
Updated on: September 17, 2024
Short on time? Here’s how to remove the Chrome.exe virus:
- 1. Scan Your Device — Run a full disk scan using a premium antivirus like Norton to find the Chrome.exe virus and any other malware.
- 2. Remove The Chrome.exe Virus — Once the scan is done, let your antivirus get rid of all files related to the Chrome.exe virus.
- 3. Stay Protected Online — To avoid more infections, choose a premium antivirus like Norton, which offers flawless malware detection rates, real-time protection, and many other tools to keep you safe online. Norton comes with a 60-day money-back guarantee on all plans, so you can try it risk-free.
The Chrome.exe virus is a trojan that can seriously damage your computer. Trojans are malware files that pretend to be safe programs on your device and then steal your data and deploy other malware files like rootkits and worms. In this case, the Chrome.exe virus imitates Chrome.exe, the executable file that opens and runs the Chrome browser on your computer.
Fortunately, it’s very easy to remove the Chrome.exe virus if you follow the right steps. The best way to rid your device of trojans and other malware files is with one of the top antiviruses on the market in 2024. A comprehensive antivirus will detect and safely remove the Chrome.exe virus and prevent future malicious files from infecting your computer. Norton is our top antivirus software pick for 2024, and its plans start at just $54.99 / year*, with a 60-day money-back guarantee.
Try Norton (60 Days Risk-Free)
How Chrome’s Secure Sandboxing Makes It Hard to Detect Trojans
It can be really difficult to figure out if you have a trojan masquerading as Chrome.exe on your system, and here’s why. If you look at the Task Manager while Chrome is open, you’ll see numerous instances of Chrome.exe running. This isn’t an indication of being infected by the Chrome.exe virus. Chrome.exe runs a separate process for each of its different windows, tabs, web apps, and extensions — this security practice is called “sandboxing”. Sandboxing is a safety measure to stop your entire web browser from crashing if one of these web apps or plugins fails (or gets hacked).
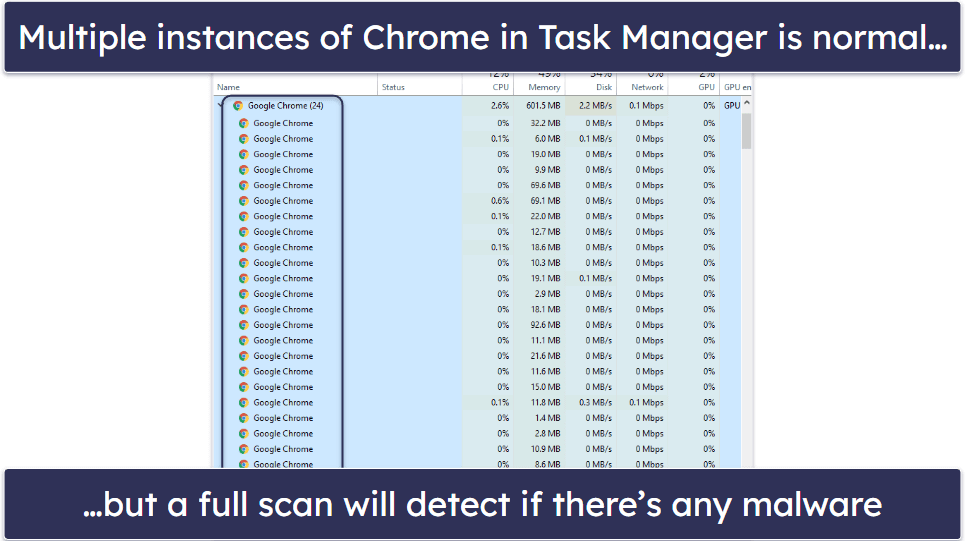
Trojans rely on Chrome’s sandboxing to hide their fake instances of Chrome.exe in the crowd of legitimate Chrome.exe files that run any time you open your browser. One method for detecting a fake or malicious instance of Chrome.exe is to close out of Chrome and check Task Manager. If Chrome.exe is still running once you’ve exited the Chrome browser, it’s probably a malware file. However, sophisticated trojans and rootkits are able to detect when your browser is running — so the only way to be sure your device is safe is to run a full system scan using a comprehensive antivirus scanner.
