promotion: If you use online platforms for business, exercise caution in how much company information you divulge. Yes, promoting your business is important, but ensure that you’re not unintentionally giving away personal information or details that could compromise your safety.
- Limit Real-Time Updates: Sharing your activities in real time can be a risk. Posting about events or locations after you’ve left, rather than while you are there, is often safer. This delay can help prevent someone from using this information to locate you.
- Review Your Digital Footprint: Regularly check your online presence and see what information about you is publicly available. You might be surprised at what you find and may need to adjust your privacy settings or remove certain details.
2. Update Your Software
Regular software updates can prevent your information from being leaked. Many of these updates are specifically designed to address and patch security vulnerabilities that have been discovered. Keeping your software up to date means that you’re equipped with the latest defenses against emerging cyber threats.
Most browsers update automatically, but you can manually check for updates in the browser’s settings menu.
Mobile devices are also at risk. Make sure that your smartphone’s operating system and all apps are up-to-date.
- For Android: Go to Settings > System > About phone or Advanced > Update
- For Samsung Galaxy: Go to Settings > Software update > Download and install
- For iOS: Go to Settings > General > Software Update
3. Don’t Let Social Networks Post Your Address or Phone Number Publicly
Another key step to protect yourself from cyberstalking is to control the visibility of your personal information, particularly your address and phone number. Here’s how you can manage this:
- Review Your Social Media Settings: Most social networks have privacy settings that allow you to control who sees your personal information. Ensure that your address and phone number are not visible on the “about” pages of your profiles. Regularly check these settings as platform updates can sometimes reset your preferences.
- Use Separate Contact Details for Business: If you use social media for business purposes, have a separate business phone number and email address. This segregation ensures that your personal contact details are not exposed to a wider audience, reducing the risk of them being misused by cyberstalkers.
- Consider Alternative Contact Methods: For business inquiries or situations where you need to provide an address, consider using a P.O. Box instead of your physical home address. This provides an extra layer of privacy and security, keeping your home location confidential.
- Have a Dedicated Email for Social Media: Having a separate email address exclusively for social media accounts can be a good practice. This helps you manage your online communications more effectively and also adds an extra layer of security. In case this email gets compromised, your primary personal or work email remains unaffected.
4. Be Wary of Public Wi-Fi
Using public Wi-Fi networks can be a risk factor. These networks, found in places like cafes, airports, and hotels, are convenient but can be easily compromised by hackers.
Public Wi-Fi networks are generally less secure than those that are private. They often lack strong encryption, making it easier for hackers to intercept the data you send and receive. This can include personal information like passwords, credit card numbers, and other sensitive data.
A safer alternative to using public Wi-Fi is to rely on your phone’s data connection. Cellular networks are generally more secure than public Wi-Fi because they use encryption, which provides added protection for your data.
5. Use a VPN and Security Software
A Virtual Private Network (VPN) is a powerful tool for enhancing your online privacy and security. Essentially, a VPN creates a secure, encrypted connection between your device and the internet. This encrypted tunnel ensures that your data is shielded from prying eyes even when you are using public Wi-Fi networks, which are known for their vulnerabilities.
One of the key benefits of using a VPN is that it hides your IP address. Your IP address can reveal a lot about you, including your general location and the internet service provider (ISP) you’re using.
By masking your IP address, a VPN makes it much more difficult for anyone to track your online activities back to you. This is particularly important for protecting your privacy, as a determined cyberstalker could potentially use your IP address to find out more personal information, such as your physical address or even financial details linked to your internet provider account.
6. Log Out of Your Social Media Accounts
Logging out of your social media accounts and then searching for them online is a valuable method to gauge what information is publicly accessible about you. This allows you to see your profile from the perspective of someone who isn’t connected to you, giving you a clear idea of what personal information might be exposed to potential cyberstalkers.
Most social media platforms provide a feature that lets you view your account as it appears to the public. Using this feature, you can adjust your privacy settings effectively. Set your posts to be visible to “friends only” or a similarly restricted setting.
