
One of the leading online retailers in Brazil, Natura&Co, has been informed of a significant data leak within its website, https://www.natura.com.br.
More than 250,000 customers that had previously ordered beauty products from the website had their personal information made available to the public without Natura’s knowledge. Payment information from 40,000 customers related to a third-party company, Wirecard, was also publicly available for over 2 weeks.
Who is Natura?
Natura&Co is a Brazilian perfumery/cosmetics company headquartered in São Paulo with commercial operations extending globally as a result of online sales. In total, the company has over 40,000 employees and generates around US$10 billion in revenue each year. The parent company also owns Natura Cosméticos, Aesop, The Body Shop and Avon with sales revenues generated in over 73 countries across all continents.
The security team at Safety Detectives, currently led by Anurag Sen, discovered a significant data leak including various items of personal information on a 272-gigabyte Amazon-hosted server, located in the US.
Strangely, since the data leak was discovered and Natura being informed, the size of the data leak has been reduced from 272GB to 27.2GB, according to server logs — this is a strong indication of purposeful impropriety aimed at concealing the severity of the leak. For example, an ill-intentioned hacker removing a precise number of records to conceal their actions.
Moreover, according to server logs, the size of the data breach has varied over the course of several days with the latest estimate showing 69GB.
Around 90% of users were Brazilian customers although other nationalities were also present including customers from Peru.
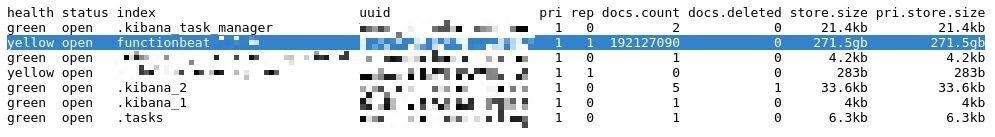
The data leak was first discovered on 12 April 2020, although the Safety Detectives security team was able to confirm that hundreds of gigabytes of information were available as early as 26 March 2020.
Natura was immediately contacted, and its management informed of the leak including the potential ramifications of the vulnerability discovered on its server. This report has now been published after Natura secured its server and removed all private data from public view.
A few days before the publication of this report, while we had confirmed the server was secured, Anurag discovered a new leaking server owned by Natura. We tried to reach out to the company as soon as we discovered it, but again nobody replied to us. We (again) reached out to Amazon so they could inform their customers and after a few days, the server got secured.
During these few days, a bigger server (1.3TB) had been exposed, leaking similar data to the previous one. In addition to what was in the first server found, we could see browser cookies of their users as well as some other additional information. We didn’t spend much time looking into this server as it seemed quite similar to the previous one and owner had already been confirmed.
What was leaked?
The compromised server contained website and mobile site api logs thereby exposing all production server information. Furthermore, several “Amazon bucket names” were mentioned in the leak including PDF documents referring to formal agreements between various parties.
In total, the vulnerable database contained over 270GB of data with more than 192 million records.
More specifically, the following data points were discovered:
- Full name
- Mother’s maiden name
- Date of Birth
- Nationality
- Gender
- Natura.com.br login credentials including hashed passwords
- Welcome email template
- Username and nickname
- MOIP account details
- Api credentials including unencrypted passwords
- Previous purchases
- Telephone number
- Email and physical addresses
- Access token for wirecard.com.br

The exposed information contained login credentials for over 250,000 customers, including what’s known as a “hashed password with salts”. This information potentially allows hackers to find the correct password for each user by brute forcing the hash and obtaining full access to customers’ accounts.