Step 1. Run a Full System Scan With Your Antivirus
It’s really important to disconnect any USB devices from your computer before initiating a scan. This includes USB sticks, portable hard drives, and mobile phones. Malware, like the Chrome.exe virus, can replicate itself onto any of these devices.
Next, you need to run a comprehensive virus scan with your antivirus (I recommend Norton). Make sure to select a full-disk scan, which will scan every single file and process on your computer. When the full-disk scan finds malware, it will place the infected files into a quarantine vault. Remember, the full-disk scan may take 4-5 hours, so I recommend that you schedule it for a convenient time or when you’re not planning to work on your PC.

Also, don’t cancel the scan until it’s finished — even if the compromised file appears on the infected file list, malware is able to replicate and you want to make sure your antivirus has found every instance of it.
Once the full scan has finished, all malware on your computer should be quarantined, including the Chrome.exe virus. Now, you’re ready for step 2.
Step 2. Delete Any Infected Files
All of the malware your full-scan detected will be displayed in your antivirus’s quarantine vault. While it’s best to delete all of the infected files, advanced users can look through the infected file list and choose to keep false positives — but only keep a file if you’re 100% sure that it’s safe.

Once you’ve gone through the list and deleted all of the infected files, you need to restart your PC. This is because sometimes malware loads itself into your computer’s memory and continues to run even after the scan. But when you restart your PC, Windows will reload its memory without the infected process.
When your PC has restarted, run another full disk scan to ensure all instances of the malware have been removed. The good news is the second scan shouldn’t take as long — programs like Norton can remember which files have already been scanned and they only check for any discrepancies or new files that have appeared since your last scan.
When the second full disk scan is complete, look through your infected file list once more. There shouldn’t be any infected files, but if there are you’ll need to delete them, restart your PC once more, and continue this step until all of the malware is wiped clean from your device.
When you’re sure all infected files are gone, your PC is free from all malware. However, you’ve experienced first-hand how easy it is for malware to infect your computer, and now you need to take measures to prevent it from happening again. The best part is that it’s easy to avoid catching a virus if you follow our advice.
Step 3. Keep Your Device Protected From Getting Re-Infected
Cybercriminals are constantly developing new and sophisticated ways to infect users’ devices in 2024. Users have to remain vigilant and take a few preventative steps to protect themselves. While this may seem challenging, you can keep your computer and personal information safe if you follow these steps.
- Don’t Download Suspicious Files. Most malware spreads through suspicious emails and untrustworthy websites. So, if you see a suspicious email or don’t recognize a site, avoid clicking on it or downloading any files from it until you have verified that it’s safe. Always ensure you have an antivirus running with real-time protection, which actively scans files, websites, and emails for suspicious links and attachments and prevents you from downloading them.
- Keep Your Software, OS, and Drivers Up-To-Date. If you’re running on outdated software, operating systems, or drivers, your computer is vulnerable to an attack. However, many antiviruses (like McAfee) have vulnerability scanners that ensure your computer has the latest versions of your software, operating system, and drivers. McAfee also offers a free security assessment that scans your PC for any apps that need an update, lets you choose which updates you want to run, and tells you which updates you need to manually install.
- Secure Your Wireless Network and IoT Devices. Type your router or IoT device’s brand and model number into Google (or check the product manual) to learn how to log into its settings. Next, navigate into the settings and create a strong password (the best passwords are 20+ characters long and include numbers and special characters). I recommend purchasing an affordable password manager like 1Password to help create and store a strong password. A password manager can generate virtually unbreakable passwords for you and then store them in a password vault that is protected with military-grade encryption. This means hackers will never be able to compromise your passwords, and you’ll never have to worry about forgetting a password. If you have to use an unsecure network, for example when you’re out and about, make sure to use a quality VPN like ExpressVPN to protect your privacy.
- Download a Secure Antivirus Program. The safest way to prevent your computer from getting infected is to download a secure antivirus program like Norton. Norton comes with tons of features to protect you in 2024, including really good malware detection rates and excellent web protection.
3 Best Antivirus Programs for Removing the Chrome.exe Virus
Quick summary of the best antiviruses for removing the Chrome.exe Virus:
- 🥇1. Norton — Best antivirus for removing Chrome.exe and other malware in 2024.
