
Updated on: April 26, 2024
Short on time? Here’s how to use the Tor browser safely:
- 1. Get a Tor-friendly VPN and connect to one of its servers. I recommend ExpressVPN, as it allows Tor traffic on all of its servers in 105 countries, has industry-leading security and privacy features, and provides fast speeds while using Tor.
- 2. Download and install the Tor browser. Make sure to only download it from Tor’s official site, otherwise you might accidentally download malicious files.
- 3. Open the Tor browser. Wait for it to connect to the Tor network — this could take up to 10 seconds or more, depending on how fast your internet is and how overloaded the Tor network is.
- 4. Surf the web. You can now use the Tor browser to securely access any website you want, including dark web sites.
The Tor browser is a popular way for internet users to visit dark web sites. It also provides some level of privacy and might also allow people in restrictive countries to access the free internet.
That said, the Tor browser also has some security issues, so it can’t 100% protect users’ privacy. Plus, some people still don’t know how to get and use the Tor browser, despite it being pretty accessible and user-friendly.
So I put together this guide to show you how to use the Tor browser and also stay safe while doing it — in this article, I’ll provide step-by-step instructions on how to install the Tor browser and surf the web with it, address Tor’s security issues, give you tips on how to safely use Tor, and more.
Secure Your Tor Traffic with ExpressVPN
While Tor is legal in most countries, it can also be used for illegal purposes. We strongly recommend researching your local laws to make sure it’s perfectly legal to use Tor and to only use it to access legal content.
Editors' Note: Intego, Private Internet Access, CyberGhost and ExpressVPN are owned by Kape Technologies, our parent company
How to Set Up & Use the Tor Browser
1. Download & Install the Tor Browser
Start by downloading the Tor browser from Tor’s official site. I strongly recommend avoiding unofficial sources, as you risk downloading malicious software.
The browser is available on Android, Windows, macOS, and Linux — on iOS, only the Onion Browser is available, which is a good alternative but doesn’t offer as much privacy as the Tor browser. For this guide, I used the Tor browser on Windows 10.
Next, open the installer and follow its instructions — installing the Tor browser won’t take more than 2 minutes.
2. Open the Tor Browser
Next, open the Tor browser app and wait for it to connect to the Tor network — this usually takes 5–10 seconds depending on how fast your internet connection is and how overloaded the Tor network is.
3. Connect to a Site
You can now start surfing the web while connected to the Tor network. Access any site you want as you normally would on your regular browsers. Just keep in mind it might take a bit longer to connect to a site due to Tor’s slow speeds.
If you want to surf .onion sites, see our list of the best dark web sites in 2024.
4. (Optional) Change the Tor Exit Server
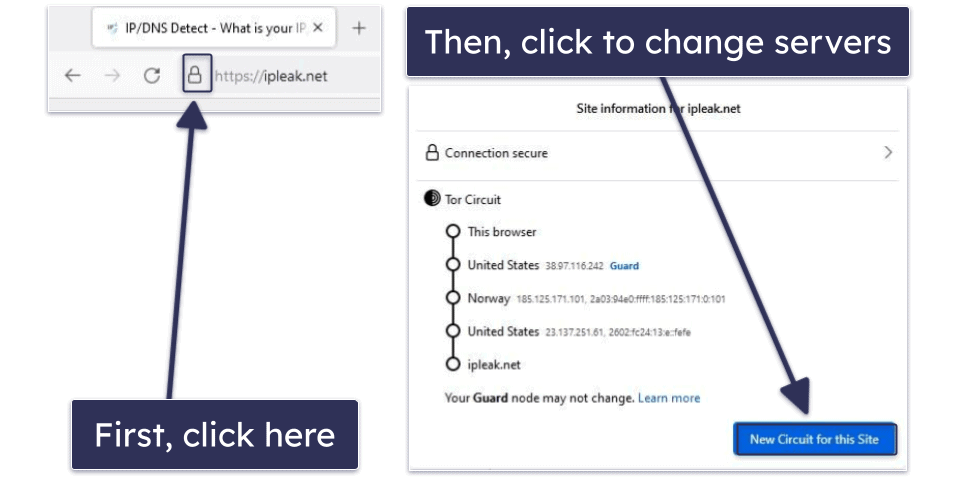
You can change the IP address the Tor network assigned to you by connecting to different servers — to do that, first click the padlock icon next to the site’s URL bar. Next, hit the New Circuit for This Site button to connect to a different server chain. Repeat this process until you get an IP address from your desired country.
Is it Safe to Use Tor?