In addition to adjusting privacy settings, manage your digital presence actively. Keep your timelines, feeds, and message threads free from negative or revealing comments. If you have old accounts that you no longer use, consider closing them. Inactive accounts can still be a source of personal information and may become a gateway for cyberstalkers to reconnect with or track you.
7. Use Strong Authentication Measures
Enabling two-factor or multi-factor authentication (2FA/MFA) on your accounts is one of the most effective ways to enhance your online security. This additional layer of security requires a password and username and also something that only the user has on them, i.e., a piece of information only they should know or have immediately to hand — such as a physical token or time-based one-time password (TOTP).
Using strong passwords and regularly updating them is equally important. A strong password should be complex and unique. Try to use a combination of letters (both upper and lower case), numbers, and symbols. They should be difficult to guess and different for each of your accounts. Regularly updating your passwords ensures that if one password is compromised, it will be quickly fixed and the damage limited.
8. Clean Up Your Digital Footprint
Your digital footprint comprises all the information about you that’s available online. This includes both your social media profiles and also any public records like voting registration, details on people-finder websites, news articles, forum posts, and more. Each piece of information contributes to the overall picture of your online presence.
To mitigate the risk of cyberstalking, actively manage and clean up your digital footprint:
- Review and Remove: Regularly search for your name online to see what information is publicly accessible. This can include your social media posts, comments on forums and articles, and any other platforms where you have a digital presence.
- Delete Old Accounts: If you have accounts on social media platforms or websites that you no longer use, consider deleting them. Old accounts can be a source of personal information that you may no longer want to be publicly accessible.
- Request Removal from People-Finder Sites: Websites that aggregate personal information can be a goldmine for cyberstalkers. Many of these sites have a process for requesting the removal of your information. Take the time to request these removals to reduce your online visibility.
- Stay Vigilant: Continually monitor the internet for new information about you. Setting up Google Alerts for your name can help you stay informed about any new mentions online.
- Limit Sharing of Personal Information: Be mindful of the personal information you share in new posts, comments, or profiles. Think twice before sharing locations, contact details, and other sensitive information.
What to Do If You Are Cyberstalked
If you’re already the target of a cyberstalker, you should know how to respond effectively. I’ll cover the essential steps you need to take to protect yourself, stay calm, and get the help you need.
1. Tell the Cyberstalker to Stop
Unless you live with your harasser, one of the first things you should do if you’re the target of cyberstalking is to issue a clear, written order to the stalker to stop all forms of communication with you. This step is crucial for several reasons.
First, it tells the stalker in no uncertain terms that their attention is unwelcome and must stop immediately. This can sometimes be enough to deter the stalker, as it clearly establishes their actions as unwanted and potentially illegal.
However, understand that in many cases sending this message may not stop the cyberstalker. Cyberstalkers are often driven by compulsions.
Still, having a record of your direct request that they stop can serve as evidence of your clear communication and rejection of their advances, which is essential if you need to escalate the matter to legal authorities.
If you do live with the person who is stalking you, you’ll need to have a conversation that establishes limits and boundaries. You’ll need to clarify your expectations regarding privacy and respect in your shared space.
2. End All Contact
After you’ve sent a clear message to the cyberstalker to stop, the next step is to completely stop any form of communication with them. Maintain this no-contact stance even if the stalker intensifies their efforts or the stalker’s messages become more frequent or aggressive in response to your silence.
Understand that the cyberstalker’s goal is often to provoke a response from you. Any response, no matter how negative, may be perceived as a victory in their eyes and could fuel further harassment.
Resisting the urge to respond can be challenging, but engaging with the stalker in any way can be misinterpreted as an invitation to continue their behavior. It may also give them more information and emotional leverage to use against you.
3. Document Everything
Meticulously document each instance of harassment. This means keeping copies of all interactions, whether through screenshots or printed pages. Be sure to capture the messages and profile pages, including usernames, from which the abuse originated.
This thorough documentation should extend beyond online interactions. If there are any offline activities related to the cyberstalking, such as unexpected appearances at your home or workplace, these should be noted as well.
The importance of this step lies in its utility for legal and protective action. Should the harassment escalate to the point where police intervention or action by social media platforms is required, a comprehensive record of these incidents can be invaluable.