- 🥈2. Bitdefender — Feature-rich antivirus with a lightweight and effective scanner.
- 🥉3. McAfee — Includes excellent web security and very cost-effective plans.
Frequently Asked Questions
Is Chrome.exe a virus?
In most cases, Chrome.exe isn’t a virus. It’s a safe and trusted process used by Google Chrome’s web browser. Chrome.exe runs multiple instances of Chrome.exe in your Task Manager (and here’s why).
However, the Chrome.exe virus disguises itself as a legitimate Chrome.exe file. Your computer is likely infected with the Chrome.exe virus if your PC is frequently crashing, exposing you to lots of pop-up ads, or if you can’t remember installing Google Chrome but it’s in your Task Manager. The best way to find out whether you have the Chrome.exe virus is to run a full system scan using a comprehensive malware scanner like Norton.
Can I uninstall the Chrome.exe virus?
Yes, and it’s really easy to do it. First, purchase an antivirus (Norton is my favorite), and then follow these steps — run a full-disk scan, which will check your entire computer for malware, including trojans (like the Chrome.exe virus), rootkits, computer worms, and more, and place them in quarantine. Next, delete all of the infected files in your quarantine vault. Then, restart your computer and run another full scan to make sure all of the malware was detected and removed.
Once you have deleted the Chrome.exe virus and all other malware from your computer, you can keep your computer from getting reinfected by following these preventative measures:
- Don’t click on suspicious links or download files from unknown sources.
- Confirm that all of your drivers, software, and operating systems are updated with the most recent versions.
- Make sure you purchase a top-quality antivirus program that includes real-time protection (my top pick is Norton).
Is Chrome.exe dangerous?
Chrome.exe is the executable file that launches and runs the Chrome web browser on your device. Seeing it in your Task Manager just means Chrome is active. However, be cautious — some malware files like the Chrome.exe virus can imitate Chrome.exe to sneak into your system unnoticed.
Malware files that pretend to be legitimate files are called trojans, and they are very dangerous. Trojans can create a backdoor into your system and allow cybercriminals to steal or modify your files — or even spy on you. To make sure that you don’t have the Chrome.exe virus running on your system, follow my steps.
How can I check if Chrome.exe is legitimate or a virus?
The best way to figure out if your version of Chrome.exe is legitimate or a virus is to run a full scan using a comprehensive antivirus scanner.
However, you can also check the Chrome.exe file manually.
- If you can’t remember installing Chrome, bring up your Task Manager by pressing Ctrl+Shift+Esc.
- Right-click on the suspicious Chrome.exe process and click “Open File Location.”
- Check the location of the folder you’re taken to. If it’s: “C:\Program Files (x86)\Google\Chrome\Application,” (or similar) it’s unlikely you have a virus infection. If you’re taken anywhere else (such as a temporary folder, your Windows installation folders, or a Documents folder), chances are you have a virus infection.
- If you have a virus infection, you should scan your computer using a comprehensive antivirus scanner (like Norton).
Where is Chrome.exe located in Windows 10?
The default location for Chrome.exe in a 64-bit Windows 10 operating system is:
- C:\Program Files (x86)\Google\Chrome\Application\chrome.exe.
If your operating system isn’t 64-bit, you should look in:
- C:\Program Files\Google\Chrome\Application\chrome.exe.
If you suspect you have the Chrome.exe virus, don’t manually delete the .exe file in the mentioned directory. Chrome can’t work without it. If you find Chrome.exe in the specified directories, it’s likely your legitimate Google Chrome installation and not malware.
If you suspect you have a virus (even if you find Google Chrome in the above location), you should run a malware scan using a comprehensive antivirus program like Norton. To do this, download and install your chosen antivirus program on your device and follow our above steps.
How to remove the Chrome.exe virus?
The best way to remove the Chrome.exe virus is to download a comprehensive antivirus program like Norton and follow our above steps. However, before you do this, you need to check if your version of Chrome.exe is legitimate or a virus. To do this, check to see if it’s installed in C:\Program Files (x86)\Google\Chrome\Application\chrome.exe. If it is, it’s unlikely to be a virus. However, if you have any doubts, it doesn’t hurt to run a virus scan anyway.