
Short on time? Here’s how to quickly check if an email attachment is malicious:
- Install reliable antivirus software. Norton is my favorite antivirus for scanning emails for viruses, but there are other antiviruses you can use, too.
- Let the antivirus scan and remove any malware. Your antivirus will analyze the file and check for any malware hidden inside of it. Make sure that real-time protection is turned on; otherwise, future email threats might not get detected.
- Practice good online safety habits. Verify the sender of every email you receive, don’t click suspicious links or download files from unknown sources, and regularly back up your files.
Email attachments are an all-too-common source of malware. Cybercriminals know how easy it is for someone to open a file contained in an email. Being criminals, they like to take advantage of social engineering tactics by pretending to be legitimate sources. They’re pretty good at this, so it can be tricky to know if an email is safe.
Fortunately, there are ways to tell whether emails contain infected files or not. These range from looking for attachments with suspicious file formats and checking for strange grammatical errors to having an antivirus installed. You should always be suspicious of unexpected emails and make sure the sender’s address matches a contact or other verifiable source.
To protect yourself from viruses buried in emails, you’ll need a good antivirus. I recommend Norton as my top antivirus in 2024. It has a flawless malware scanner and great real-time protection against incoming viruses. For extra protection, I recommend also getting Safe Email, a subscription add-on that scans emails for viruses and other threats before you even open them.
How to Detect & Remove Malicious Email Attachments (Step-by-Step Guide)
Scanning email attachments is different from running regular antivirus scans. I’ll be using Norton in this example, but most antiviruses will have similar steps. Unfortunately, attachments in encrypted emails can’t be scanned until the file has been opened or saved, but luckily Norton’s real-time protection will block malware the second you attempt to open it.
Step 1. Install Reliable Antivirus Software
The first step is to purchase Norton from its official website. After you do so, the download process will start. Once this is done, open the program. The installation wizard will walk you through the process — all you have to do is click a few prompts, customize some settings, and Norton does the rest.

Step 2. Turn on Real-Time Protection
Norton’s Auto-Protect feature scans every file that you attempt to download. If it catches any malware, it simply removes it. Open up the Device Security tab, click the drop-down menu, followed by Advanced, and make sure Auto-Protect is toggled on. This will make it so Norton scans all incoming files and downloads and ensures that you’re protected from malicious emails.

While you’re at it, make sure AntiSpam is turned on — it’s a great precautionary feature that filters out email phishing scams before they reach your inbox. From Device Security, open up the Settings tab and click on AntiSpam to make sure it’s on. Both are on by default, but it’s always worth double-checking.
For additional safety, you can add a Safe Email subscription to your Norton account, too. It’s easy to do from your account page but the setup process varies depending on which email client you use. Either way, once you’ve got Safe Email set up, you can connect up to 5 email addresses. All incoming messages will automatically be scanned for viruses, phishing links, and scamming attempts and given a ‘Safe’ or ‘Suspicious’ tag. Safe Email didn’t work perfectly in my tests, but it did flag most of the malicious emails that landed in my inbox.
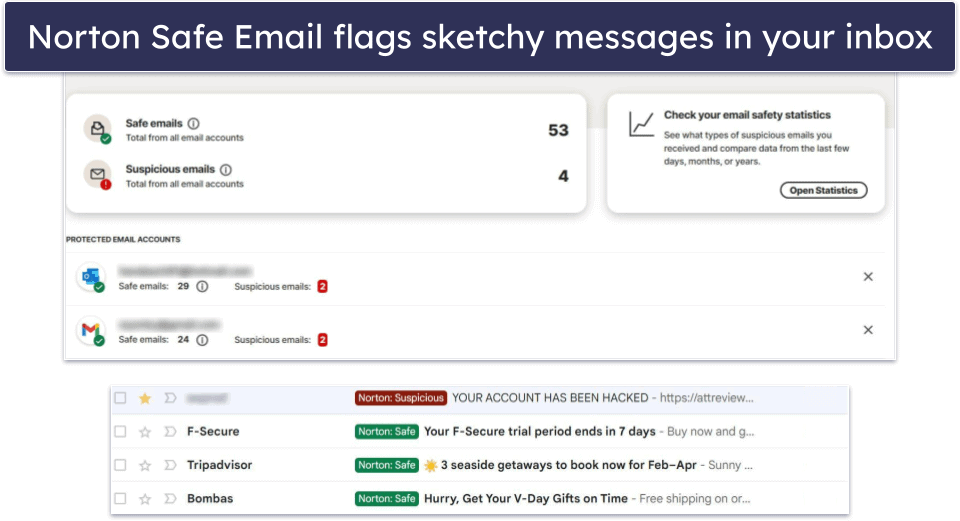
Step 3. Scan the File With Your Antivirus
Though Norton will have blocked any email viruses, I still recommend you regularly run a malware scan on your device. If you think you may have opened a malicious attachment before downloading Norton and activating its real-time protection, or you’re just unsure, this is doubly important. To run a scan, open Norton’s Device Security tab, tick the Full Scan checkbox, and start the scan. Norton will analyze your computer to find any irregularities caused by malware — including malicious email attachments.