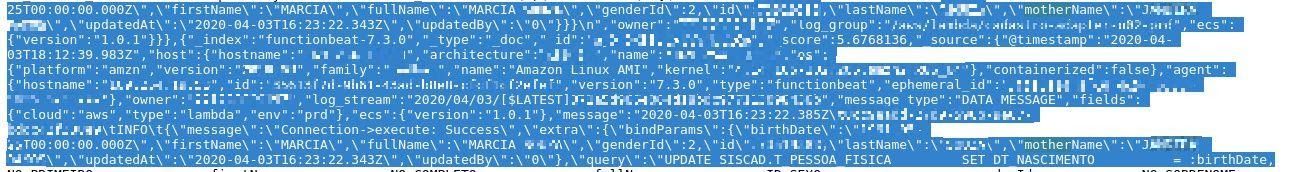
The database also contained over 40,000 wirecard.com.br Moip account details with access tokens.
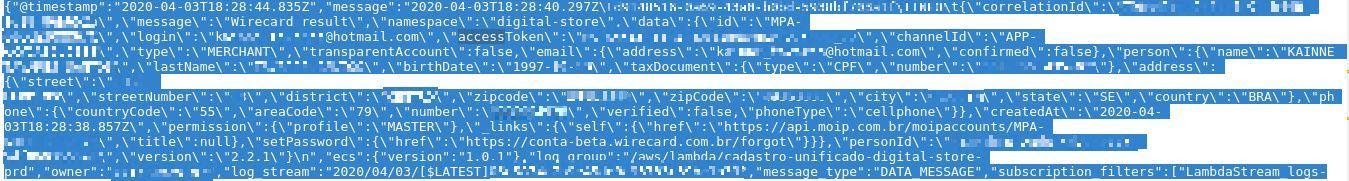
wirecard.com.br – (MOIP) credentials exposed with access token.
In addition, internal technical confidential details such as a .pem certificate key and a “client secret” were discovered and publicly accessible.

Third-party merchant Wirecard
Natura’s database has a merchant relationship with MOIP/wirecard.com.br – a third party company that facilitates online payments for Natura.
Wirecard commenced its European operations in 1999 and has operated in Brazil since 2017. In 2016, MOIP became part of the global payments company Wirecard.
In 2018, the company’s valuation exceeded €20 billion on the Frankfurt Stock Exchange, making it one of the 30 largest publicly traded companies in the country.
From the information discovered on the server, delivery details like purchase amount, cart id and cart details were viewable, although associated personal details were not matched to the information.
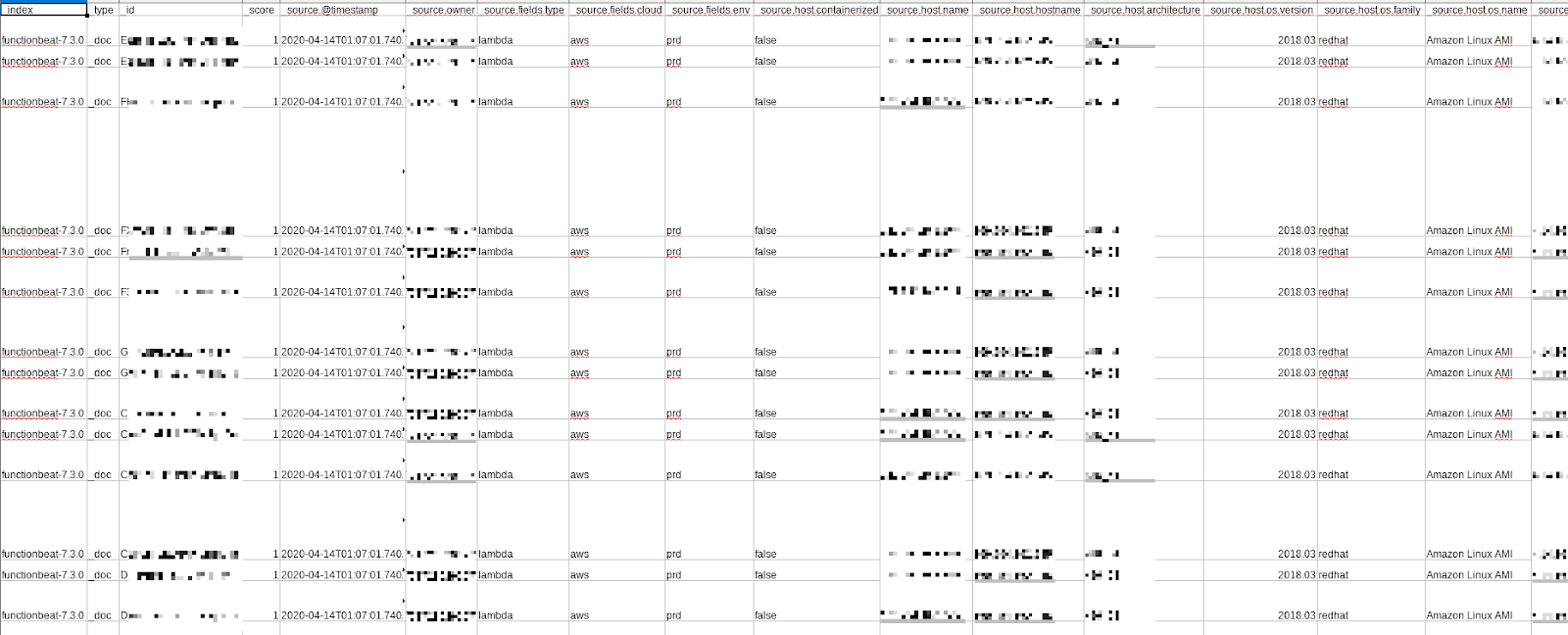
Data leak shows previous purchases and cart information including IP address

Detailed information about purchased products and order details
Data Breach Impact
Displaying personally identifiable information including passwords on an unsecured server is never wise and could potentially lead to severe cybersecurity ramifications including financial and identity fraud, phishing attacks and ransomware vulnerability.
Natura’s database contained the physical addresses, phone numbers, and personal information of customers including credentials such as mother’s maiden names that could be harnessed by nefarious hackers to cause severe financial, social and reputational damage to those affected by the leak.
One example would be using mother’s maiden names to answer security questions and potentially access email accounts and cloud services that could in turn be used maliciously to gain deeper access to someone’ private information. Alternatively, welcome email templates could be used to initiate phishing scams whereby the user clicks on a link sent by the hacker, under the false impression the email originated from Natura.
Moreover, the exposed .pem file creates a significant risk since it contains the key/password to the EC2 Amazon server.
