
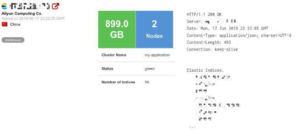
Safety Detectives’ research team has recently discovered a sizeable data leak (over 899gb and growing by the day) of a China-based server, which has now been closed. We are unable to confirm the company behind the leak, but according to the data, it appears to most likely be a marketing agency for mobile apps. The provider of the server is Aliyun Computing Co., but they only rented the server to the company and are not otherwise involved or responsible for the leak.
What’s Being Leaked?
Led by Head of Research, Anurag Sen, our security research team has discovered a veritable treasure trove of data. With what seems to be data of more than 100 mostly loan-related apps, this is no insignificant breach of trust for the users of said applications. The Elastic server exposed publicly sensitive information of Chinese citizens.

A simple search finds us credit evaluation reports, which contain:
- Loan records and details
- Risk management data
- Real ID numbers
- Personal details
- Name
- Address
- Contact number

Our team also found:
- Device data – over 4.6 million unique entries
- GPS location
- Detailed list of contacts
- SMS logs
- IMSI numbers
- IMEI numbers
- Device model/version
- Stored app data
- Memory data
- Operator reports
- Transaction details
- Mobile billing invoices
- Full names
- Phone numbers
- Bill amount per month
- Call log
- Credit and debit card details
- Concentrated list of apps on each mobile device
- Detailed tracking of app behavior
- Device information
- Device location
- Launch & exit times
- Duration on the content, etc.
- Passwords with MD5 encryption, which can be decoded

In the database, the data tells us that people’s activity is being tracked, in detail. Things including a user’s IP address and duration of a given activity, call logs, SMS exchanges (including content of the SMS), and the various apps installed on the devices are all within the scope of data made available by this leak. This is not only great for marketers to know everything to hyper-target their audience and fine-tune their message, it could also be easily used in either ‘friendly’ government spying or not-so-friendly espionage.
The loan records are viewable in detail, as well as risk management IDs, organization IDs, real government-issued ID numbers, and P2P activity (may represent loans between parties). This is information that could negatively impact future loan applications, career opportunities, and more.
Mobile phone account details are often more than enough to learn everything you need to know about a person. Names, phone numbers, billing amounts, call logs, and service provider can leave even security experts vulnerable.
There are more than enough details to entirely overtake someone’s identity without any significant effort whatsoever. If this data were to be sold on the Dark Web, it could easily be packaged into a ‘deal’ where an individual’s financial, medical, and personal life are up for grabs. When targeted, even a phone’s sim card can be replicated and nearly full access to all of a person’s phone apps that control smart home devices, contain private photos and details, and more is made available.

Preventing Data Exposure
How can you prevent your personal information from being exposed in a data leak and ensure that you’re not a victim of attacks if it is leaked?
- Be cautious of what information you give out and to whom
- Check that the website you’re on is secure (look for https and/or a closed lock).
- Only give out what you feel confident cannot be used against you (avoid government ID numbers, personal preferences that may cause you trouble if made public, etc.).
- Create secure passwords by combining letters, numbers, and symbols
- Do not click links in emails unless you are sure that the sender is legitimately who they represent themselves to be
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust
- Avoid using credit card information and typing out passwords over unsecure WiFi networks
- Find out more about what constitutes cybercrime, the best tips to prevent phishing attacks, and how to avoid ransomware.
About Us
SafetyDetectives.com is the world’s largest antivirus review website. The Safety Detectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats, while educating organizations on protecting their users’ data.
Published on: Jul 17, 2019