In addition, keeping your own records helps ensure that you have an unalterable history of events. Abusers may try to delete their posts or profiles to cover their tracks, but your documentation preserves the evidence of their actions. This can be especially important in cases where the cyberstalker’s behavior fluctuates between active harassment and attempts to erase their digital footprint.
4. Block Your Stalker
Use the blocking feature offered by social media platforms. This tool allows you to restrict the stalker’s access to your account activity, effectively cutting off their direct line to you through these channels. Blocking is an easy way to enforce your boundaries and make it harder for the stalker to reach you.
However, understand that this measure has its limitations. Determined stalkers can create multiple new accounts, called “burner accounts,” to get around blocks and continue their harassment. While blocking can provide immediate relief to the stalker’s current account, it’s not a foolproof solution to persistent stalking behavior.
Despite these challenges, blocking remains an essential step. It prevents the stalker from contacting you through their known account or phone number, which can be a significant barrier to their efforts. For added protection, there are apps like Truecaller that automate the call and message blocking process, providing another layer of defense.
For more detailed guidance on how to use these features effectively, please visit our section on blocking strategies. Here you’ll find step-by-step instructions and tips to maximize the effectiveness of these tools in your fight against cyberstalking.
5. Don’t Use Your Home Computer and Disable Notifications
Especially if you live with your stalker, try not to use your personal computer for researching sensitive topics like domestic violence or getting help. Your device may be compromised or monitored by the stalker, particularly if they are a partner or housemate.
Instead, use a computer that the stalker can’t access. Public libraries, a trusted friend’s house, or even your workplace can offer safer alternatives for accessing the internet without the risk of your activities being tracked or observed.
You should also disable text and email notifications to your phone, tablet, and other devices. When notifications pop up on your screen, they can reveal sensitive information or private conversations to the abuser.
Turning off these notifications helps keep your incoming messages private, which is particularly important if you’re planning your next steps or getting advice on how to handle the situation.
6. Change Your Number and Email
Opting to change your phone number and email address can seem like a drastic measure, but in the face of persistent cyberstalking can be highly effective. This action creates a significant barrier, cutting off the line of communication the stalker has been exploiting.
When adopting this strategy, exercise caution in sharing your new contact details. Only provide this information to close family members and trusted friends, and make it clear that these details should not be shared with others without your explicit consent.
Should you continue to receive harassing emails, each email platform offers specific avenues for reporting and addressing these concerns:
- Gmail: If you’re receiving harassing emails from a Gmail account, you can report this directly through the Gmail Help Center. Search for “I would like to report a Gmail user who has sent messages that violate the Gmail Program Policies and/or Terms of Use.” Fill out the provided form with the necessary information and submit it.
- Outlook/Hotmail: For harassment through Hotmail, MSN, Live, or Outlook.com accounts, you can report the abusive message by forwarding it to abuse@outlook.com. Select the offending message, choose “Forward,” and address it to the abuse email.
- Yahoo: To address email harassment on Yahoo, mark the concerning email as “Spam” and then select the appropriate reason for reporting it from the drop-down list. Alternatively, you can visit help.yahoo.com, search for “Email a specialist,” and follow the instructions to report the harassing emails.
7. Report Your Stalker to Law Enforcement
When faced with cyberstalking consider involving law enforcement, particularly if there’s any concern for your safety. Before reaching out to the police, evaluate the situation by asking yourself a few key questions:
- Has the harasser made any explicit threats toward you or your loved ones?
- Do the messages from your harasser contain personal details about you or those close to you?
- Are you familiar with the individual who is harassing you?
- Is there an escalation in the behavior – in terms of frequency, intensity, or aggression?
- Are you worried that the public circulation of these messages might adversely affect your personal or professional reputation?
Remember, you don’t need to have an exhaustive collection of evidence or information to file a report. The act of reporting is a crucial step in itself.
To report cyberstalking, contact your local law enforcement agency. Initiating this contact is the first step in what could become an official investigation. Understand that filing a report does not automatically guarantee an investigation or result in charges being filed. However, it’s a necessary and valuable step.