Tor generally provides good security and privacy, but it also has certain limitations and security issues:
- The guard server can see your IP address. The first Tor server you connect to can see your real IP address, which reveals your location. This is terrible for your privacy.
- Opening documents downloaded through Tor is risky. Certain documents (like PDF files) might contain internet resources that are downloaded outside of the Tor browser — this can cause your real IP address to be exposed.
- Tor doesn’t encrypt all of your device’s traffic. The Tor network only provides privacy as long as you use the Tor browser — if you access a site using a different browser, your IP address and data will be exposed.
- Malicious actors can run Tor servers. Pretty much anyone can run Tor servers, including hackers. Interacting with malicious Tor servers could severely compromise your privacy.
- Tor exit servers can see unencrypted traffic. If you use Tor to access HTTP websites (many dark web sites lack HTTPS), the exit server will be able to monitor your unencrypted traffic. If malicious actors are running the server, they can steal sensitive data like logins and cryptocurrency seed phrases.
- Tor has previously leaked user IP addresses. The Tor network has suffered various security issues in the past, which caused user IP addresses to leak, revealing users’ real locations. Those issues have been fixed, but there’s no telling when other similar security problems might pop up.
- Tor receives a lot of funding from US government agencies. This doesn’t mean the US government controls Tor, but it makes it hard to fully trust Tor with protecting my privacy — after all, there’s no way to know if government authorities are operating Tor servers or not.
- There are tons of malicious Tor websites. If you use Tor to access dark web sites, you’re at risk of accidentally accessing malicious sites that could infect your device with malware or use scripts to compromise your privacy.
All in all, Tor provides decent security and privacy, but it’s best to take precautions when using it — like using a VPN (such as ExpressVPN) to first secure your traffic before connecting to the Tor network.
How to Stay Safe While Using Tor
- Use a VPN. VPNs are online apps that change your IP address and encrypt your traffic, and I strongly recommend connecting to a VPN before you use the Tor browser — that way, your data will be secured before it reaches the Tor network. Only use a VPN that comes with essential security features, like 256-bit AES encryption, a kill switch to prevent traffic leaks, IPv6, DNS, or WebRTC leak protection, and a no-logs policy to prevent the VPN from logging your data. In my opinion, ExpressVPN is the best VPN for accessing the Tor network.
- Use an antivirus. You’re likely to encounter malicious links and content on clearnet sites, so the odds of encountering them on dark web sites are even higher. That’s why I recommend using Tor with an antivirus, which is a program that can protect your device from malware infections and malicious sites — the best antivirus on the market at the moment is Norton 360.
- Upgrade Tor’s security levels. By default, the Tor browser’s security level is set to Standard, which enables all website features. If you switch it to Safer, the browser will automatically disable website features that can be abused to endanger your privacy, like certain fonts and math symbols. And the Safest option disables even more site features — like JavaScript, which hackers could use to access sensitive information you shared with different sites (such as passwords).
- Use privacy-friendly search engines. Most Tor users recommend using DuckDuckGo or Startpage instead of Google, as they provide more privacy. Also, if you want to look up .onion links, I recommend using Ahmia — on top of being very accurate, it also blacklists sites that host abusive content.
- Don’t access HTTP sites. If you use Tor to connect to HTTP websites, the exit servers can see your unencrypted traffic — if malicious actors are operating them, they can steal sensitive data from you. So you should only connect to HTTPS websites.
- Only access safe dark web sites. If you’re using Tor to access .onion links, I strongly recommend only sticking to legit sites that are safe to use, as many shady sites could compromise your privacy and infect your device with malware.
- Don’t use personal information. If you interact with dark web sites that require you to enter your name or email address, I recommend using a fake name and a secure email service (like ProtonMail) instead — otherwise, malicious actors might collect your personal data and use it to target you with cyber attacks and scams.
- Pay in cryptocurrencies. If you plan to purchase anything on the dark web (which I strongly recommend not doing), you should always use cryptocurrencies instead of credit/debit cards — they provide better privacy, and there’s no risk that malicious actors will compromise your payment information.
Why Would You Want to Use the Tor Browser?
1. Enjoy Better Privacy
The Tor browser lets you access the Tor network, which hides your traffic and IP address — in addition, the Tor browser allows users to optionally disable website features that might compromise their privacy, although that might prevent some sites from working properly.
The Tor browser also prevents browser fingerprinting (the collection of data about a device or service) to a certain extent.
All of that allows internet users to enjoy a higher level of privacy when surfing the web. This way, websites and advertisers can’t track their location, device information, and online preferences.