It’s also possible to run a custom scan on specific files, so if you do download an email attachment and are still suspicious, you can scan it without waiting on a full system scan. To do this, click on Scans, then Custom Scan, and finally select the file you want to scan.
That said, I don’t recommend downloading suspicious email attachments for the sole purpose of testing them. If you accidentally open one, there could be trouble. What’s more, a good antivirus like Norton will detect whether an email attachment has malware without requiring you to actually download and scan the file.
You can generally rely on passive protections to keep you safe from email viruses. Still, I recommend running a full scan to make sure there isn’t any malware lurking on your device. It’s always better to be safe than sorry!
Step 4. Remove Any Malware That’s Found
After you’ve run a scan, Norton will flag any files it deems unsafe and quarantine them for you. You’ll have the option of removing them or keeping them. While it’s usually best to let the antivirus do its job and remove any files it thinks are unsafe, it’s worth double-checking, just to make sure personal files aren’t lost.

After removing the malware, restart your device. I recommend running a second full scan at this point to ensure there’s no lingering malware — especially if you think you may have opened any suspicious attachments or downloads. You’ll also want to uninstall leftover applications if you’ve been infected by unwanted programs. For example, on Windows 11, click on the Start button and head to the Control Panel. From there click on Uninstall a program and remove any lingering applications that look suspicious.
Step 5. Practice Good Online Safety Habits
Even with the best antivirus, it’s important to practice good online safety habits to minimize the risk of encountering malicious emails and attachments. Here are some key practices to follow:
- Be cautious with email attachments from unknown senders. If you don’t know the sender, and they’re peppering you with attachment-laden emails, chances are they contain a virus or some kind of scam.
- Verify the legitimacy of the sender before opening any attachments. For example, if the sender claims to be with a legitimate business, verify the company’s official email address by checking their website.
- Avoid clicking on suspicious links from untrusted sources. Much like attachments from unknown sources, untrustworthy-looking links should simply be avoided.
- Make sure everything on your system is updated. This applies to your antivirus, your operating system, drivers, and any other third-party software you use.
- Regularly back up your important files. Use an external storage device or cloud storage so your files will be safe even if your device gets compromised.
By following these steps, you can stay protected from malicious email attachments and other nasty threats. Criminals are constantly coming up with new ways to trick people into downloading malware or forking over information through email, so it’s important to always stay vigilant.
Best Antiviruses for Protecting Against Email Viruses in 2024
Quick summary of the best antiviruses for protecting against email viruses:
- 🥇 1. Norton 360 — Best antivirus to protect against email viruses and other threats.
- 🥈 2. Bitdefender — Cloud-based antivirus with customizable web protection.
- 🥉 3. TotalAV — User-friendly antivirus with email scanning & more.
Why You Need to Scan Email Attachments for Viruses
Email attachments often contain viruses. When opened, they can infiltrate your system, compromising data and disrupting your device’s functionality. Because of this, it’s essential to enable features like Norton’s Auto-Protect to protect yourself from malicious attachments. If you don’t use it (or the equivalent real-time protection tool offered by another antivirus), you’ll be at risk of suffering debilitating malware attacks.