Even if reporting the cyberstalking doesn’t lead to immediate results, the process is still beneficial. Having a copy of the police report can be an important piece of evidence. It can support your case when reporting the harassment to tech platforms, and it can be necessary for pursuing a restraining order or other legal measures.
8. Consider Counseling
Dealing with the emotional aftermath of cyberstalking, particularly when it involves someone close to you, can be immensely challenging. Setting boundaries in such situations is difficult and can take an emotional toll.
In these times, professional help can be incredibly beneficial. Counseling or therapy offers a supportive space where you can process your feelings, experiences, and fears.
A professional therapist can provide valuable tools to manage your emotions effectively, helping you to navigate the complex mix of feelings that accompany such experiences. They can also guide you in establishing and maintaining healthy boundaries, which is crucial for your emotional and psychological well-being.
Moreover, therapy can offer much-needed guidance through the process of recovery and healing. It can help you develop strategies to cope with the situation, rebuild your sense of self, and empower you to move forward.
9. Get a Restraining Order
Once you’ve filed a police report about cyberstalking, the next step can be to obtain a restraining order. This legal document serves as a formal directive, legally prohibiting the stalker from contacting or approaching you. It’s an enforceable measure that adds a layer of legal protection.
Obtaining a restraining order can also play a crucial role if your case proceeds to prosecution. The order itself stands as tangible evidence of the severity of the situation and the steps you’ve taken to address it. It demonstrates to investigators and the legal system that there is a recognized threat that requires intervention.
Additionally, a restraining order may effectively deter the stalker from continuing their behavior. For many stalkers, the realization that their actions have legal consequences can be a significant deterrent. Note, however, that while restraining orders can be powerful tools, their effectiveness can vary based on the individual situation and the stalker’s response to legal boundaries.
Steps Platforms Use to Prevent Stalking
Every social media site offers a variety of tools and features designed to prevent stalking and increase user safety. Reporting helps in flagging content that violates the platform’s guidelines, which can include harassment, threats, hate speech, and other forms of abuse. This can protect not just you, but also other users who might be exposed to such content.
By reporting abusive behavior, users contribute to the enforcement of the platform’s community standards. This ensures that content on the platform remains appropriate and safe for its user base, promoting a healthier online environment.
In addition, blocking allows individuals to protect their mental health by limiting exposure to harmful interactions. It can be a critical tool for users experiencing cyberbullying or harassment, providing an immediate solution to prevent further abuse.
But the question remains: Are these tools enough? While they are important steps in protecting users, the evolving nature of online interactions means that the fight against cyberstalking is ongoing.

Resources and Helplines
For those facing the challenges of cyberstalking, knowing where to turn for help is crucial. Helplines and resources dedicated to this issue provide essential support, advice, and intervention options.
They offer a safe space to discuss your concerns and receive guidance on how to navigate and resolve these complex situations.
- The Internet Privacy Handbook serves as a resource for protecting your online presence, covering methods for removing your personal information from websites that could expose or exploit it.
- CyberAngels is one of the oldest and most respected online safety education programs. It’s recognized not only as a provider of online safety education, but also as a thriving virtual learning community.
- The Cyber Helpline features a chatbot designed to communicate in clear, understandable language, making cybersecurity advice accessible to everyone, regardless of their technical knowledge.
- National Cybersecurity Alliance is a non-profit organization that advocates for the safe and responsible use of technology. The Alliance focuses on educating the public about effective strategies to protect themselves, their families, and their organizations from the ever-growing threat of cybercrime.
- National Stalking Helpline provides support to those who find themselves, or someone they know, being harassed or intimidated by another person. The helpline, which can be reached on 0808 802 0300, offers victims a confidential and compassionate ear, as well as expert advice and support.
- Get Cyber Safe aims to educate Canadians about the risks associated with the digital world and the simple yet effective steps they can take to stay safe online. It provides accessible, practical advice to help individuals protect their personal information and digital assets.
- Tech Safety App is designed to help individuals recognize and address technology-facilitated harassment, stalking, and abuse. The app helps users recognize such behavior and take appropriate action.
FAQs
1. What Is Cyberstalking?
Cyberstalking refers to the use of the internet or other digital means to harass, intimidate, or threaten an individual persistently. It can include monitoring someone’s online activities, sending threatening messages, or sharing personal information without consent. It’s a form of cyberbullying that can lead to psychological harm and poses a serious privacy concern.