2. Circumvent Censorship
The Tor browser allows people in restrictive countries to visit blocked online services, such as social media apps, news websites, media outlets, entertainment sites, and more. Tor does that by allowing people to communicate with the internet through its servers, whose IP addresses don’t have firewall restrictions linked to them.
3. Visit Dark Web Sites
Some online users use the Tor browser to browse dark web sites that use .onion links, which are not available on the clearnet (the publicly accessible internet). There are tons of interesting dark web sites you can browse, including search engines, chatrooms, news sites, and even well-known platforms like Facebook.
4. Share Sensitive Information
Political activists, whistleblowers, and journalists often use the Tor browser to share information with trusted sources and protect their privacy and the privacy of their sources in the process. They use the Tor network to receive anonymous tips, investigate controversial topics, and access information that’s not available on the clearnet.
5. Run Security Tests
IT staff might use the Tor network to run security tests, such as penetration testing — this involves performing an authorized cyberattack on a computer system or web application to test how secure it is.
Many hackers rely on Tor when performing cyberattacks, which is why it’s often used in security tests. Running security tests using Tor allows businesses to better protect their data against threats from the dark web.
6. Ask for Medical Advice
Some people use the Tor browser to discuss their health problems with doctors over the Tor network. They likely do this because they want extra privacy and because they’re not comfortable discussing their health issues with medical professionals face-to-face. Also, people who can’t afford to visit a doctor or visit a clinic might use this approach as well.
7. Perform Undercover Operations
Law enforcement agents often use Tor to go undercover on the dark web, so that they can investigate and catch people who engage in illegal activities — like drug trafficking, selling illegal firearms, credit card fraud, and more.
How Does the Tor Browser Work (& Keep You Anonymous Online)?
The Tor browser is a web browser that lets you access the Tor network. The browser is free to download and use, and it’s also open-source, so anyone can audit the code for security vulnerabilities.
The Tor network is a privacy network that encrypts your traffic multiple times, making it completely unreadable. When you use the Tor network to access a site, your traffic is routed through at least 3 Tor servers, which are also called “relays” or “nodes,” and are usually run by volunteers. Here’s a quick sketch of how a Tor connection looks:
Your Device → Tor Browser → Internet → Tor Server #1 → Tor Server #2 → Tor Server #3 → Website
There are 4 types of Tor servers:
- Guard servers — The first Tor server your connection goes through.
- Middle servers — The Tor server that routes your traffic between the first and last Tor servers.
- Exit servers — The last Tor server your connection goes through before reaching its destination (like a website, for example).
- Bridge servers — Tor servers whose IP addresses are not made public (unlike the other types of Tor servers). These servers are intended to help people in restrictive countries circumvent censorship.
As well as encrypting your traffic, the Tor network changes your IP address — any site you access through Tor will only see the IP address of the exit Tor server, while your real IP address will remain hidden.
What’s the Difference Between the Tor Browser and a VPN?
The Tor browser is a free, open-source web browser that lets you access the Tor privacy network. When you use the Tor browser, it changes your IP address and encrypts your traffic at least 3 times. The Tor browser also lets you access dark web sites, which are not available on the clearnet.
The Tor browser is mostly used to surf the dark web or evade censorship. You can also use it to enjoy better privacy online, but I honestly think a VPN is better suited for that. And you would also benefit from it if you’re a journalist, whistleblower, or activist that needs to share sensitive data with their sources, or if you’re an undercover agent.
A VPN is an online app that also changes your IP address and encrypts your traffic — but it only does it once, which allows VPNs to provide much faster speeds than Tor. To secure your data with a VPN, you use a VPN app (also called a VPN client) to connect to a VPN server. Once connected, the server will route and encrypt all of your internet traffic. Most top VPNs have paid subscriptions, but there are also a few providers that have good free plans that let you test their services. And unlike the Tor browser that only secures the traffic that passes through it, a VPN secures all of your device’s web traffic.
Pretty much anyone stands to benefit from using a VPN. It provides great privacy and security, is good for secure streaming, torrenting, and gaming. And because VPNs encrypt your traffic but are much faster than Tor, they’re also good for bypassing bandwidth throttling. Whistleblowers, journalists, and anyone else who needs to share sensitive data can also use a VPN to protect their traffic — even better, they can use it together with the Tor browser for added privacy and security.
Tor Over VPN vs. VPN Over Tor — Which Is Safer?
Tor over VPN is when you route Tor traffic over a VPN connection, so you first connect to a VPN server, and then use the Tor browser to connect to the Tor network.