Instances of personally identifiable information being exposed, could potentially lead to identity theft and fraud since they can be used by attackers for identification in various sites and locations.
Also, exposed password hashes and salts further compromise the safety of private data because possessing salts simplifies intrusion for attackers. Salts are additional data, used to encrypt passwords thereby making it more difficult for passwords to be compromised, even if the hash is exposed.
The risk of phishing and phone scams is also raised by the Natura data leak. Private details could be used to establish trust with the ultimate result of users being targeted and tricked into providing further information including banking and security information.
Leaked data could be used to extract further sensitive information and lead to identify fraud as well as criminal activity carried out under ‘false flag’ pretences.
Exposed details about the backend, as well as keys to servers, could be leveraged to conduct further attacks and allow deeper penetration into existing systems.
Preventing Data Exposure
How can you prevent your personal information from being exposed in a data leak and ensure that you’re not a victim of attacks – cyber or real-world – if it is leaked?
- Be cautious of what information you give out and to whom
- Check that the website you’re on is secure (look for https and/or a closed lock)
- Only give out what you feel confident cannot be used against you (avoid government ID numbers, personal preferences that may cause you trouble if made public, etc.)
- Create secure passwords by combining letters, numbers, and symbols – a password manager such as Dashlane can make this easier
- Do not click links in emails unless you are sure that the sender is legitimately who they represent themselves to be
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust
- Avoid using credit card information and typing out passwords over unsecured WiFi networks
- Find out more about what constitutes cybercrime, the best tips to prevent phishing attacks, and how to avoid ransomware
About Us
is the world’s largest antivirus review website.
The Safety Detective research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data.
Published on: May 19, 2020