
An active Australian sports fan site with over 100,000 members has leaked a large volume of private data.
Our security team discovered multiple instances of personal private information made available to the public within the compromised server operated by BigFooty.com’s parent company Big Interest Group LLC.
Led by Anurag Sen, our team discovered around 132GB of data from an Elasticsearch database including private user data and technical information relating to the company’s web and mobile sites.
The leak included data from the site’s forum such as public posts as well as private messages between users.
A proportion of the data found on the server related to anonymous users and did not include private information attributable to real people.
However, some of the messages contain explicit and what could be described as hateful, racist and offensive material that could be attributed to various users including their true identities.
We reached out to BigFooty but as they didn’t get back to us, we decided to reach out to Amazon aws the service provider and the Australian Cyber Security Centre as well to make sure it can be secured quickly.
The Australian Cyber Security Centre was quick to reply and it seems that their intervention has been very helpful, as the servers were closed when we checked again later.
Who is Big Footy.com?
BigFooty.com is an Australian web site and mobile phone application focusing on Australian rules football — a variety of football common only to Australia. The site allows users to interact with each other on a range of topics with football being the prime focus for most users.
The site is owned and operated by parent company Big Interest Group LLC, who claims it operates “a variety of interest verticals” including multiple sports sites (e.g. BigCricket.com), which it has been doing so for over 14 years.
The site contains a login function and offers access to forums, statistics and miscellaneous features such as third-party blogs aimed at boosting user numbers.
Overall, the site acts like a social portal which means many of the interactions on the site go beyond football-related topics.
What was leaked?
Given the fact that BigFooty.com is a predominantly anonymous user site, participants cannot always be identified but some sensitive things are indeed shared in messages. Namely:
- Usernames used to access Big.Footy.com
- Passwords to live streams
- Data relating to ad spammers
- Email addresses
- Relationships between users
- Mobile phone numbers
- User comments including personal threats and racist material
- Personal information relating to real-world activities, intentions and behaviour
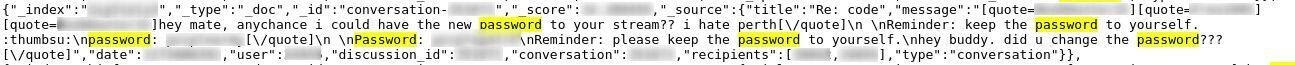
Password information relating to both accounts and streams hosted by BigFooty.com

Other data was also discovered that related to the site’s internal workings, namely:
- Server information
- Operating system information
- Internal resource details
- Browser information
- Error logs
- Access logs
- IP addresses
- GPS/location data
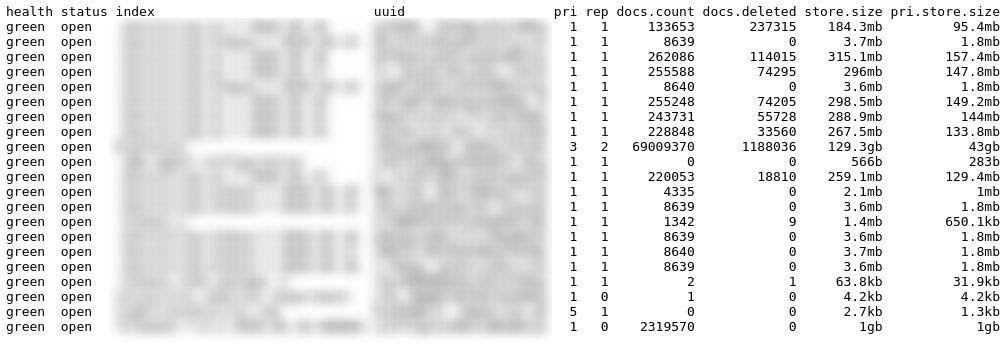
Server information is showing including server status, document counts and storage capacity of various server applications.
Although many user messages were available publicly, whether or not users could be identified depends on the data they shared in their correspondence. Many users shared mobile phone numbers, passwords to access other content and highly sensitive information relating to private activities
Data breach impact
From the technical server data and the large number of user correspondence discovered, multiple negative outcomes are made more likely.
Private messages are fully exposed in the leak and can be traced back to specific users. This includes some high-profile users such as Australian police officers and government employees. Private information belonging to such individuals, including chat transcripts and email addresses, were found on the database which thereby creates a significant vulnerability in terms of potential blackmail and other reputational damage that could be caused.
Furthermore, user activity is extremely varied with some users posted benign comments about football and popular culture, whereas multiple others, posted highly sensitive toxic material such as offensive comments, racism and threats. Sensitive material of this nature exposes those users to blackmail and coercion by malicious hackers, assuming their identity can be determined. In BigFooty’s case, several users that posted sensitive material could be identified.
Technical server data and user conversations could be leveraged to obtain further information and, therefore, empower malicious hackers to compromise the server and its users.
Even though usernames, passwords and identities were not always matched, there remains a significant risk that the titbits of information available could be used to commit identity fraud, and consequently, create financial, social and reputational damage on users.
A further issue — and one that is common with data leaks in general — is users sharing passwords to other platforms, or, reusing the same username and password on multiple platforms.
This user-generated vulnerability was evident in the BigFooty.com leak with several users sharing passwords which raises the chance of account takeover and more personal data being exposed to malicious hackers.
In terms of website vulnerability, by compromising BigFooty’s server, hackers obtain data that could help compromise other sister sites such as BigCricket.com.
Preventing Data Exposure
How can you prevent your personal information from being exposed in a data leak and ensure that you are not a victim of attacks – cyber or real-world – if it is leaked?
- Be cautious of what information you give out and to whom
- Check that the website you are on is secure (look for https and/or a closed lock)
- Only give out what you feel confident cannot be used against you (avoid government ID numbers, personal preferences that may cause you trouble if made public, etc.)
- Create secure passwords by combining letters, numbers, and symbols
- Do not click links in emails unless you are sure that the sender is legitimately who they represent themselves to be
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust
- Avoid using credit card information and typing out passwords over unsecured Wi-Fi networks
- Find out more about what constitutes cybercrime, the best tips to prevent phishing attacks, and how to avoid ransomware
About Us
is the world’s largest antivirus review website.
The Safety Detective research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on how to protect their users’ data.
Published on: May 29, 2020