2. What Are the Different Types of Cyberstalking?
- Harassment: Persistent and threatening online communication.
- Catfishing: Creating fake identities to deceive and manipulate.
- Hacking: Unauthorized access to personal data and accounts.
- Doxing: Publicly sharing private information without consent.
- Cyberbullying: Online intimidation, often in public forums.
- Identity Theft: Using someone’s personal data for fraudulent activities.
3. What Laws Protect Me from Cyberstalkers?
Laws protecting against cyberstalking vary by region:
- United States: Federal laws, including the Violence Against Women Act, recognize cyberstalking as a federal cybercrime under the interstate stalking statute. The National Conference of State Legislatures also provides resources on computer crime and spyware laws.
- Canada: Cyberstalking falls under criminal harassment laws, specifically section 264 of the Criminal Code, as outlined by the Department of Justice.
- United Kingdom: The Protection from Harassment Act (1997) and the Protection of Freedoms Act (2012) are used to prosecute cyberstalking cases.
- Australia: The Stalking Amendment Act (1999) addresses cyberstalking, encompassing contact through technology.
- European Union: While the European Parliament adopted a report on gender-based cyberviolence in 2021, it’s not yet classified under EU Crimes. The Istanbul Convention, signed by the EU in 2017, sets international standards, but not all member states have ratified it.
4. How Do I Stop Someone from Cyberstalking Me?
- Send a Clear Warning: Write a direct message to the stalker, clearly stating that they should not contact you anymore. This serves as a formal warning.
- Do Not Engage Further: If they attempt to contact you after your warning, do not respond. Any engagement can encourage them to continue.
- Document Everything: Keep printed copies of all evidence, including emails, texts, and screenshots. Document every instance of stalking, as this will be crucial if legal action is required.
- Report to Platform Authorities: Report the stalker to the specific platform where the harassment is occurring. For instance, if it’s on Facebook, use their reporting mechanism to flag the stalker’s behavior.
- Seek Police Assistance: If the stalking persists, contact the police. Provide them with all documented evidence and any previous reports made to online platforms.
5. What Should I Do to Prevent Cyberstalking?
- Use Strong Passwords: Create complex and unique passwords for each account. Avoid using easily guessable information like birthdays or common words.
- Log Out after Use: Always log out of email, social media, and other online accounts, especially when using shared or public devices.
- Secure Your Devices: Keep a close watch on your personal devices. Don’t leave your phone, tablet, or laptop unattended in public places.
- Be Wary of Public Wi-Fi: Avoid using public Wi-Fi for sensitive activities. Consider using a Virtual Private Network (VPN) for enhanced security.
- Manage Social Media Connections: Accept friend requests only from people you know. Set your social media profiles to private.
- Hide Your IP Address: Use services that mask your IP address to prevent it from being seen by others online.
- Adjust Privacy Settings: Regularly review and tighten your privacy settings on all social media platforms.
- Enable Multi-Factor Authentication (MFA): Add an extra layer of security to your accounts by implementing MFA.
- Check for GPS Trackers: Check your personal belongings and vehicle for any unauthorized GPS tracking devices.
- Use Security Features: Make full use of the security settings offered by your devices and online services.
- Choose Generic Screen Names: Avoid using identifiable information in your usernames or email addresses.
- Disable Geolocation: Turn off geolocation settings on apps and devices to keep your movements private.
- Be Cautious with Personal Info: Refrain from sharing sensitive personal information online that could be used to track or identify you.
The Bottom Line
Everyone should recognize what cyberstalking is and understand the steps they can take to prevent or end it. In an age in which technology is rapidly evolving, staying informed about the latest developments, especially regarding social media privacy policies, is more important than ever. This knowledge is key to ensuring your personal protection online.
Tech companies also bear a responsibility to continually update and strengthen their data protection measures. As users, we rely on these companies to safeguard our information and provide secure digital environments. These organizations must prioritize user safety and take proactive steps to combat cyberstalking, ensuring a safer online experience for everyone.