Cybercriminals often use emails as a delivery mechanism for malware, including but not limited to:
- Ransomware. This type of malicious software encrypts files and demands a ransom for their release.
- Trojan horses. These programs disguise themselves as legitimate files or software, but they contain malicious code that can harm your system or steal sensitive information.
- Spyware. This will gather information about your online activities and can compromise your privacy.
- Keyloggers. These capture keystrokes, enabling attackers to collect sensitive data like passwords and credit card information.
- Phishing attacks. This is a common trick that aims to deceive users into providing personal information or clicking malicious links, which can lead to identity theft or financial loss.
Both inbound and outbound emails pose risks. Inbound emails may contain infected attachments that can compromise your device and data, while outbound emails can inadvertently transmit malware to others if your system is already infected. By scanning email attachments, you can detect and neutralize malware, protecting yourself and others from potential harm.
How to Know if an Email Attachment Is Infected With Malware
Identifying malicious email attachments is crucial to protecting your device and data from malware infections. Here are some warning signs to look out for:
- Suspicious sender. Be cautious if the email comes from an unfamiliar or suspicious sender and look for abnormalities like extra characters or an unusual domain in the sender’s email address — even if it sounds like a business you know and trust.
- Unexpected or urgent emails. Exercise caution when receiving unexpected or unusually urgent emails, especially those requesting personal information or demanding immediate action.
- Poor grammar and spelling. Emails with significant grammar and spelling errors may indicate malicious intent, as legitimate organizations usually maintain professional standards.
- Unusual file extensions. Be wary of email attachments with unusual or suspicious file extensions, such as executable files (.exe) or script files (.js or .vbs).
You should also check the properties of all your downloads. On Windows, right-click on the attachment, click Properties, and review details such as file size, file type, and file extension. Unusually large file sizes or unexpected file types may indicate potential malware.
Finally, to determine if an email attachment is infected with malware, use your antivirus. The best antiviruses have precautionary security features like anti-spam measures and real-time protection. This will tell you with perfect accuracy whether emails contain any malware, and it will also block you from opening malicious attachments by mistake.
What to Do if You Open a Malicious Email Attachment
If you’ve opened an infected email attachment, it’s crucial to take immediate action to minimize the potential damage and protect your device and data. Here’s what to do if you suspect you just downloaded malware:
- Disconnect from the internet. Quickly disconnect your device from the internet to sever communication with potential attackers and prevent further infiltration or data exfiltration.
- Scan your device. Run a comprehensive scan using Norton or another top antivirus to detect and remove any malware that may have infected your device. Follow the recommended actions provided by the software to quarantine or eliminate the detected threats.
- Isolate the affected device. If you’re using a shared network, inform your system administrator or other affected parties about the situation. Disconnect your device from the network to prevent the infection from spreading to other devices.
- Change your passwords. Immediately change the passwords for all your online accounts, including email, banking, social media, and any other critical services you use. Ensure that you create strong, unique passwords for each account to enhance security. I recommend using a premium password manager.
- Monitor your accounts. Keep a close watch on your financial and online accounts for any signs of suspicious activity. If you notice any unauthorized transactions or unusual changes, promptly report them to the appropriate service providers.
- Update your software. Ensure that your operating system, antivirus software, and other essential applications are up to date with the latest security patches and updates. Regularly updating your software helps protect against known vulnerabilities and strengthens your device’s defenses.
- Educate yourself. Take the opportunity to learn more about phishing scams, email security, and safe online practices. Familiarize yourself with the warning signs of malicious emails and exercise caution when opening email attachments. Verify the sender’s identity before interacting with any suspicious emails to avoid falling victim to similar attacks in the future.
By following these steps, you can mitigate the impact of malicious email attachments and fortify your device against potential threats.
Which Email Attachments Are Safe to Open?
Certain file types are generally considered safe to open as email attachments, while others pose a higher risk of containing malware. Safe file types often include image files (such as .JPEGs and .PNGs), audio files (such as .MP3s and .WAVs), and video files (such as MP4s or .AVIs). These file types are commonly used for media sharing and are less likely to carry malicious code.
On the other hand, file types that are commonly used for malware distribution include executable files (such as .exe), archive files (such as .zip or .rar), documents (including .doc and .pdf), and scripts (such as .js or .vbs). Cybercriminals frequently employ these file types to deliver malware payloads and exploit vulnerabilities in software.