Routing your VPN traffic through a Tor connection is referred to as VPN over Tor. Essentially, you initiate a connection with the Tor network via the Tor browser first, followed by a connection to a VPN server.
For the utmost privacy and security, combine Tor with a VPN connection. This encrypts your online traffic before entering the Tor network and shields your actual IP address. In case of a leak, only the VPN’s IP address will be exposed.
VPN over Tor connections are pretty bad for your privacy — the first Tor server will always see your real IP address, so if a malicious actor is using it they can collect your IP and use it to track your location. And anyone (including your ISP) can see that you’re connected to Tor. What’s more, it’s also hard to establish a VPN over Tor connection, as most VPN providers don’t support them. And even if you find a VPN that does, you’ll still need to perform a manual setup, which is inconvenient and time-consuming.
Frequently Asked Questions
Is it safe to download the Tor browser?
Yes, but only as long as you download it from official sources, like Tor’s official website. Otherwise, you risk downloading fake apps that might infect your device with malware.
That said, using the Tor browser is not 100% safe, as the Tor network has a few security issues. That’s why I strongly recommend using a VPN together with Tor to protect your privacy.
Does the Tor browser hide your IP address?
Yes, but only from the sites you connect to — instead of your IP address, they will only see the IP address of a Tor server.
However, the first Tor server you connect to can see your real IP address — if a malicious actor operates it, they could collect it and use it to track your location or online behavior.
That’s why I recommend using a VPN before you access Tor, as it will prevent any Tor server from seeing your real IP address.
Does the Tor browser work on iOS?
No, but Tor devs recommend using the Onion Browser app as an alternative. It works well, it’s free, and it provides decent privacy since it’s open-source.
However, it can’t provide the same level of privacy as the Tor browser due to how the iOS operating system works — it forces the Onion Browser app to use Apple’s WebKit browser engine instead of Mozilla Firefox’s Gecko browser engine, which is used by the Tor browser and can provide better anti-tracking functionality.
Does the Tor browser slow down your speeds?
Yes — I performed 10+ speed tests with Tor, and it always slowed down my original speeds by 98–99%, which is a lot. It usually took up to 5–10 seconds for most websites to load.
Tor’s speeds are really slow because it encrypts your traffic multiple times. Each layer of encryption increases the time it takes for data to travel between your device, Tor’s servers, and the sites you visit.
Can you use the Tor browser for torrenting?
No, as the Tor network is not good for torrenting — some Tor browsers block P2P traffic, and even Tor’s developers ask users not to use the network for P2P downloads. That’s because Tor’s speeds are pretty slow and its bandwidth is limited, so torrenting over Tor will cause even more slowdowns. Plus, I don’t think that torrenting over Tor is secure, as some Tor servers can see your IP address, which is terrible for your privacy.
Instead, I recommend using a VPN for torrenting, as you get much better P2P speeds, security, and privacy — ExpressVPN is my top pick for torrenting, as it allows P2P downloads on servers in 105 countries, has the fastest torrenting speeds out there, and provides excellent security and privacy features.
Is the Tor browser different from a VPN?
Yes — the Tor browser and a VPN are similar, but there are some differences between them. The Tor browser is a web browser that connects you to the Tor network, which changes your IP address and encrypts your traffic at least 3 times. A VPN is an online app that lets you connect to VPN servers to change your IP address and encrypt your traffic (usually just once). Also, the Tor browser is free and open-source. On the other hand, most VPNs have paid plans and only some providers have free plans, and only a few VPNs come with open-source apps.
I personally think the Tor browser is only good for surfing dark web links, while VPNs have many more use cases — they’re great for streaming, torrenting, gaming, and bypassing censorship. And while both Tor and VPNs provide security and privacy, I think VPNs are better because Tor has some security issues. What’s more, VPNs are much faster than Tor, and this also allows them to help you prevent bandwidth throttling.
Tor over VPN or VPN over Tor — which is better?
Tor over VPN connections are much safer than VPN over Tor connections, and easier to use too — they prevent Tor servers from seeing your real IP address, stop anyone from seeing you’re using Tor, and they protect your real IP address if Tor suffers a leak. Plus, most top VPNs (like ExpressVPN) support Tor traffic on their servers.
However, VPN over Tor connections provide poor privacy, as Tor servers can collect your real IP address. What’s more, anyone can see you’re using the Tor network. And very few VPNs support VPN over Tor connections — and the ones that do require you to perform an inconvenient manual setup.