That said, no file type is completely immune to the risk of containing malware. Malicious actors can manipulate file extensions or use techniques to disguise malware within seemingly harmless files, including PDFs. That’s why it’s crucial to exercise caution when opening email attachments, even if they appear to be from a trusted source.
What Can Happen if You Open a Malicious Email Attachment?
Opening a malicious email attachment can have severe consequences, exposing your device and data to various types of email viruses. Malware, such as spyware, adware, or keyloggers can be unleashed upon your system, compromising your privacy and potentially leading to identity theft.
Ransomware, a particularly damaging type of email virus, can encrypt your files, rendering them inaccessible until a ransom is paid. What’s worse is that each strain of ransomware needs a unique decrypter, meaning some of your data may be inaccessible for a long time.
Phishing attacks may trick you into revealing sensitive information, such as login credentials or financial details, which can then be exploited for fraudulent purposes. Moreover, email viruses can spread across your network, infecting other devices and potentially causing widespread damage.
By opening a malicious email attachment, you expose yourself to the risk of data loss, financial harm, identity theft, and system instability. To protect yourself, exercise caution when handling email attachments, use reliable antivirus software, and stay updated with the latest and best security practices.
How to Scan Email Attachments on Mobile Devices
Malicious emails can infect desktop and mobile devices alike. Luckily, you can protect your phone just as you do your computer. First of all, you’ll need a solid mobile antivirus. Install a top Android antivirus from the Google Play Store or a top iOS program from the Apple App Store to ensure you stay protected. The best will provide excellent real-time protection, including web protection that monitors email attachments. Make sure that these features are turned on.
If you’re an Android user, to ensure an attachment you’ve downloaded is safe, scan the file before you open it, just as you would on a desktop device. Open your chosen mobile antivirus and choose to run a scan on the file. Once the scan is complete, follow the instructions to remove any malicious files that are detected. iOS users can’t run malware scans and aren’t as susceptible to malware as Android users, but the biggest risk here is phishing attempts — so be sure to read up on how to identify suspicious emails.
Frequently Asked Questions
What kinds of viruses are in emails?
Emails can contain various types of viruses, including adware, ransomware, trojans, and phishing attacks. These viruses are often hidden within email attachments, which, when opened, can infect your device or compromise your data. While antiviruses can detect and beat the malware in an email, you still have to be careful.
Cybercriminals use email attachments as a common delivery method for viruses, aiming to gather sensitive information, display unwanted advertisements, encrypt files for ransom, or deceive recipients into revealing personal information.
Which antivirus has the best protection against email viruses?
I think Norton offers the best protection against email viruses in 2024. Its powerful malware scanner and real-time protection excel at identifying and blocking email-borne threats (plus every other kind of cyberattack). Its email protection tools also block dangerous incoming and outgoing emails, keeping your inbox free from scammers and hackers.
That said, any of my top antiviruses are more than capable of protecting you from viruses. My other favorite, Bitdefender, also had excellent web protection, blocking as many phishing attempts as Norton.
Can I get email viruses on my phone?
Yes — mobile devices are susceptible to email viruses. Cybercriminals may use malicious email attachments or links to infect your phone with malware. To protect your device, it’s essential to exercise caution when opening email attachments, especially from unfamiliar sources, and have a reputable antivirus like Norton installed.
Regardless of your operating system, malicious emails are bad news. Even though some files, like image and video files, are often safer than documents, scripts, and PDF files, they can still pose a serious risk to your phone. That’s why it’s important to regularly check files on your phone too.
What are the common signs of a phishing attack?
There are common signs that indicate a potential phishing attack, including suspicious email addresses or domains, spelling and grammar errors in the email content, urgent or alarming requests for personal information, and unexpected emails from known entities. Phishing attacks rely on social engineering techniques to manipulate you into downloading email attachments or clicking links.
By paying attention to the email address or domain, carefully reviewing the content for errors, being wary of anything that sounds too good to be true (like an advertisement for a massive sale on a shady website), and always verifying the source of an email, you can protect yourself from falling victim to phishing attacks.